Security Engines - Smart-Phish (Anti-Phishing)
The Smart-Phish (Anti-Phishing) security engine is responsible for detecting phishing, suspected phishing, and spam emails. It analyzes various components of an email, such as attachments, links, sender reputation, domain analysis, OCR, URLs behind QR code, and many more.
The Smart-Phish engine detects phishing in emails in all languages. Language-based detections are supported for languages, as mentioned in Supported Languages for Anti-Phishing.
Phishing Confidence Level (Threshold)
The Anti-Phishing algorithm returns a verdict on each email analyzed with confidence that may go from Lowest to Highest.
Any email categorized as phishing with a confidence level equal to or greater than the phishing confidence level (threshold) generates a Phishing event and triggers the relevant workflow.
Any email categorized as phishing with a confidence level below the defined phishing confidence level (threshold) generates a Suspected Phishing event and and triggers the relevant workflow.
For example, if the phishing confidence level (threshold) is High and if the Anti-Phishing engine categorized an email as phishing with phishing confidence level (threshold) as Medium, it triggers the Suspected Phishing workflow.
By default, the phishing confidence level (threshold) is set to High.
To configure the phishing confidence level (threshold):
- Go to Security Settings > Security Engines.
- Click Configure for Smart-Phish.
- Under Phishing confidence level, select the required threshold.
- Click Save.
Nickname Impersonation
For more details about Nickname Impersonation, see Nickname Impersonation.
Phishing Simulation Solutions
Many organizations use phishing simulation solutions to educate their employees on how to detect and report phishing attacks. These solutions send fake phishing emails to employees to try and trick them into performing actions, opening attachments, or clicking on phishing URLs.
Avanan automatically detects such emails from commonly-used phishing simulation solutions and does not mark them as phishing. Phishing reports from users regarding those emails will be automatically declined.
Avanan Portal supports phishing simulation solutions from ActiveTrail, BenchMark, CybeReady, HubSpot, Infosec IQ, KnowBe4, MailChimp, MailGun, MailJet, MimeCast, Phished, PhishMe, ProofPoint, SendGrid, SendInBlue, Sophos Phish Threat V2, TargetHero, TerraNova, and ZoHo.
If you are using a different phishing simulation solution:
- To avoid detection of phishing simulation emails, add an Anti-Phishing Allow-List rule based on the solution's IP address.
For information about adding an Allow-List, see Anti-Phishing Exceptions. - To request for supporting the phishing simulation solution, contact Avanan Support.
- To automatically decline end-users' phishing reports regarding phishing simulation emails, contact Avanan Support.
To configure the Avanan Portal to automatically send feedback to users who reported phishing training emails as phishing:
- Access the Avanan Portal.
- Click Security Settings > User Interaction > Phishing Reports.
- In the Phishing simulation emails section, select the Notify user checkbox.
- (Optional) To change the default text in the feedback:
- Click the cog icon next to Notify user checkbox.
The Configure Auto-Reply to Users Reporting Phishing Simulation Emails pop-up appears.
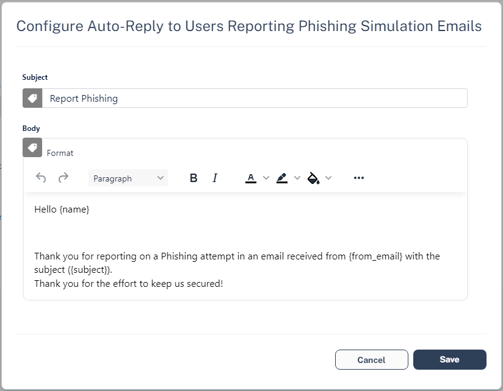
- Make the necessary changes and click Save.
- Click the cog icon next to Notify user checkbox.
- Click Save and Apply.
For Office 365, to see user-reported phishing reports from phishing simulation solutions, see Integration with End-user Phishing Reports.
Upstream Message Transfer Agents (MTAs)
During Learning Mode, to improve the accuracy of the Anti-Phishing engine, Avanan automatically detects MTAs that process emails before they reach Microsoft/Google.
