Email is not secure by nature, because email was never meant to be secure. The way email is used today — and its security needs — differs greatly from what its inventors intended.
Definition of Email Security
Email security uses AI and other filtering techniques to stop malware, phishing scams, and business email compromise (BEC). As malicious actors turn to cloud environments to exploit G Suite and attack Office 365, email security is a vast undertaking with no one-size-fits-all approach. Good email security begins with a comprehensive understanding of the threat and willingness to evolve as email usage continues to rise and change.
How Secure is Email?
Relative to modern computer technologies, email evolved slowly. It originated in MIT’s compatible time-sharing system in 1965 to store files and messages on a central disk, with users logging in from remote computers.
In 1971, the @ symbol was introduced to help users target specific recipients. In 1977, the “To” and “From” fields and message forwarding were created within DARPA’s ARPANET, constituting email’s first standard.
Infographic: The History and Future of Phishing
These advances created the conditions for spam prototypes, and in 1978 the first mass email was sent to 397 ARPANET users. It was so unpopular that no one would try it again for a decade. Email security became necessary in the late 1980s, when spam proliferated as a prank among gamers, and quickly gained prominence as a criminal activity.
Thirty years later, email is vastly more powerful and sophisticated, with the cloud connecting users and syncing files in real-time. These factors have incentivized malicious actors to send nearly 4.7 billion phishing emails everyday.
Phishing is one of the most prominent forms of cybercrime today. Hackers use social engineering techniques to fool even the most attentive employees into opening a malicious attachment, clicking on a malicious link, or disclosing credentials. 92% of malware is delivered via a successful phishing attack over email, enabling hackers to access corporate data infrastructures and steal millions of dollars or personally identifiable information (PII).
In reality, email security will never be 100%. Knowing this, hackers will never stop leveraging email as an attack vector — especially not when where are 190 Million Office 365 users and 1.5 Billion G Suite users sharing confidential information and documents to do their jobs. Those email providers protecting those users are responsible for the security of the cloud, but you're responsible for the security of your data in the cloud.
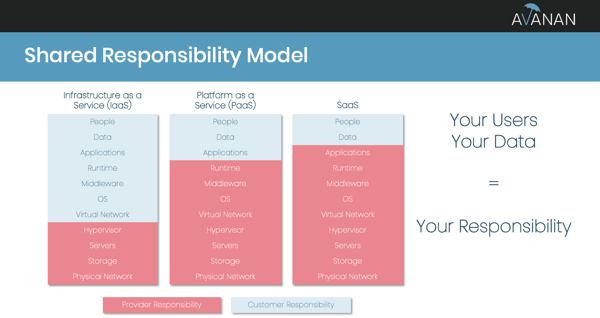
Why You Need Email Security
Email is the double-edged sword of the business world: it’s the enterprise’s communicative lifeblood, but that makes it the primary point of entry for hackers. All a hacker needs is one successful phishing email to open up opportunities for malware, ransomware, BEC, and other attack methods to obtain credentials and hold the organization hostage.
According to Canada's cybercrime task force, the Internet and Crime Complaint Center (IC3), both the number of complaints about cyberattacks and the financial loss of the attacked businesses have steadily increased over the past few years. In 2018, the IC3 received over 350,000 complaints (50,000 more than the year before) and financial losses nearly doubled from $1.4 Billion to $2.7 Billion. That's why phishing is a top concern for security professionals, according to survey results from 451 Research.
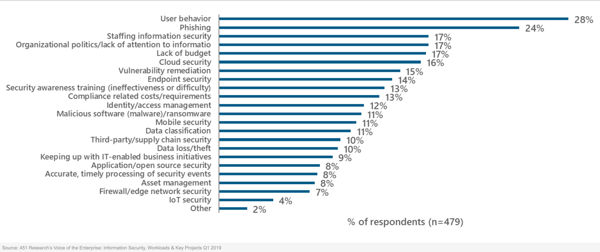
Although these statistics can be attributed to more reporting from increased user awareness, they also do not account for how many attacks go unreported — simply because victims don’t know about them until it’s too late. That’s one of the most insidious parts of email attacks: they allow the hacker to lurk in networks, observing systems and processes, waiting for the right moment to strike — and implicating potentially anyone and anything ever associated with the comprised account. Even business partners and clients are vulnerable.
The average cyberattack costs a small company $200,000, effectively putting it out of business. Given the stakes of poor email security, it’s jarring to see how many businesses around the world are unprepared for email attacks.
How Does Email Security Work?
