Security Engines - Click-Time Protection
Avanan's virtual inline technology provides phishing protection for emails after they have been scanned by Microsoft servers, but before they reach the user’s mailbox.
New attacks have become more sophisticated and can generate phishing campaigns such that the phishing website they link to does not have any known bad reputation, sometimes for hours and days after the emails are sent.
Click-Time Protection works by replacing links. The replaced links point to the Avanan inspection services, so that every time a user clicks on a link, the website behind the link is inspected to ensure it is not a phishing website.
Click-Time Protection uses these security engines for inspection.
- URL Reputation - Checks if the URL is known to be malicious or holds any malicious references.
- URL Emulation - Emulates the website to detect zero-day phishing websites
Benefits
- Most Up-to-Date Intelligence - Inspecting links when the user clicks on the URL allows to inspect the URL based on the latest inspection intelligence and software capabilities.
- Protection against zero-day phishing websites - Inspecting links when the user clicks on the URL allows to follow the user into the website. Click-Time Protection then emulates the website to expose hidden Phishing indicators. So Phishing websites that are not known to be malicious are also flagged.
- Pointing out the users that clicked the malicious URL - Click-Time Protection forensics allows to detect the users that require further education and training to avoid clicking on malicious links.
Note - Click-Time Protection is available for Office 365 email and Gmail.
Interaction with Microsoft ATP
Avanan supports link rewriting even when Microsoft Safe Links is enabled. When both Avanan Click-Time Protection and Microsoft Safe Links are active, the Avanan rewritten link is embedded within the Microsoft rewritten link.
The format of the rewritten link is as follows:
<Safe Links rewritten URL prefix> <Avanan rewritten URL prefix> <Original URL> <Avanan rewritten URL suffix> <Microsoft Safe Links suffix>.
This integration provides the protection of both Avanan and Microsoft without you requiring to disable either one:
- Both Avanan and Microsoft inspects the original link upon email receipt.
- When a user clicks the URL, both Avanan and Microsoft inspects the website or file linked and can block access if it is identified as malicious.
When clicking on re-written links, the end user experiences the following:
| Microsoft Verdict | Avanan Verdict | End User Experience |
| Clean | Clean | Redirect to the original URL. |
| Malicious | Malicious or Clean | Microsoft block page |
| Clean | Malicious | Avanan block page. see Click-Time Protection End-User Experience. |
Configuring Click-Time Protection Engine
To configure Click-Time Protection engine:
- Navigate to Security Settings > Security Engines.
- Click Configure for Click-Time Protection.
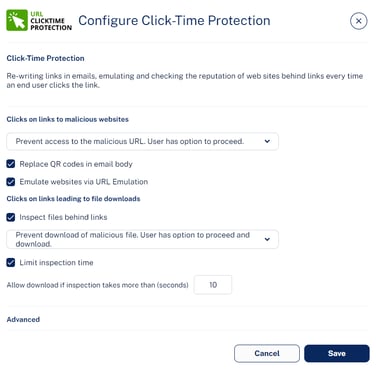
- In the Click on links to malicious websites section, select the required option to handle the malicious websites.
- Prevent access to the malicious URL. User has option to proceed.
- Prevent access to the malicious URL. User cannot proceed.
- Do nothing
- To replace the QR code in the body of the email to redirect to the rewritten link, select the Replace QR codes in email body checkbox.
Note - For the rewritten QR codes, the structure will be the same as V2 version even if you select to use V1 version. For more information, see Rewritten URL. - To emulate websites behind links to detect phishing websites with no bad reputation, select the Emulate websites via URL Emulation checkbox.
Note - If the Emulate websites via URL Emulation was disabled, and if the administrator enables it, it could take up to 20 minutes for the URL Emulation to start working. - To inspect files behind links, do these in the Clicks on links leading to file downloads section:
- Select the Inspect files behind links checkbox.
- Select a workflow:
- Prevent download of malicious file. User has option to proceed and download.
- Prevent download of malicious file. User cannot proceed.
- Do nothing
- To allow the download of files if the file inspection exceeds a specific time, do these:
- Select the Limit inspection time checkbox.
- In the Allow download if inspection takes more than (seconds) field, enter the time in seconds.
For more information, see Protection Against Malicious Files Behind Links.