If there are other MTAs that are not detected by Avanan, you can add them manually.
To add MTAs manually:
- Go to Security Settings > Security Engines.
- Click Configure for Anti-Phishing.
- Scroll-down to SMTP host/s acting as Mail Transfer Agent/s (MTA) and enter the full DNS names or IP addresses of MTAs separated by comma.
- Click Save.
Blocking Emails that Fail DMARC
Some organizations configure their DMARC (Domain-based Message Authentication, Reporting and Conformance) record to quarantine or reject emails that fail DMARC checks. Most organizations choose to enforce this rejection for incoming emails with Microsoft/Google.
If you wish to enforce it with Avanan, you may configure to trigger the Suspected Phishing or Phishing workflow for emails that fail DMARC checks.
By default, No extra action is selected for DMARC failed emails in the Anti-Phishing security engine.
To configure the workflow for DMARC failed emails with Quarantine or Reject action:
- Sign in to the Avanan Portal.
- Navigate to Security Settings > Security Engines.
- Click Configure for Smart-Phish (Anti-Phishing).
- Scroll-down to When emails fail DMARC with action reject/quarantine section and select one of
these.- No extra action - Enforces no extra action.
- Trigger 'Suspected Phishing' workflow - Enforces the Suspected Phishing workflow configured in the threat detection policy.
- Trigger 'Phishing' workflow - Enforces the Phishing workflow configured in the threat detection policy.
- Click Save.
Warning - If incoming emails go through a secure email gateway (SEG) before reaching Microsoft/Google, then Microsoft/Google might flag these emails as DMARC violation because the email comes in from the SEG, whose IP might not be authorized in the SPF/DMARC records.
In such cases, selecting to trigger Suspected Phishing or Phishing workflow might result in a high number of false positives and might impact email delivery.
Make sure the DMARC record is configured properly before selecting these workflows.
Impersonation of your Partners
Avanan lists all your partners in the Partner Risk Assessment dashboard.
When a sender from a newly registered domain sends an email to your organization, the Smart-Phish (Anti-Phishing) engine checks if the sender domain resembles your partner domain(s). By default, if such a domain similarity is detected, it is considered an indicator in the AI-based Anti-Phishing security engine. It might or might not yield a Phishing verdict.
Partner Impersonation Attacks - Workflow
Administrators can select to override the AI-based verdict of the Anti-Phishing security engine and trigger a specific workflow when such a similarity is detected.
To configure a specific workflow for emails from domains that resemble a partner domain:
- Go to Security Settings > Security Engines.
- Click Configure for Smart-Phish.
- Scroll down to When the sender domain resembles the domain of a partner section and select one of these workflows.
- Consider as an indicator in the standard Anti-Phishing inspection (Default)
- Trigger Suspected Phishing workflow
- Trigger Phishing workflow
- Click Save.
Handing Secured (Encrypted) Emails
Administrators can select how to manage incoming encrypted emails for end users, including Microsoft RPMSG and Microsoft 365 Message Encryption, and so on.
To view the content of the encrypted emails, the end users must click the link provided in the email and authenticate.
To configure workflow for secured (encrypted) emails:
- Click Security Settings > Security Engines.
- Click Configure for Anti-Phishing.
- Scroll down to the Secured encrypted emails section and select a workflow.
- Do not trigger any phishing workflow
- Trigger Suspected Phishing workflow for recurring first time senders
- Trigger Suspected Phishing workflow for first time senders
- Trigger Suspected Phishing workflow
- Trigger Phishing workflow for recurring first time senders
- Trigger Phishing workflow for first time senders
- Trigger Phishing workflow
Note - Recurring first-time senders are senders identified as sending multiple emails where they are considered first-time senders, across all Check Point customers.
- Click Save.
Preventing Email Bomb Attacks
An Email Bomb is a social engineering attack that overwhelms inboxes with unwanted emails. Usually, subscription confirmations to newsletters the users never signed up for.