Today’s cloud environment means email security must go beyond the capabilities of most Secure Email Gateways, which were originally designed to protect on-premises email. In a cloud environment, email security must prioritize anti-phishing, anti-malware, and anti-spam capabilities. With email integrated into applications and file sharing, business collaboration suites like Office 365 and G Suite presents hackers with multiple entry points and exploits once inside systems — which also means that email security must include mid-attack measures, like compromised account detection and access management tools. Email security must also offer full-suite protection. It should connect to the native API of cloud email providers and associated SaaS/productivity applications, like OneDrive and SharePoint.
Key capabilities of the anti-phishing, anti-malware, and anti-spam email security market start with content inspection tools, like a network sandbox, an isolated environment that mimics end-user operations and file detonations. The network sandbox allows for the proactive determination of malicious content, which administrators can disarm and reconstruct. In the actual environment, URL rewriting detects malicious links (sometimes rebranding the links so that end users can see that security has done its job) and performs time-of-click analysis.
Every email security solution should scan attachments in messages must be scanned before being passed through to their recipients. It’s far too easy, for instance, for hackers to embed malware in an attachment. Hackers also use attachments to execute various Business Email Compromise schemes, like false invoices.
In that case, the hacker might have breached the company accountant and pretended to be them while emailing an unsuspecting employee asking them to sign off on a doctored invoice. If the forged email is reasonably good, and if the recipient of the email is working quickly and expecting the invoice, there may be no way to stop the scam — unless the email security system detects a blemish in the attachment.
Web isolation services prevent malware and phishing threats while allowing broad web access by isolating potentially risky traffic. But phishing attacks and BEC need to be stopped with more targeted security measures, like display name spoof detection, domain-based message authentication, lookalike domain detection, and anomaly detection. Together, these features identify compromised accounts.
The most adapted email security connect to the cloud via APIs and use artificial intelligence (AI) to detect communication patterns and relationships between employees and customers.
With this data, the solution uses a threat detection algorithm and machine learning to prevent hackers from weaponizing the email suite in an account takeover scenario. This ability to gather real-time and historical data on every user, file, event, and policy — not only of internal accounts, but everyone who has access — allows for a seamless threat protection protocol. Solutions that adapt each specific business environment are ideal compared to one-size-fits-all vendors whose product works the same for every customer.
Email Security Policies
The first step to securing email is writing solid email security policies. This begins with developing a complete understanding of incoming email to the company. What are routine communications between clients, partners, and the organization?
To define this, the email security solution should learn the environment rapidly and over time using protection for links, attachments, and suspicious subject-lines, sender behavior, and language within the email.
Smart email security policies should then clearly define what happens next in a workflow, but create enough flexibility with the policies to meet the organization’s needs. For instance, should all suspicious content be sent to the spam folder or quarantine folder for review? Should it be separated from the message, which can otherwise continue through?
Suspicious content needs to be sent to a secure location for detailed analysis. If a threat is detected, the policies should state an action item for investigating the scope of that specific threat, and for determining if it has affected other parts of the cloud infrastructure.
Finally, once the entirety of the malicious activity is uncovered, there need to be policies around reinforcing encryption and safeguarding from future attacks. But what decisions guide changing existing policies and created new ones?
A good first step to email security policies after a breach is to analyze the originally breached email with full headers and original attachments, so that you can examine IP addresses. It’s equally as important to examine click patterns, both as recorded by systems and as practiced by the user. What was the user thinking when they encountered the phishing email? Did the user notice any suspicious activity around that time?
Once you’ve gained a thorough understanding of the incident, seize the opportunity to take smart account cleanup measures. Changing passwords is a must. Keep track of the active session for affected users, to ensure that the hacker isn’t still able to access the network through a legitimate channel like a VPN. Check mailbox configurations to see if the hacker changed them during the compromise. Finally, naturally integrate more targeted security tools into email and associated applications that end-users rely on everyday, so that business can keep on humming in an even more secure state than before.
End User Best Practices for Email Security
The best email security practices blend seamless protection for users and the reinforcement that protection is there. All users should know a few simple tactics for securing their accounts from the onset — the equivalents to not leaving the front door to the home unlocked. But they should also know that their organization has installed email security defense.
Strong Passwords
A strong password is the absolute bare minimum of email security — yet analysis of breached accounts shows that millions of users still choose bad passwords like “123456,” “qwerty,” “password,” or their first name.
In today’s world, when the average business user needs 191 passwords, password managers are a savior. Password managers like LastPass generate passwords for you, and store them in secure environments, reinforcing that the best password is the one you don’t know.
