Security Engines - DLP (SmartDLP)
Avanan's Data Loss Prevention (DLP) engine safeguards the organization's data from breaches or unauthorized sharing. It scans emails, attachments, shared files, and text messages, even extracting text from images using OCR. The DLP engine identifies patterns that should not be shared with unauthorized people or destinations.
The DLP engine enables you to create universal policies across multiple cloud applications to control how files are shared amongst internal and external users. DLP identifies and marks files containing confidential, financial, and personally identifiable information, including credit card numbers, social security numbers, bank routing numbers, or data protected under HIPAA, etc.
Note - DLP is not available for Avanan Portal accounts residing in the United Arab Emirates (UAE) region. If required, you can request to enable DLP. However, sensitive data analysis will be performed in the United Kingdom (UK) and not within the borders of the UAE. If you wish to enable DLP, contact Avanan Support.
DLP Policies
This chapter discusses defining the DLP categories, Data Types, and other DLP security engine settings.
To enforce your organization’s DLP standards, you need to define DLP policies for different protected SaaS applications.
To configure the DLP policy, see the relevant SaaS application:
- Email Data Loss Prevention (DLP) Policy
- File Storage SaaS applications
- Messaging SaaS applications
DLP Categories
DLP categories are containers of multiple data types used in different DLP policies to describe data sharing that can be considered as a DLP violation and should trigger a DLP workflow.
For example, the PII DLP category includes the Passport Number DLP Data Type.
Managing DLP Categories
You can configure all the available DLP categories and manage them under Security Settings > Security Engines > SmartDLP.
Editing DLP Categories
To edit the list of DLP Data Types each category contains:
- Navigate to Security Settings > Security Engines.
- Click Configure for DLP.
- Scroll down to Detection Types and find the relevant DLP category.
- Add or remove data types from the category.
Note - To exclude Universal Air Travel Plan (UATP) card numbers from detecting as credit card numbers, under the PCI detection type, enable the Exclude UATP cards from the Credit Card data types checkbox. - Click Save.
For more information about the default DLP Data Types and their DLP categories, see DLP Built-in Data Types and Categories.
DLP Data Types
DLP Data Types describe the content the DLP engine tries to detect. Every time the engine detects a data type, it adds 1 to the hit count of every DLP category containing this data type.
Managing DLP Data Types
To view and manage the available Data Types, go to Security Settings > DLP Data Types.
Custom DLP Data Types
Avanan allows you to create custom DLP Data Types. These Data Types provide organizations the flexibility to add any DLP data type to each of the DLP categories.
Note - You must add the custom DLP Data Type to a DLP category before it is enforced.
Creating Custom DLP Data Types
Regular Expression DLP Data Types
Data Types based on regular expressions are data types that will add a hit count to their parent category every time a string in the inspected email/file/message is matched against the defined Regular Expression.
To create a regular expression Data Type:
- Navigate to Security Settings > DLP Data Types.
- Click Create Data Type.
Create Custom DLP Data Type section appears. - Enter the required Name and Description for the Data Type.
- Under Match type, select Regular Expression and enter the required regular expressions.
Note - Avanan supports Regular Expression 2 syntax. For more information about the syntax, see this article. - Click Save.
Dictionary DLP Data Types
A dictionary is a list of custom strings. These Data Types add a hit count to their parent category every time a string in the inspected email/file/message matches one of the strings in the dictionary.
To create a Dictionary DLP Data Type:
- Navigate to Security Settings > DLP Data Types.
- Click Create Data Type.
Create Custom DLP Data Type section appears. - Enter the required Name and Description for the Data Type.
- Under Match type, select Dictionary and add the required keywords:
- To add a keyword to the dictionary, enter the required keyword and click Add Keyword.
- To import keywords to the dictionary from a CSV file:
- Click Import dictionary.
- Under Upload Dictionary File, select the required CSV file.
- To override the existing keywords, enable the Override all existing words checkbox.
Note - To export the keywords in the dictionary to a CSV file, click Export dictionary.
- Click Save.
Compound DLP Rules
Compound DLP Rules are parent DLP rules that contain other child DLP rules, divided into two groups:
- Triggers – DLP rules that must match otherwise, the parent DLP rule will not match
-
Children – DLP rules that could match and add to the parent DLP rule hit count.
In addition, each Compound DLP Rule has a Minimum Match Type Count of its own so that the number of matches across all contained data types must be above it for the parent DLP Rule to match.