- Under Advanced, select the required URL version (V1 or V2).
Note - Avanan recommends using V2 version. - Click Save.
Notes:
- To start rewriting the links, you must configure a Click-Time Protection policy. To configure Click-Time Protection policy, see Configuring Click-Time Protection policy.
- To create Allow-List or Block-List for Click-Time Protection, see Click-Time Protection Exceptions.
Re-Written Avanan URL
The format of the rewritten Avanan URL is <click-time domain>_<original url>_<encrypted blob>. While configuring the Click-Time Protection engine, administrators can choose the <click-time domain> from
these versions:
- V1: https://avanan.url-protection.com/v1/
- V2: https://url.avanan.click/v2/
In the <click-time domain> V2 version, the original URL is surrounded by underscores, making it easier to identify the original (rewritten) URL. Also, the URL is shorter, and the domain is different from the V1 version.
Notes:
- Avanan recommends using V2 version.
-
For rewritten QR codes, the structure will be the same as V2 version even if you select to use V1 version.
Hiding Original URL Full Path
By default, the rewritten URL includes the full path of the original URL, improving readability and predictability for end users. However, if administrators do not want to show the full path, they can configure the Click-Time Protection security engine to rewrite the URL to include only the domain of the original link, obfuscating the remaining path.
To obfuscate the full path of the original URL:
- Navigate to Security Settings > Security Engines.
- Click Configure for Click-Time Protection.
- In the Re-written URL field, select one of these:
- Full original URL included in re-written URL
- Only original URL domain visible in re-written URL
Note - Obfuscating the original URL is only supported when the version of the re-written link is v2.
Re-written URL Containing an Obfuscated Original URL
For example, if the original link is https://www.acme.org/lorem/ipsum/dolor.aspx, the re-written link:
- Without obfuscation - https://https://url.avanan.click/v2/___https://www.acme.org/lorem/ipsum/dolor.aspx{}.YXAzOnByb2...{_}
- With obfuscation - https://https://url.avanan.click/v2/___https://www.acme.org/NsyjwsfqrjidLjsjyn.fxuC___.YXAzOnByb2...
Validity of Rewritten URL
- Avanan inspects the website behind the rewritten URL only when you have a valid license.
- Rewritten URLs remain valid indefinitely, even when you do not have a valid license or when you delete the Avanan Portal.
- After the license expires, Avanan redirects the rewritten URL to the original URL without inspection.
- Avanan handles the rewritten URLs as described above regardless of the identity of the user that clicks the URL - internal user, external user, or unidentified user.
Therefore, even if the email is forwarded to a user in your organization that is not protected by Avanan, this user's click is also secured by Avanan.
Replacing Links Inside Attachments - Supported File Types
If you configured the Click-Time Protection Policy to replace links inside the attachments, the links get replaced for these file types:
| File Type | File Extensions |
| Adobe FDF | FDF |
| Adobe PDF (all versions) | |
| Microsoft Excel 2007 and later | XLSX, XLSB, XLSM, XLTX, XLTM, XLAM |
| Microsoft Excel 2007 Binary | XLSB |
| Microsoft Excel 97 - 2003 | XLS |
| Microsoft PowerPoint 2007 and later | PPTX, PPTM, POTX, POTM, PPAM, PPSX, PPSM |
| Microsoft PowerPoint 97 - 2003 | PPT, PPS, POT, PPA |
| Microsoft Word 2007 and later | DOCX, DOCM, DOTX, DOTM |
| Microsoft Word 97 - 2003 | DOC, DOT |
Protection Against Malicious Files Behind Links
The Anti-Malware security engine emulates the files behind direct download links before delivering them to end users. To prevent attacks in which the file behind the link is altered after the email is sent, this inspection will also take place when users click on such links after they are re-written by Click-Time Protection.
If the file behind the link is found to be malicious, and the Click-Time Protection security engine is configured to block it, access to the file will be blocked.
