Modules - Data Loss Prevention (DLP)
What is Avanan DLP?
Cloud applications make it easier than ever for your employees to access and share data, both internally and externally. This makes cloud services a major source of risk. Complicated sharing permissions make data leakage and compliance difficult to manage.
Avanan enables you to create universal policies across multiple cloud applications to control how files are shared amongst internal and external users. Our advanced tools identify and mark files containing confidential, financial, and personally identifiable information, including: credit card numbers, social security numbers, bank routing numbers, or data protected under HIPAA.
Avanan SmartDLP - DLP Engine
SmartDLP is a DLP engine developed by Avanan. It allows to easily detect sensitive information and generate security alerts in Avanan with a DLP policies.
For more information on SmartDLP read the following article.
Note - DLP is not available for Avanan Portal accounts residing in the United Arab Emirates (UAE) region. If required, you can request to enable DLP. However, sensitive data analysis will be performed in the United Kingdom (UK) and not within the borders of the UAE. If you wish to enable DLP, contact Avanan Support.
Benefits
- Scan emails and files for sensitive information with ease, by using a common solution for all platforms.
- Stop data leakage by using automated actions.
- Generate actionable alerts.
- Use an integrated solution for DLP and other types of attacks, such as phishing and malware.
Data Loss Prevention (DLP) Policy
DLP Policy filters outgoing emails to ensure that sensitive data does not reach unauthorized recipients. In addition, it can also filter incoming emails to ensure sensitive data is not stored in your organization's mailboxes and/or that it is shared only through authorized delivery methods.
Note - Changing the policy protection mode from Monitor Only or Detect and Prevent mode to Prevent (Inline) mode takes time to start protecting in Prevent (Inline) mode. It could take up to an hour, depending on the number of protected users in the Avanan account.
For more details about the DLP security engine, see Configuring DLP Security Engine.
Sync Times with Microsoft
- If you change the policy protection mode from Monitor Only or Detect and Remediate mode to Prevent (Inline) mode, it takes time to start protecting in Prevent (Inline) mode. It could take up to an hour, depending on the number of protected users in the Avanan portal.
- When adding a user to the scope of a Prevent (inline) policy that is not set to All Users and Groups, it may take up to 1 hour for emails from this user to be inspected inline.
- When a new user is added to Microsoft 365, administrators can include them in the policy scope within 10 minutes or it might take up to 24 hours.
DLP Policy for Outgoing Emails
To configure the DLP policy for outgoing emails:
- Go to Policy.
- Click Add a New Policy Rule.
- Select the desired SaaS application under Choose SaaS drop-down.
- Select DLP under Choose Security drop-down and click Next.
- Select Protect (Inline) or Monitor only mode.
- Select the Scope of the policy:
- Select Outbound Emails.
- Select the Specific Sending Users and Groups, the policy applies to.
- In the DLP Criteria section, do these:
- Select the required DLP Categories.
- Select the required Sensitivity Level. See DLP Policy Sensitivity Level.
- If you need to add a subject regular expression as the matching criteria to the DLP policy, under Advanced, enable the Enable matching based on subject regular expression checkbox and enter the regular expression. See DLP Subject Regular Expression.

- In the DLP Workflow section, select the required DLP workflow. See DLP Workflows for outgoing emails.
Note - This option is available only in Protect (Inline) mode. - Select the required Severity.
- Select the required DLP Alerts. See DLP alerts for outgoing emails.
- Click Save and Apply.
Note - Applying a Prevent (Inline) rule could take up to an hour to take effect, depending on the number of protected users in the Avanan account.
For more details about the DLP security engine, see Data Loss Prevention.
DLP Subject Regular Expression (Regex)
By default, Avanan matches emails to DLP policy rules based on the data types detected in them. However, you can use regular expressions to match emails from the email subject.
This type of matching helps you to detect sensitive emails from the email subject and allows you to trigger specific workflow. Therefore, emails with a defined subject pattern will match the DLP policy rule regardless of the data types they include.
