File Storage Protection - Office 365 OneDrive
Overview
Office 365 OneDrive is a cloud storage system that allows sharing files and collaboration. Avanan adds security, privacy, and compliance to Office 365 OneDrive by scanning files shared in OneDrive for malicious content and data loss prevention (DLP) and generates actionable events on malicious content.
How it works
Avanan adds a layer of security that provides these security features for Office 365 OneDrive:
- Data Leak Prevention (DLP): Protecting sensitive text messages and files
- Anti-Malware: Scanning of files for malicious content
- User Behavior Anomaly: Identifying suspicious login and compromised accounts
- Remediation: Quarantine malicious files and send files containing sensitive data to the vault
Required Permissions
Avanan requires these permissions to protect Office 365 OneDrive.
Note- All these permissions are required to access your data in the Avanan portal tenant.
| Permissions required from Microsoft | Functions performed by Avanan |
|---|---|
| Manage all access reviews | Allows the app to read, update, delete and perform actions on access reviews, reviewers, decisions, and settings in the organization without a signed-in user. |
| Read and write all applications | Allows the app to create, read, update and delete applications and service principals without a signed-in user. Does not allow management of consent grants. |
| Read and write contacts in all mail boxes | Allows the app to create, read, update, and delete all contacts in all mailboxes without a signed-in user. |
| Read and write directory data | Allows the app to read and write data in your organization's directory, such as users, and groups, without a signed-in user. Does not allow user or group deletion. |
| Read and write domains | Allows the app to read and write all domain properties without a signed-in user. Also allows the app to add, verify and remove domains. |
| Read and write files in all site connections | Allows the app to read, create, update and delete all files in all site collections without a signed-in user. |
| Read and write all groups | Allows the app to create groups, read all group properties and memberships, update group properties and memberships, and delete groups. Also allows the app to read and write group calendar and conversations. All of these operations can be performed by the app without a signed-in user. |
| Read and write all user mailbox settings | Allows the app to create, read, update, and delete user's mailbox settings without a signed-in user. Does not include permission to send mail. |
| Read and write mail in all mailboxes | Allows the app to create, read, update, and delete mail in all mailboxes without a signed-in user. Does not include permission to send mail. |
| Send mail as any user | Allows the app to send mail as any user without a signed-in user. |
| Read all usage reports | Allows an app to read all service usage reports without a signed-in user. Services that provide usage reports include Office 365 and Azure Active Directory. |
| Read and update your organization’s security events | Allows the app to read your organization’s security events without a signed-in user. Also allows the app to update editable properties in security events. |
| Read and write items in all site collections | Allows the app to create, read, update, and delete documents and list items in all site collections without a signed-in user. |
| Read and write all users' full profiles | Allows the app to read and update user profiles without a signed-in user. |
| Sign in and read user profile | Allows users to sign in to the app, and allows the app to read the profile of signed-in users. It also allows the app to read basic company information of signed-in users. |
Activating Office 365 OneDrive
Important - To activate Office 365 OneDrive, make sure you have these:
- You are a user with Microsoft Global Administrator permissions, or you have the credentials of such a user.
- You have the minimum supported SaaS license. See Minimum Requirements.
To activate Office 365 OneDrive:
- Navigate to Security Settings > SaaS Applications and click Start for Office 365 OneDrive.
- Click Start in the pop-up screen that appears.
- In the Microsoft Sign in window that opens, sign in with your Microsoft administrator credentials.
Note - Microsoft performs the authentication, and Avanan does not provide these credentials. - In the authorization screen from Microsoft, click Accept to grant necessary permissions to Avanan.
For the list of permissions requested from Microsoft, see Office 365 OneDrive required permissions.
The Office 365 OneDrive SaaS is enabled, and monitoring begins immediately.
Deactivating Office 365 OneDrive
To deactivate Office 365 OneDrive:
- Navigate to Security Settings > SaaS Applications.
- Click Stop for Office 365 OneDrive.
Office 365 OneDrive Security Settings
Customizing Quarantine and Vault
Administrators can customize the quarantine and vault folders (folder names, quarantine/vault messages, etc.)
Quarantine folder
The Quarantine folder is used to quarantine malware-infected or sensitive files related to OneDrive. Infected or sensitive files of all the users gets quarantined and is placed in a single predefined Quarantine folder for your complete organization.
You can configure the Threat Detection policy and DLP policy to quarantine only malware and not sensitive files (which can be placed in end-user's Vault).
Notes:
- The quarantine folder gets created with the specified name in the root directory of the given email address. End users will not have access to this folder.
- Only Microsoft stores these quarantined files.