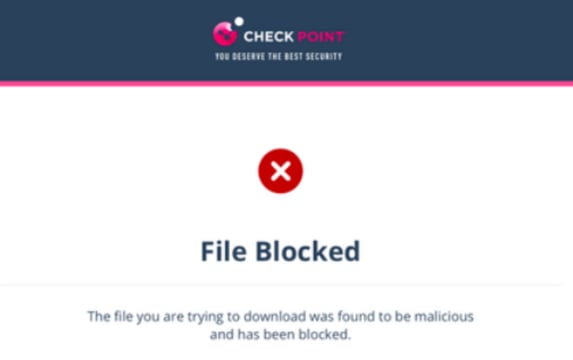
To configure the workflow in the Click-Time Protection security engine, see Configuring Click-Time Protection Engine.
Click-Time Protection - End-User Experience
After configuring a Click-Time Protection policy, Avanan replaces all URLs in the incoming emails and their attachments with a Avanan URL.
The URL also provides a tool-tip with the original URL, indicating that the link is protected by Avanan.

Note: Formatted tooltips are available on Microsoft Outlook for Mac, Outlook Web Access, and many other clients. Some clients, such as Outlook for Windows, limit the ability to present tooltips and will present the raw rewritten URL.
Clicks on Malicious Websites - End-User Experience
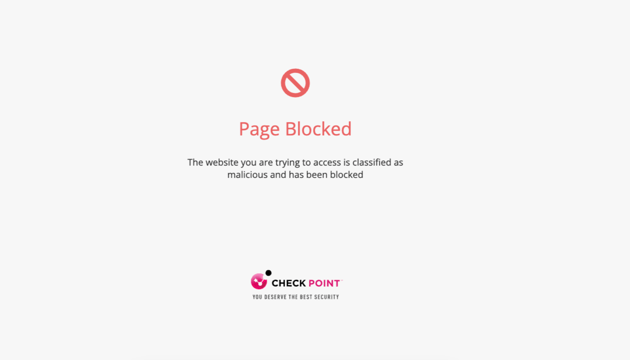
When a user clicks on the URL, Avanan checks the target URL.
- If the URL is not found to be malicious, the user will be redirected to the original URL.
- If the URL is found to be malicious, the user is forwarded to a warning page.
- If the workflow for malicious URLs is Prevent access to the malicious URL. User has option to proceed in the Click-Time Protection security engine, an additional Proceed anyway link will be available in the warning page.
Clicks on Direct Download Links - End-User Experience
When a user clicks a direct download link, the Anti-Malware security engine emulates the file.
-
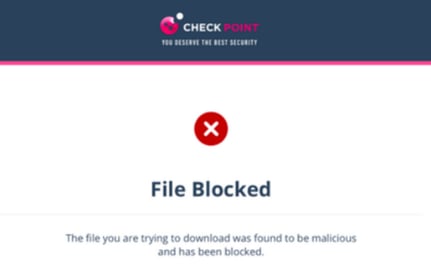
If the file is detected as malicious:
-
If the configured workflow is Prevent download of malicious file. User cannot proceed, it blocks the file and shows the warning page.
-
If the configured workflow is Prevent download of malicious file. User has the option to proceed and download, it blocks the file and shows the warning page. However, the user can click Download anyway to download the file.
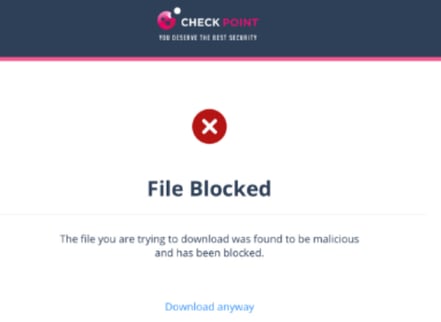
- If the file is detected as clean, it shows the notification and downloads the file.
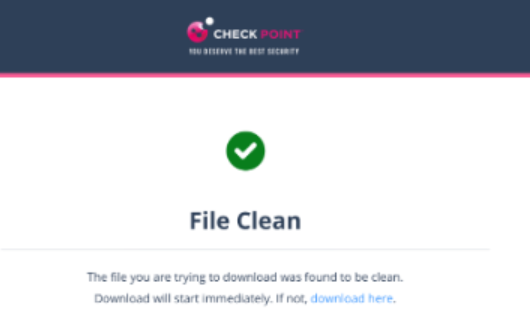
-
Google Drive Preview Links
By default, in the Gmail interface, when there is a link to a file in Google Drive, the email shows the file preview as if it was attached to the email.