To add a regular expression condition to a DLP policy:
- Navigate to Policy.
- To add the regular expression to an existing DLP policy, click the policy and continue from step 6.
- To create a new DLP policy, click Add a New Policy Rule.
- Select the desired SaaS application under Choose SaaS drop-down.
- Select DLP under Choose Security drop-down and click Next.
- Select Prevent (Inline) or Monitor only protection mode.
- Select the Scope of the policy:
- Select email direction as Outbound.
- Under Senders, select the Specific Users and Groups the policy applies to.
- In the DLP Criteria section, do these:
- Select the required DLP Categories.
- Select the required Sensitivity Level.
- In Advanced, select the Enable matching based on subject regular expression checkbox.
- Enter the regular expressions.
- Click Save & Apply.
Subject Regular Expressions Syntax
The Subject Regular Expression field allows you to enter values in the Python Regular Expressions (RE) syntax.
For example, to create a DLP policy rule to find emails that contain the string [secure] in the email subject, add (?i)\[secure] or \[secure] where (?i) is used to specify that it is case insensitive to the Subject Regular Expression field in the policy.
To create a DLP policy rule to find emails that contain either the exact strings [secure] or [encrypt] in the email subject, you can add either \[secure\]|\[encrypt\] or ex \[secure]|\[encrypt] to the Subject Regular Expression field in the policy.
For more information, see Python regular expressions documentation.
DLP Workflows for Outgoing Emails
| Workflow | Description |
| Email is blocked. User is alerted and allowed to request a restore (admin must approve) |
Any detected email will not be delivered to the recipient and will be moved to quarantine mailbox.
|
| Email is blocked. User is alerted and allowed to restore the email |
Any detected email will not be delivered to the recipient and will be moved to quarantine mailbox.
|
| Email is allowed. Header is added to the email | Any detected email will be delivered to the recipient with additional header that is configured in the policy. |
| Do nothing | Any detected email will be delivered to the recipient without any changes. |
| Microsoft Encryption Workflows | |
| Email is blocked and user can resend as encrypted by Microsoft | Any detected email will not be delivered to the recipient and the user can resend the email as Microsoft encrypted email. |
| Email is allowed. Encrypted by Microsoft | Any detected email will be delivered to the recipient as encrypted by Microsoft and a header will be added to the email. For more information, see Office 365 Encryption. |
| Email is blocked and user can request to resend as encrypted by Microsoft (admin must approve) |
Any detected email will not be delivered to the recipient and will be moved to quarantine mailbox.
|
| SmartVault Workflows | |
| Email is blocked and user can resend as encrypted by SmartVault | Any detected email will not be delivered to the recipient and the user can resend the email as SmartVault email. |
| Email is allowed. Encrypted by SmartVault | Any detected email will be vaulted by SmartVault and the recipient receives a email notification. For more information, see Avanan SmartVault. |
| Email is blocked and user can request to resend as encrypted by SmartVault (admin must approve) |
Any detected email will not be delivered to the recipient and will be moved to quarantine mailbox.
|
For more information on who receives the restored emails, see Who receives the Emails Restored from Quarantine.
DLP Alerts for Outgoing Emails
- Send email alert to admins when a DLP policy is violated.
- Send email alert to specific recipients when DLP is detected. It is possible to customize email template using the gear icon next to the action.
- Send email alert to the direct manager when an employee sends (or attempts to send) confidential data that violates a DLP policy.
Notes:
- When this option is enabled, email alerts are sent to the manager even when the email is blocked.
- This option is available only for Office 365 DLP policies.
- Send email alert to the sender when DLP Subject Regex pattern and DLP are detected in the email. For details, see DLP Subject Regular Expression.
- Send email alert to the sender when DLP Subject Regex pattern is not detected but DLP is detected in the email subject. For details, see DLP Subject Regular Expression.