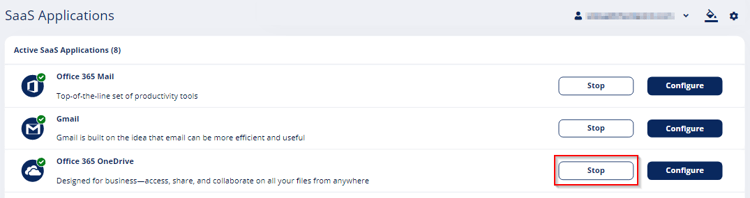
To customize the Quarantine folder:
- Navigate to Security Settings> SaaS Applications.
- Click Configure for Office 365 OneDrive.
- Go to the Quarantine Files section.
-
Under Store quarantined files in, select where you want to store the quarantined files:
-
Avanan - Stores the quarantined files in the Avanan cloud in the region associated with your organization’s Avanan Portal account.
-
Company’s OneDrive - Stores the quarantined files in a Quarantine folder located in your organization’s OneDrive account.
-
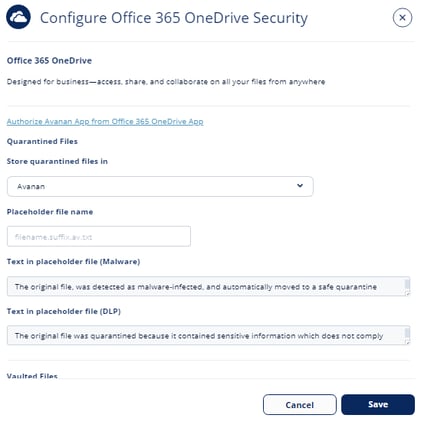
- If you selected Company's OneDrive in the previous step, enter these details for the quarantine folder:
- Under Quarantine folder owner email address, enter the required email address.
Note - OneDrive must exist for the email address you enter here. - Under Quarantine folder name, enter the required folder name.
Note - A Quarantine folder gets created with the entered name in the root directory of the given email address.
- Under Quarantine folder owner email address, enter the required email address.
- (Optional) If you need to configure the content of the file that replaces the quarantined malicious file in its original folder, enter the text under Text in placeholder file (Malware).
- (Optional) If you need to configure the content of the file that replaces the quarantined sensitive file in its original folder, enter the text under Text in placeholder file (DLP).
- Click Save.
Vault folder
A vault folder is used to remediate DLP detections related to OneDrive files. It is a non-shared folder that is created for every OneDrive user.
If a file contains sensitive information that does not comply with your organization's data-sharing policies, it is removed and placed in the vault folder.
Notes:
- The Vault folder gets created with the specified name in the root directory of each user.
- The user can access the file from the Vault but cannot share it with others.
To customize the Vault folder:
- Navigate to Security Settings > SaaS Applications.
- Click Configure for Office 365 OneDrive.
- Go to the Vaulted Files section.
- Under Vault folder name, enter the required vault folder name.
Note - The Vault folder gets created with the specified name in the root directory of each user. - If you want to allow end users to manually restore files from the Vault, enable the Allow end users to manually restore files from Vault checkbox.
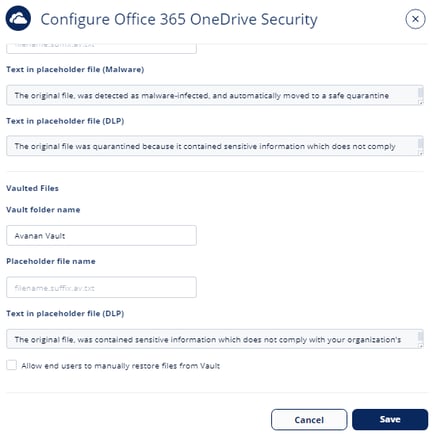
- (Optional) If you need to configure the content of the file that replaces the vaulted sensitive file in its original folder, enter the text under Text in placeholder file (DLP).
- Click Save.
Configuring Office 365 OneDrive Policy
Malware Policy
By default, the Office 365 OneDrive malware policy scans the uploaded files for malicious content.
Supported Actions
Office 365 OneDrive malware policy supports these actions:
- Quarantine/removal of malware-infected files.
- Alert owner: Sends an email notification to the user who uploaded a file that contains malicious content.
- Alert admin(s): Sends an email notification to the admin(s) about the malicious files.
Configuring Malware Policy
To configure Malware policy:
- Click Policy on the left panel of the Avanan portal.
- Click Add a New Policy Rule.
- From the Choose SaaS drop-down list, select Office 365 OneDrive.
- From the Choose Security drop-down list, select Malware and click Next.
- Select the desired protection mode (Detect and Remediate or Detect).