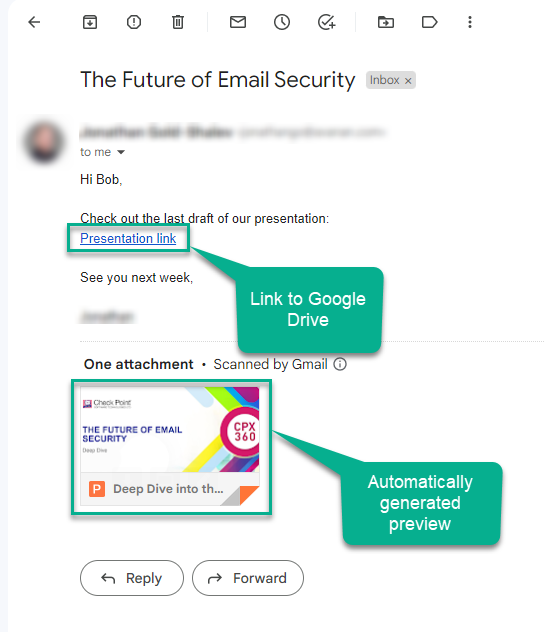
But, when Avanan rewrites the link, the file preview will not be showed.
Configuring Click-Time Protection Policy
To configure Click-Time Protection policy:
- Navigate to Policy.
- Click Add a New Policy Rule.
- Select the desired SaaS application under Choose SaaS drop-down.
- Select Click-Time Protection under Choose Security drop-down and click Next.
- Choose Scope for the policy.
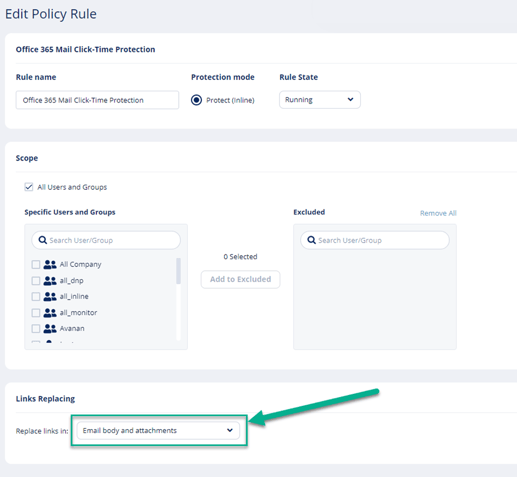
- Under Links Replacing, choose where to replace the links for the email.
- Email body
- Email body and attachments
- Under Severity, select the severity of the events generated by Click-Time Protection security engine.
- Auto
- Critical
- High
- Medium
- Low
- Lowest
- Click Save and Apply.
Click-Time Protection Exceptions
See Click-Time Protection Exceptions.
Forensics
Each stage of the Click-Time Protection process is recorded for forensic and auditing purposes, from the original URL replacement to the result of the time-of-click scan.
Click-Time Protection processes the events as Malicious Url Click and Proceed to Malicious Url.
- Malicious Url Click event is recorded when a user clicks on the rewritten URL and is redirected to the warning page.
- Proceed to Malicious Url event is recorded when the user clicks Proceed anyway in the warning page.
Note - Proceed to Malicious Url is available depending on your company’s policy.
For multiple recipients, each URL click would generate an event. Events are aggregated by default.
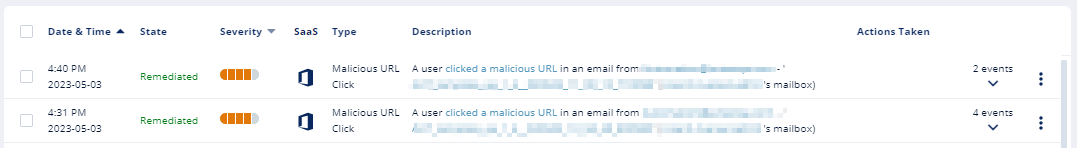
Viewing Emails with the Replaced Links
The Emails with Modified Attachments page shows emails with attachments, where the links in the attachments were replaced.
Note - The page does not show emails where links in the email body were replaced.