2-Factor Authentication
2-Factor Authentication (2FA) involves account log-in confirmation, like when a user receives a text or email asking if they’re trying to log into their account. These are the most well-known — but least secure — forms of 2FA. 2FA is a part of multi-factor authentication (MFA), and although MFA is not foolproof, it’s another baseline email security measure, one that can catch the fallout from a weak password.
Types of Email Security
With email always evolving, the types of email security must always evolve. Legacy security solutions need to be updated for new environments, and new solutions must prove their viability. In general, all the types of email security fall under the two main stages: pre-delivery and post-delivery delivery.
Anti-Phishing Behavioral Conditioning
An understandably common-sense anti-phishing solution is to raise awareness among employees. If an end-user knows of the dangers of phishing, why would that click that unfamiliar link?
However, research shows that limitations of that defense. One study showed that although 78% of 1700 participants knew of the risk of unknown links infecting their computers with viruses, up to 56% of email users clicked a malicious link. Why? They were curious.
Anti-phishing employee training can’t prevent phishing attacks. But a more specific type of anti-phishing behavioral conditioning can be taught, particularly in the platforms pioneered by KnowBe4. Employees can be trained to spot suspicious email activity and be equipped with user-friendly tools for reporting. These reports can be valuable to a security operations team tasked with monitoring threats, containing them if initiated, and analyzing them for future preventative measures.
Pre-Delivery Protection
Secure Email Gateways
A Secure Email Gateway is a longtime staple of email security. Because they were built for on-premises email environments, they were designed to be a firewall for email, and remain that way today. With this approach, a Secure Email Gateway rejects spam, prevents data loss, inspects content, encrypts messages, and more.
Secure Email Gateways protect inbound and outbound messages — but email today does far more than send and receive messages. By connecting to file sharing suites and essential workplace applications, email links every facet of a user’s online identity. Without an add-on at an extra cost, a Secure Email Gateway cannot see these essential elements of daily use, so it cannot secure them.
Another problem with Secure Email Gateways is that they are lighthouses for hackers. To reroute email through a Secure Email Gateway, an organization must change their MX records to that of the gateway. Hackers know this, and have found a massive loophole in this deployment mode to send malicious content directly to employees. Publicly available on sites like MXToolbox, hackers identify what vendor an organization uses to secure their environment, identify the root domain, and bypass the scan of a specific Secure Email Gateway.
Post-Delivery Protection
What kind of organization needs this new type of email security that scans inside the perimeter? One that requires on-demand scanning of mailboxes, generally as a secondary scan at low-use times; wants to quickly manage outbreaks that spread through email; demands detection methods that use historical communication patterns (for example, to build social graphs in defense against phishing); has substantial intra-domain email traffic without routing through an SEG; uses applications that have programmatic access to the mail server; and has users who regularly post messages in public folders. These solutions integrate well in modern email environments.
Cloud Email Security Supplement
Cloud Email Security Supplement (CESS) is a term coined by Gartner analysts to describe new measures needed in the emerging continuous adaptive risk and trust assessment (CARTA) approach to cyber security. According to Gartner, CESSs apply this to email security in particular: “CESSs focus on specific threats, often in the realm of hard-to-detect phishing, and can leverage full access to cloud-hosted inboxes via APIs for detection and remediation.”
The fact that this subset of API-based email security uses intelligence from existing security gives them a leg up on gateways — which require you to deactivate built-in security. But all of these solutions need emails to arrive into the inbox before security scans can begin. This delay in scanning means that business end-users have a small window to click on a phishing email.
As their name suggests, CESS solutions may for now be supplemental ways of protecting the entire Microsoft Office 365 suite, for instance. But once in place, the organization can affirm that the CESS satisfies all required security protection and risk avoidance, which can lead to email security consolidation — and a substantial cost savings.
M-SOAR
Another important Gartner term in email security deliver is Security Orchestration, Automation, and Response (SOAR). This refers to a solution stack that can be applied to compatible products and services, which helps define, prioritize, standardize, and automate incident response functions.
Recently, at Gartner’s Security & Risk Management Summit, Mario do Boer, a specialist in endpoint, malware, and email/collaboration security, introduced M-SOAR — Mail-focused SOAR — as a way of focusing exclusively on email threats, as opposed to orchestration. M-SOAR is a capability at the intersection of email gateways, awareness/training, and solution software for collaboration suite security — an email security capability that too few organizations currently have.