For example, you can create a compound DLP Rule named MyCompany Internal Documents the following way:
- Triggers
- A string “MyCompany”
- A string “Confidential”
- Children
- Source Code
- Bank Swift routing numbers
-
Minimum Match Type Count = 4
Example scenarios:
| Scenario | Findings | Match? | Reason | |||
| "My Company" | "Confidential" | Source Code | Bank SWIFT Routing Numbers | |||
| Only Triggers | 2 | 3 | 0 | 0 | Yes | All triggers plus match count above the threshold |
| Some Triggers | 3 | 0 | 2 | 2 | No | One of the triggers not matched |
| Not enough matches | 1 | 1 | 1 | 0 | No | Match count below the threshold |
| Triggers and Children | 1 | 1 | 2 | 2 | Yes | All triggers plus match count above the threshold |
Creating a Compound DLP Rule
Avanan allows you to define a custom Compound DLP Rule.
To create a compound DLP rule:
- Navigate to Security Settings > Security Engines.
- Click Configure for SmartDLP.
- Scroll down and find Compound Info Types.
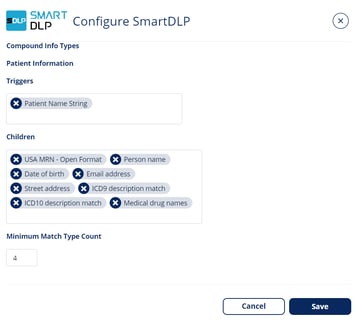
- Edit the Triggers, Children, and Minimum Match Type Count.
- Add Patient Information to one of the DLP Categories so that it can be used in the DLP policy rules. For more details, see DLP Built-in DLP Rules and Categories.
- Click Save.
Other Custom DLP Data Types
If you need a different custom data type, open a support ticket or contact Avanan Support.
Edit, Clone, or Delete Custom DLP Data Types
To edit a custom DLP Data Type:
-
Navigate to Security Settings > DLP Data Types.
-
Select a custom DLP Data Type.
-
Click on the vertical ellipses icon (in the top right corner of the selected custom DLP Data Type), and then select Edit.
-
Make the required changes to the DLP Data Type and click Save.
To clone a custom DLP Data Type:
-
Navigate to Security Settings > DLP Data Types.
-
Select a custom DLP Data Type.
-
Click on the vertical ellipses icon (in the top right corner of the selected custom DLP Data Type), and then select Clone.
-
Make the required changes to the DLP Data Type and click Save.
To delete a custom DLP Data Type:
-
Navigate to Security Settings > DLP Data Types.
-
Select a custom DLP Data Type.
-
Click on the vertical ellipses icon (in the top right corner of the selected custom DLP Data Type), and then select Delete.
-
Click OK.
Configuring Advanced Data Type Parameters
To refine the definitions of a DLP category or to handle cases of false-positive detections, you can control how to match a DLP Data Type in an email/file/message.
Match Hit Count Settings
By default, a DLP rule's hit count increases every time a string in the email/file/message matches with the DLP rule’s definitions. If the same matched string appears multiple times in the email/file/message, the hit count increases accordingly.
To configure Avanan to ignore duplications of the same string when calculating the hit count, check the Unique detections only box in the Configure DLP window.
Occurrence Threshold
By default, if a DLP rule is matched X times, the hit count of the DLP Category containing this DLP rule increases by X.
Setting the occurrence threshold for the DLP rule to Y means that:
- If the DLP rule matches < Y times, the hit count of the containing DLP Category will not be increased at all.
-
If the DLP rule matches >= Y times, the hit count of the containing DLP Category will be increased by the total number of matches.
To configure the Occurrence Threshold, open a support ticket or contact Avanan Support.
Likelihood Adjustment
By default, the DLP engine returns a specific likelihood level (Minimal Likelihood) to a DLP Category.
If you want to determine if one of the DLP Rules is matched, the likelihood will automatically increase or decrease. You can configure the Likelihood Adjustment value for every DLP Rule with positive or negative values accordingly.
To configure Likelihood Adjustment, open a support ticket or contact Avanan Support.
Hot/Cold Words
Every DLP Rule is searched across the entire email/file/message by default.
Administrators can define the scope of the search so that it happens in the vicinity of certain words and/or not in the vicinity of others.
To configure Hot/Cold Words, open a support ticket or contact Avanan Support.
Configuring SmartDLP Engine Settings
To configure SmartDLP follow these steps:
- Navigate to Security Settings > Security Engines.
-
Choose SmartDLP and click Configure.