Prerequisites to Avoid Failing SPF Checks
For Office 365 Mail, if you enable Protect (Inline) Outgoing Traffic in the DLP or Threat Detection policy, Avanan gets added to the email delivery chain before reaching external recipients (Internal email sender > Microsoft 365 > Avanan > Microsoft 365 > External recipient).
The recipient's email security solution sees the Avanan IP address as part of the delivery chain. If the recipient's email security solution fails to recognize the original IP address, it may consider the Avanan IP address as the IP address from which the email was sent.
If you do not configure the SPF record in your DNS to allow Avanan IP addresses to send emails on behalf of your domain, your emails might fail SPF checks and may be rejected. Avanan recommends you add the Avanan IP addresses to your SPF record before you enable Protect (Inline) Outgoing Traffic for outgoing emails.
To prevent outgoing emails from failing SPF checks and being quarantined, you must add include:spfa.cpmails.com to your SPF record.
Note - The above statement includes several IP addresses and networks, some outside your Avanan portal's data region. This is done for uniformity and consistency in all Avanan SPF records regardless of your data region. Avanan sends the emails only from one of the IP addresses in your region.
Office 365 Footprint
Transport rules:
Additional transport rule is created when enabling Inline DLP.
- Rule name: Avanan - Protect Outgoing.
- Verify similar to Avanan - Protect.
- Rule:

-
Rule description:
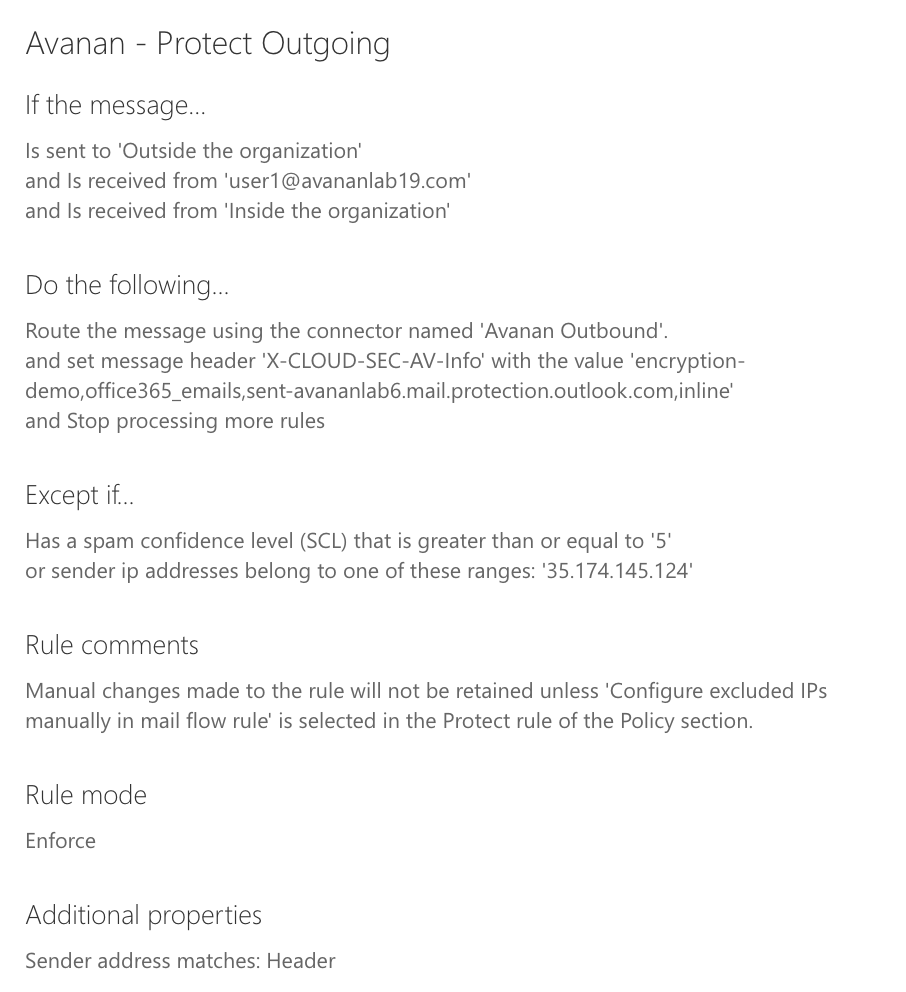
Connectors
Additional connector will be added, Avanan to O365
-
Connector:
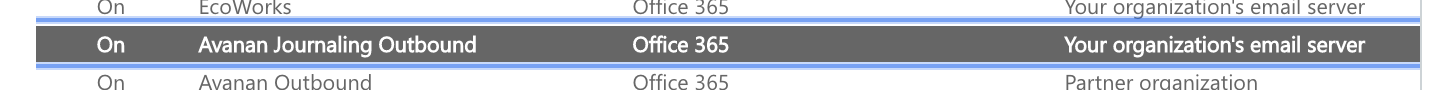
DLP Policy Sensitivity Level
The Sensitivity Level for a DLP policy is the minimum number of times all the Data Types in the selected categories need to match (hit count) for the policy to trigger the DLP workflow.