API-Based Security from Avanan
Avanan has a few things in common with these vendors, but has one key difference. Its API-based email security architecture enables the scanning of incoming emails inside the perimeter, but before they reach the inbox. Once the email is cleared by the security stack, it can arrive to the inbox or leave the organization — safely.
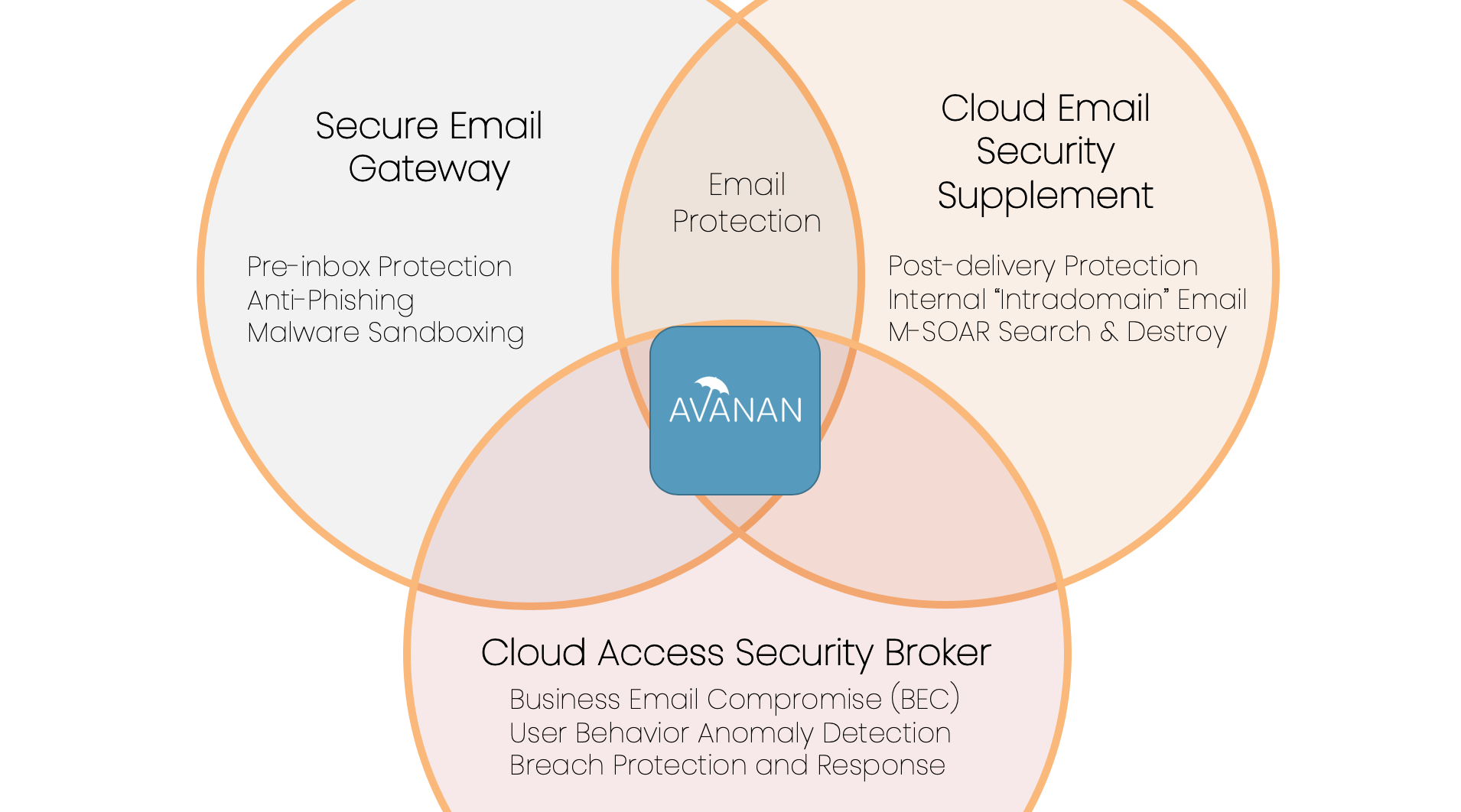
API-based methods are built for modern cloud environments. Industry analysts support that this new method of email security is better-suited to identify and stop cloud-based threats. According to Gartner, “Non-gateway solutions that integrate with the SaaS server/service [via API] are in a better position to detect communication anomalies, as well as to protect internal email…” The surge of these solutions in the market the last few years reinforces this position.
Get a FREE trial of Avanan and take your email security to the next level