Users targeted by these attacks lose access to their business emails, and the attackers may even use this as a distraction while performing malicious activities on the user's behalf.
To prevent such attacks, administrators must configure these in the Avanan portal:
- Conditions for detecting and handling an ongoing Email Bomb attack.
- Workflow to be triggered when such an attack is detected.
Identifying an Email Bomb Attack
Avanan identifies an Email Bomb attack when the number of emails from new senders exceeds a defined threshold in a common attack timeframe.
Note - The attack timeframe is dynamic and changes depending on the Avanan security analyst's judgement. It is usually a couple of hours.
To configure the Email Bomb attack threshold:
- Go to Security Settings > Security Engines.
- Click Configure for Smart-Phish.
- Scroll down to Email Bomb – Threshold and enter the threshold value.
- Click Save.
Once the number of emails from new senders in the common attack timeframe exceeds the threshold, Avanan treats all subsequent emails from any new sender as part of the attack. This continues until the attack timeframe passes without the number of emails from new senders going over the threshold.
For example, if an administrator configured the Email Bomb threshold as 50, Avanan counts emails 51 and above as part of the attack.
Handling Emails of an Email Bomb Attack
By default, when Avanan detects an Email Bomb attack, it individually evaluates every email part of the attack for Spam and Phishing. Administrators can configure a dedicated workflow for these emails.
To configure the workflow for Email Bomb attack:
- Go to Security Settings > Security Engines.
- Click Configure for Smart-Phish.
- Scroll down to Email Bomb – Workflow and select the required workflow.
- Evaluate each email separately for spam/phishing
- Trigger Spam workflow
- Trigger Suspected Phishing workflow
- Trigger Phishing workflow
- Click Save.
Spam Protection Settings
Spam Confidence Level
Any email categorized as spam with a confidence level equal to or greater than the spam confidence level (threshold) generates a Spam event and triggers the relevant workflow.
To configure the spam confidence level (threshold):
- Go to Security Settings > Security Engines.
- Click Configure for Anti-Phishing.
- Scroll down to the Spam confidence level section and select the required threshold.
- Lowest
- Low
- Medium
- High
- Highest
Note - Low confidence levels could result in a high number of false positives.
- Click Save.
Treating Marketing Emails as Spam
- Go to Security Settings > Security Engines.
- Click Configure for Anti-Phishing.
- To treat the marketing emails as spam, scroll down to the Spam confidence level section and select the Treat marketing emails as spam checkbox.
Note - Selecting this option flags all the marketing emails as spam and triggers the configured Spam workflow. For more information, see Spam workflows.
Detecting Malicious QR Codes
The Smart-Phish (Anti-Phishing) security engine analyzes the links behind the QR codes and reports the malicious links, if any. To view the links behind QR codes, open the Email Profile page and scroll down to the Link analysis section.
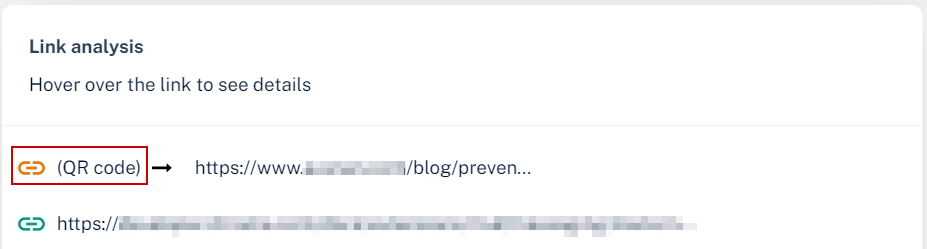
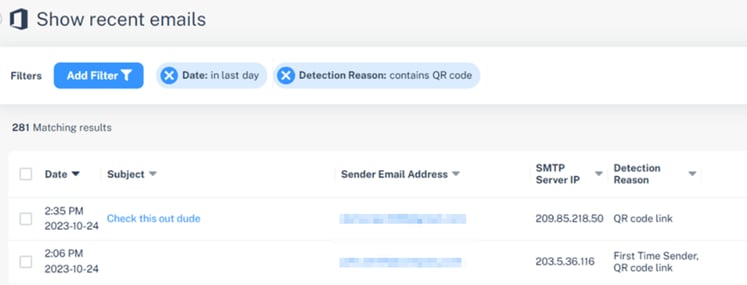
Filtering Emails Containing QR Codes
Using the Detection reason as QR in Custom Queries, the administrators can filter emails with malicious QR codes. For more information, see Custom Queries.