You can select these Sensitivity Level for every policy rule.
- Very High (hit count > 0)
- High (hit count > 2)
- Medium (hit count > 5)
- Low (hit count > 10)
- Very Low (hit count > 20)
- Custom (and enter the minimum hit count (Hit count higher than) required for the policy)
For example, a DLP policy includes only the PII category and you selected the Sensitivity Level as High.
- If all the Data Types in PII were matched only once - the rule does not trigger the selected DLP workflow.
- If all the Data Types in PII were matched three times - the rule triggers the selected DLP workflow.
DLP Policy for Incoming Emails
To configure the DLP policy for incoming emails:
- Go to Policy.
- Click Add a New Policy Rule.
- Select the desired SaaS application under Choose SaaS drop-down.
- Select DLP under Choose Security drop-down and click Next.
- Select Protect (Inline) mode.
- Select the Scope of the policy:
- Select Inbound Emails.
Note - This option is available only in Protect (Inline) mode. - Select the Specific Receiving Users and Groups to which the policy applies.
- Select Inbound Emails.
- In the DLP Criteria section, do these:
- Select the required DLP Categories.
- Select the required Sensitivity Level. See DLP Policy Sensitivity Level.
- Select the required DLP Rules.
- Select the required DLP workflow.
- Click Save and Apply.
Note - Applying a Prevent (Inline) rule could take up to an hour to take effect, depending on the number of protected users in the Avanan account.
For more details about configuring the DLP engine, see Data Loss Prevention.
DLP Workflows for Incoming Emails
- Email is blocked. User is alerted and allowed to request a restore (admin must approve) (default)
- Detected email will not be delivered to the recipient and will be moved to quarantine mailbox. The
user will receive an email with an alert of the quarantine action, and will be able to request to restore
the original email (send the original email to the recipient). - Email is blocked. User is alerted and allowed to restore the email - Any detected email will not be
delivered to the recipient and will be moved to quarantine mailbox; the user will receive an email with
alert of the quarantine action, and will be able to restore the original email (send the original email to
the recipient). - Do nothing - Any detected email will be delivered to the recipient without any changes.
- User receives the email with a warning - The email is delivered to the user with a warning banner inserted in the body of the email. To customize the banner (text, background color, etc.), click the gear icon next to the workflow.
- Email is allowed. Header is added to the email - The detected email is delivered to the recipient with an additional header that can be configured in the policy.
- Email is blocked. User is not alerted (admin can restore) - Detected email will not be delivered to the recipient and is automatically quarantined without any user notification. The administrator can restore the email.
DLP Alerts for Incoming Emails
You can configure alerts for incoming emails detected to contain a DLP violation:
- Send alert on this violation to specific mailboxes.
- Alert the external sender about the violation when the email is quarantined.