Viewing Replaced Links and User Clicks
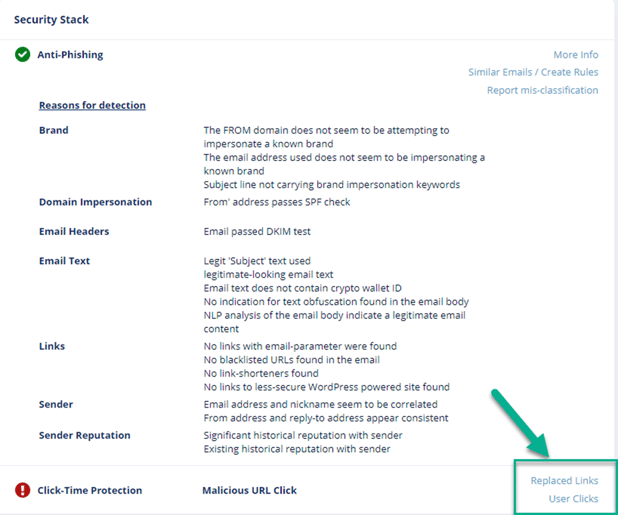
- From the Email Profile page
- Under Security Stack, for Click-Time Protection, administrators can view:
- Replaced Links - All the links replaced by the Click-Time Protection engine in the email body and its attachments
- User Clicks – All the clicks performed by users (for clean and malicious websites)
- Under Security Stack, for Click-Time Protection, administrators can view:
-
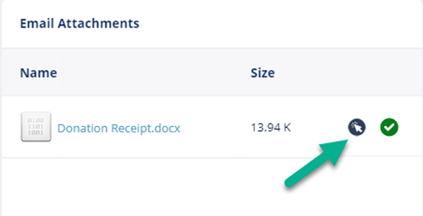
- Under Email Attachments, attachments with replaced links will be marked with a small icon.
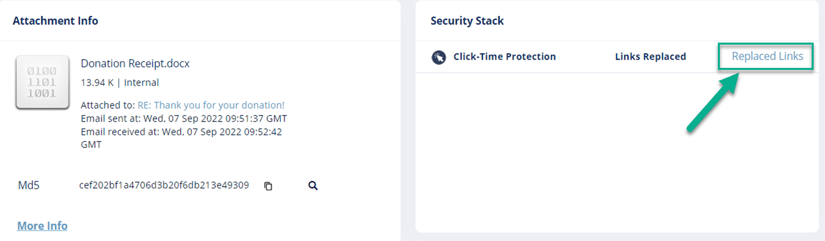
- From the Attachment Info page, administrators can see all the Replaced Links in the attachment.
Note - The User Clicks can only be seen from the Email Profile page.
Determining Which User Clicked a Link
Identification of the user that clicked a link is based on a cookie Avanan adds to the clicking user's browser.
Identification procedure:
- When a user clicks on a replaced link in an email sent to only one email address (click number 1), Avanan adds a cookie to the user's browser.
- If the user clicks (click number 2) on another replaced link in an email using the same browser within 30 days of the previous click, and the email is sent to the same email address, the user's identity will be linked to that browser.
- Click number 2 and all future clicks on replaced links (that are opened on the same browser) within the next 365 days will be attributed to the user, regardless of the number of email recipients.
- After 365 days from click number 1, the cookie is removed from the browser, and the procedure restarts.
Example: Every row in this table describes a click on a replaced link by John Smith:
| Date | Email recipients | John Smith's browser | Reported clicked user | Why the user is reported as the clicked user? |
| 01 January 2023 | John Smith | Cookie is added | Undetermined | One click is not enough to determine the user as John Smith. |
| 02 January 2023 | John Smith Mary Brown James Wilson |
Cookie is still valid | Undetermined | Waiting for another click from this browser on links in emails with a single recipient. |
| 03 January 2023 (or any date before 30 January 2023) | John Smith | Cookie is still valid | John Smith | John Smith clicked the replaced link (click number 2) in an email (sent only to one person) using the same browser within 30 days from the previous click. So, John Smith is reported as the clicked user. |
| 20 February 2023 (or any date before 01 January 2024) | John Smith Mary Brown James Wilson |
Cookie is still valid | John Smith | As the cookie is still valid, John Smith is reported as the clicked user though the email is sent to multiple users. |
| 01 January 2024 | John Smith | New cookie is added | Undetermined | Now, as 365 days are complete from the first click (click number 1), the old cookie is removed, a new cookie is added, and the user identification procedure starts again. |