Reviewing Phishing Events
Phishing events are triggered by the Smart-Phish and Click-Time Protection security engines.
The Smart-Phish security engine prevents the most sophisticated phishing and spam emails from being delivered to the end users' mailboxes.
The Click-Time Protection security engine re-writes the links in emails, emulates and checks the reputation of websites behind the links every time an end user clicks on them.
Acting on Phishing Events
To review and investigate the phishing event:
- To see reasons for the detection of an event as phishing, under Security Stack, click More Info for Smart-Phish.
- To investigate the header of the raw email, under Email Profile, click Show for Header from raw email.
- To investigate the body of the raw email, under Email Profile, click Show for Show body from raw email.
- To download the raw email, under Email Profile, click Download for Download this email.
- To send the original email to the end-user, under Email Profile, click Send for Send Original Email.
Note - This option appears only when there are links that were re-written by the Click-Time Protection security engine. - To recheck the email for phishing, under Email Profile, click Recheck for Recheck email.
To filter emails similar to the event generated:
- Under Security Stack, select Similar Emails / Create Rules.
- Under Filters, define the criteria for filtering the emails.
- Click Search.
Note - After filtering the emails, you can create Anti-Phishing Allow-List and Block-List. See Anti-Phishing Exceptions.
To report mis-classification of an event:
- Under Security Stack in the event profile, click Report mis-classification for Anti-Phishing.
- Under Report this email as, select how you want to classify the event:
- Legit Marketing Email
- Clean Email
- Spam
- Phishing
- Under How confident are you, select how confident you are about the classification you selected:
- Not so sure
- Medium confidence
- High confidence
- Click OK.
Post-delivery Email Recheck
Sometimes emails are rechecked after delivering to the end user mailbox, which may result in emails being removed from the user mailbox.
Post-delivery email recheck can be initiated in these cases:
- Recheck initiated by the inputs from the end users (reported phishing, malicious url clicks) and other sources.
- Emails are processed by the Anti-Phishing security engine and when needed by the Avanan security analysts.
- When a global block action is issued. The block action includes all emails that match the relevant match criteria, across all protected mailboxes.
- Emails processed by the relevant policy workflows.
When a policy is configured to block emails, the emails are removed from the mailbox and placed in quarantine. Avanan generates the relevant security events and sends email notifications.
Reviewing Malicious Links
Link Analysis card on the Email Profile page shows the reasons why Avanan flagged links and QR codes as malicious or not. It also shows a secure preview (image) of the link.
For information about the malicious QR codes, see Detecting Malicious QR codes.
To review and investigate the malicious links:
- Open the malicious event.
- Scroll-down to Link analysis.
- Hover over the link and click Analyze link.
The URL Sandbox pop-up appears.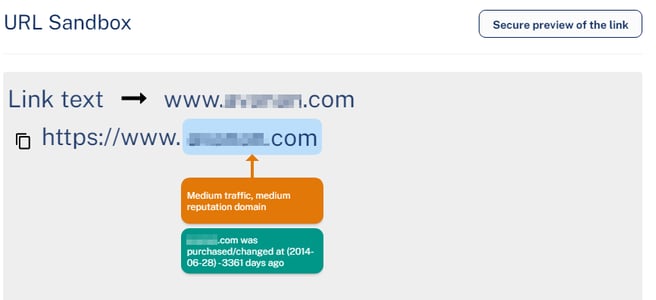
- To view the image of the link, click Secure preview of the link.
Anti-Phishing Exceptions