If required, you can change the Rule Name. - Choose the Scope for the policy.
- To apply the policy to specific users or groups, select the users and groups and click Add to Selected.
- To apply the policy to all users and groups in your organization, enable All Users and Groups checkbox.
- To exclude specific users or groups from the policy, select the users/groups and click Add to Excluded.
- Under Blades, select the threat detection blades required for the policy.
Note - To select all the blades available for malware detection, enable All running threat detection blades checkbox. - Under Suspected malware workflow (Attachment), select the workflow required for the policy.
- Quarantine. User is not alerted (admin can restore)
- Do nothing
Note - The Workflows are available only when Detect and Remediate protection mode is enabled.
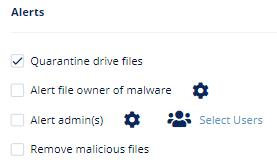
- To quarantine malware-infected files, enable the Quarantine drive files checkbox under Alerts.
Note - This option will be available only in Detect and Remediate protection mode. - To remove malware-infected files, enable the Remove malicious files checkbox under Alerts.
Notes:- If you enable this option, malicious files will be removed permanently, and you cannot restore them.
- For a policy, you can only enable Quarantine drive files or Remove malicious files.
- Configure Alerts for the policy.
- To send email alerts to the file owner of malware, enable the Alert file owner of malware checkbox.
- To send email alerts to admins about malware, enable the Alert admin(s) checkbox.
Notes:
- Even when the alerts are enabled here in the policy, the administrator only receives email alerts for security events when Receive Alerts role is enabled in the Specific Service Role.
- To customize the email alert templates, click on the gear icon to the right of the alert.
- Click Save and Apply.
DLP Policy
By default, the DLP policy scans the uploaded files to OneDrive for potentially leaked information, such as credit card number and Social Security Number (SSN).
Supported Actions
Office 365 OneDrive DLP policy supports these actions:
- Send files with sensitive data to the vault.
- Alert owner: Sends an email notification to the user who uploaded a file that contains sensitive information.
- Alert admin(s): Sends an email notification to the admin(s) about the files that contain sensitive information.
Configuring DLP Policy
To configure DLP policy:
- Click Policy on the left panel of the Avanan portal.
- Click Add a New Policy Rule.
- From the Choose SaaS drop-down list, select Office 365 OneDrive.
- From the Choose Security drop-down list, select DLP and click Next.
- Select the desired protection mode (Detect and Remediate or Detect).
If required, you can change the Rule Name. - Choose the Scope for the policy.
- To apply the policy to specific users or groups, select the users and groups and click Add to Selected.
- To apply the policy to all users and groups in your organization, enable All Users and Groups checkbox.
- To exclude specific users or groups from the policy, select the users/groups and click Add to Excluded.
- Under DLP Criteria, select the DLP categories required for the policy. For more details about the DLP rules and categories, see DLP Built-in Rules and Categories.
- Select the sensitivity level required for the policy.
- Very high (hit count > 0)
- High (hit count > 2)
- Medium (hit count > 5)
- Low (hit count > 10)
- Very Low (hit count > 20)
- To exclude DLP policy for the files shared only with the internal users, enable the Skip Internal items checkbox.
- Configure Actions for the policy.
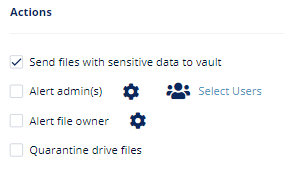
- To send a detected file with sensitive data to its owner’s vault, enable the Send files with sensitive data to vault checkbox.
Note - This option will be available only in Detect and Remediate protection mode. - To send email alerts to admins about DLP, enable the Alert admin(s) checkbox.
- To send email alerts to the file owner about DLP, enable the Alert file owner(s) checkbox.
- To quarantine drive files, enable the Quarantine drive files checkbox.
Notes:
- For a policy, you can only enable Send file with sensitive data to vault or Quarantine drive files.
- Even when the alerts are enabled here in the policy, the administrator only receives email alerts for security events when Receive Alerts role is enabled in the Specific Service Role.
- To customize the email alert templates, click on the gear icon to the right of the alert.
- To send a detected file with sensitive data to its owner’s vault, enable the Send files with sensitive data to vault checkbox.
- Click Save and Apply.
Viewing Office 365 OneDrive Security Events
Avanan records the OneDrive detections as security events. The event type depends on the type of policy that created the event. You can handle the security events in different ways, whether they are detected/prevented automatically or discovered by the administrators after not being prevented.
The Events screen shows a detailed view of all the security events.
Note - For files marked as malware by Microsoft, scan results are unavailable, and access to these files is prevented by Microsoft.