Visibility into Microsoft Defender's Verdict and Enforcement
Avanan provides visibility to how Microsoft Defender classified the emails and which enforcement action it intended to perform.
You can view Microsoft Defender's visibility for an email in the Security Stack section of the email profile page.
Note - Microsoft Defender's visibility is available only for incoming and internal emails.
Spam confidence level (SCL)
Microsoft assigns a spam confidence level (SCL) to inbound messages that go through spam filtering and are assigned a spam score. That score is mapped to an individual spam confidence level (SCL) that's added to the email. A higher SCL indicates a message is more likely to be spam.
| SCL Value | Description |
| -1 | The message skipped spam filtering. For example, the message is from a safe sender, was sent to a safe recipient, or is from an email source server on the IP Allow List. |
| 0, 1 | Spam filtering determined the message wasn't Spam. |
| 5, 6 | Spam filtering marked the message as Spam |
| 8, 9 | Spam filtering marked the message as High confidence spam. |
For more information, see Spam confidence level (SCL).
Bulk complaint level (BCL)
Microsoft assigns a bulk complaint level (BCL) to inbound messages from bulk mailers. A higher BCL indicates a bulk message is more likely to generate complaints (and is therefore more likely to be spam).
| BCL Value | Description |
| 0 | The message isn't from a bulk sender. |
| 1, 2, 3 | The message is from a bulk sender that generates few complaints. |
| 4, 5, 6, 7* | The message is from a bulk sender that generates a mixed number of complaints. |
| 8, 9 | The message is from a bulk sender that generates a high number of complaints |
| * This is the default threshold value used in anti-spam policies. | |
For more information, see Bulk complaint level (SCL).
Phishing confidence level (PCL)
The phishing confidence level (PCL) indicates the likelihood that a message is a phishing message based on its content.
| PCL Value | Description |
| 1, 2, 3 | The message content isn't likely to be phishing. |
| 4, 5, 6, 7, 8 | The message content is likely to be phishing. |
For more information, see Phishing confidence level (SCL).
Enforcement Flow
The Enforcement Flow shows the enforcement action taken by Microsoft and Avanan in an email. You can view the Enforcement Flow for an email in the Security Stack section of the email profile page.
Note - The Enforcement Flow does not include manual actions taken on the email.
Depending on the Protection mode selected in the threat detection policy, the Enforcement Flow would be different.
- Example of an email inspected by a policy in Protect (Inline) protection mode.
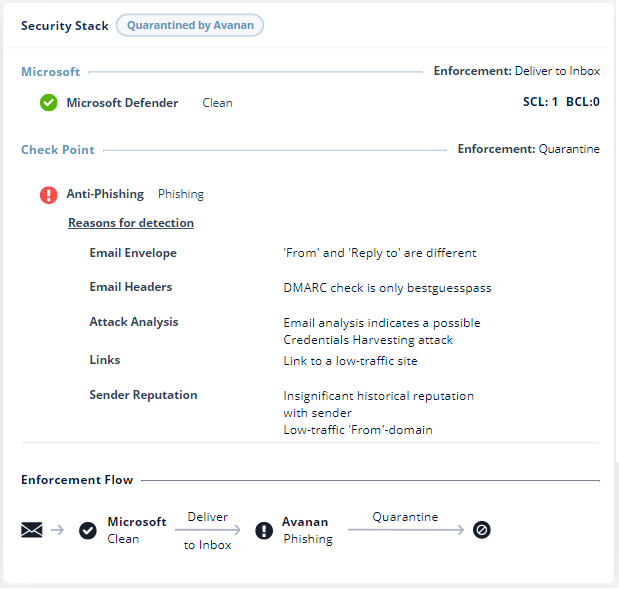
Microsoft finds the email Clean and intends to deliver it to the user's mailbox. Avanan scans the email, finds it Malicious, and quarantines it before it gets to the user's mailbox since it's inspected by a Protect (Inline) policy.- Microsoft finds the email Clean and intends to deliver it to the user's mailbox. Enforcement: Deliver to Inbox.
- Avanan scans the email and finds it malicious. Avanan quarantines the email before it gets delivered to the user's mailbox and quarantines it. Enforcement: Quarantine.
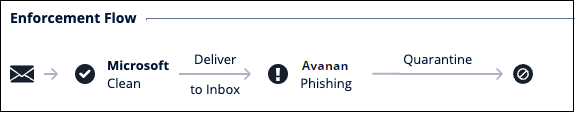
- Example of an email inspected by a policy in Detect & Remediate protection mode.
- Microsoft finds the email Clean and delivers it to the user's mailbox. Enforcement: Deliver to Inbox.
- Avanan scans the email and finds it malicious. Avanan pulls the email from the user's mailbox and quarantines it. Enforcement: Quarantine.
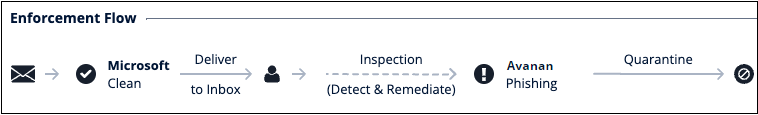
- Example of an email inspected by a policy in Detect protection mode.
- Microsoft finds the email Clean and delivers it to the user's mailbox. Enforcement: Deliver to Inbox.
- Avanan only scans the email and does not perform any enforcement as the policy protection is in Detect mode. Enforcement: Deliver to Inbox (Monitoring).
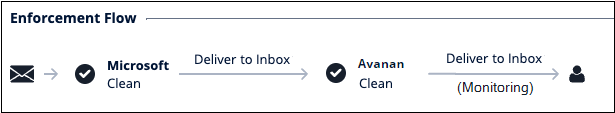
- When Avanan is configured to automatically restore emails quarantined by Microsoft 365 for being High Confidence Phishing, and if Avanan classifies them as Clean:
- Microsoft finds the email High Confidence Phishing and quarantines it.
- Avanan scans the email and finds it clean. Check Point restores the email to the user's inbox.
Releasing Microsoft 365 High Confidence Phishing False Positive Emails
Administrators can configure Avanan to automatically release emails quarantined by Microsoft for being High-Confidence Phishing emails if Avanan classifies
them as Clean / Spam / Suspected Phishing. To do that:
- Go to Security Settings > User Interaction > Quarantine.
- In the Emails Quarantined by Microsoft section, expand Emails Quarantined by Microsoft as High-Confidence Phishing, and select the Automatically restore if Avanan classifies differently checkbox.
- From the list, select the preferred Avanan verdicts.
- Clean
- Spam
- Suspected Phishing
- Click Save and Apply.
Note - The policy workflow will not apply to these emails as the released email is the original email. The email will be sent directly to the user's mailbox.