Security Engines - Anti-Malware
The Anti-Malware engine determines if an email attachment or a shared file contains malware. It detects files containing known malware (Anti-Virus) and Avanan’s advanced sandbox (Threat Emulation) to detect the evasive zero-day malware.
Engines Enabled
Under Engines Enabled, you can see the security engines available based on the license.
It could include Anti-Virus (known malware detection) or Threat Emulation & Antivirus (advanced sandbox).
To see the Engines Enabled for your tenant, navigate to Security Settings > Security Engines and click Configure for Anti-Malware.
Malware Emulation Operating Systems
Sandboxing attachments and shared files is crucial for detecting advanced zero-day unknown malware hidden in them. During sandboxing, the Check Point Anti-Malware (Threat Emulation) engine opens the file in a secured virtual machine and baits it to trigger its malicious behavior.
A dedicated team in Check Point constantly perfects the engine and the preferences of the virtual machines on which files are emulated. Specifically, this team selects the operating systems of those machines.
Administrators can choose not to follow the Check Point best practices and to select the operating systems on their own. To do that, contact Avanan Support.
Note - Changing the default operating systems for emulation is not recommended and can damage the malware detection rate.
Anti-Malware Inspection - File Size Limit
The Anti-Malware security engine inspects files attached to an email or shared via supported file sharing/messaging applications for malware only if it is less than 50 MB.
Anti-Malware Exceptions
See Anti-Malware Exceptions.Reviewing Malware Events
The Anti-Malware engine is responsible for detecting malicious files. It comprises of matching the file against a database of known malicious files (Anti-Virus) and running it through an advanced sandbox (Threat Emulation).
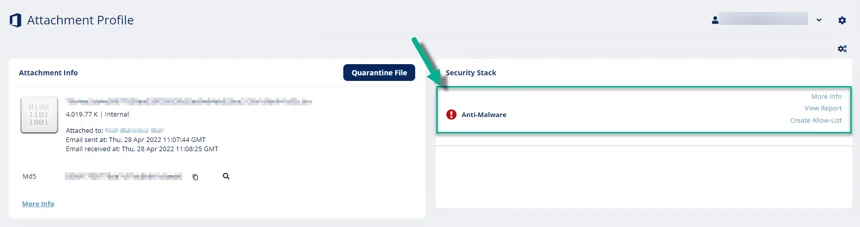
To review the event details, open the attachment profile page for the malicious event. In the Anti-Malware section under Security Stack, you can do these.
- To view the sandbox report with a detailed explanation about why the file was deemed malicious, click View Report.
- To download the malicious file from the report to your local computer, click Actions > Download File.
Warning - You should use the downloaded file with care as the malware can cause significant damage to computers, networks, and corporate data.- To help you not run the malicious file accidentally on your local computer, the malicious file gets downloaded in the compressed tar.gz format as a password-protected file.
- Use infected_te_report as the password to extract the malicious file.
- To download the malicious file from the report to your local computer, click Actions > Download File.
- To view the confidence level of the detection by the sandbox or the signature used by the static engines used to detect the malware, click More Info.
Acting on Malware Events
- To quarantine an email, click Quarantine Email from the email profile.
- To release an email from quarantine, click Restore Email if the email is already in quarantine.
- To exclude a file that you believe was falsely detected as containing malware, add the file to Allow-List.
For more details about adding Anti-Malware Allow-List rule, see Anti-Malware Allow-List.