Configure SmartDLP screen appears.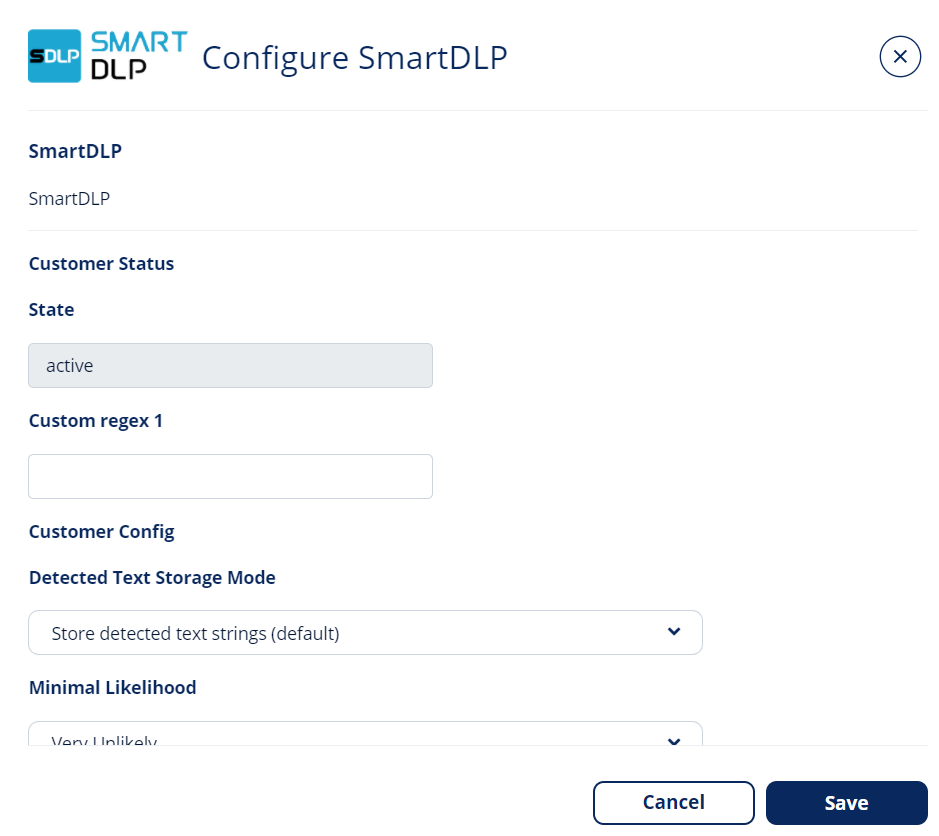
- Configure the different configuration options and click Save.
Storage of Detected Strings
When the DLP engine matches strings to a DLP rule, Avanan stores these strings and displays them for administrators with sufficient permissions when they investigate the security events. Since these strings are considered sensitive and private end-user data, you can select how they are stored and presented in the system called Detected Text Storage Mode.
To update Detected Text Storage Mode:
- Navigate to Security Settings > Security Engines.
- Click Configure for DLP.
- Scroll down to Detected Text Storage Mode and select one of these options.
- Store detected text strings (default): This is the default option, and the detected data is saved and displayed on the security events for the forensic process.
- Obfuscate detected text prior to storage: Detected data is saved and displayed on the security events obfuscated. The original data is discarded and cannot be accessed.
- Do not store detected text: No detected data is stored or displayed on the security events.
- Click Save.
Minimal Likelihood
DLP detection results are categorized based on how likely they are to represent a match. The likelihood is determined by the number of matching elements a result contains. The likelihood representation is intended to indicate how likely it is that a piece of data matches a given type of information (info type).
Likelihood scale:
- Very Unlikely: it is very unlikely that the data matches the given Info type.
- Unlikely: it is unlikely that the data matches the given Info type.
- Possible: it is possible that the data matches the given Info type.
- Likely: it is likely that the data matches the given Info type. Depends also on context.
- Very Likely: it is very likely that the data matches the given Info type. Depends also on context.
Context: SmartDLP checks for additional attributes and the presence of relevant data within the scanned document, depending on the configured level of likelihood. For example, when a Social Security Number (SSN) is discovered the engine can also check for the presence of relevant strings close to the discovered pattern, i.e. "SSN" or "Social Security".
DLP Exceptions
See DLP Exceptions.DLP - Supported File Types
Avanan detects DLP violations in a large list of file types, including EML, HTML, PDF, Microsoft Office files, images, and many more.
For more information, see Supported File Types for DLP.
DLP Inspection - File Size Limit
The DLP security engine inspects the email, its attachments and files that are less than 50 MB only.
Note - At times, the DLP security engine might inspect the archived files larger than 50 MB.
Forensics
DLP detections are recorded as events for forensic and auditing purposes. The events include what type of sensitive information was potentially leaked (PII, HIPAA, etc.).
You can view the events from the Events page.