Email is used by 3.8 billion people every day, and its popularity is only growing. Unfortunately, that makes it the favorite channel for opportunistic and targeted attacks. Secure Email Gateways have been a critical email security tool against email hackers.
The prevalence of multi-vector attacks using evasion techniques such as encryption and anti-forensics are rendering the old core capabilities of anti-spam and signature-based anti-malware insufficient. Today, for instance, 35% of client organizations that move to Office 365 are supplementing its natively available email security capabilities with a third-party product.
Secure Email Gateways were designed to secure on-premises email environments. In this capacity they were highly effective. As email has moved to the cloud, Secure Email Gateways have tried their best to adapt to the new environment but unfortunately have come up short. A tool designed around a clear perimeter can not secure modern email where this perimeter has shifted and multiplied.
Email threats that did not exist before the prevalence of cloud email are not detected by these legacy solutions and a complete reinvention of how email security strategy is necessary.
What is a Secure Email Gateway?
For on-premises email environments, a Secure Email Gateway utilizes message transfer agent (MTA) functionality to filter emails. Secure Email Gateways scan emails, determining whether they are phishing, spam, or malware. It either either blocks, quarantines, or passes emails onto the email platform’s built-in security scan — all before they are delivered to their intended recipient.
To secure cloud email, the Gateway connects outside of the email provider’s cloud environment via a proxy that reroutes the email through the Secure Email Gateway. If the Secure Email Gateway marks it as clean, the message is sent to the email provider, where the email is again scanned by the email provider’s built-in security.
How Does a Secure Email Gateway Work?
Secure Email Gateways are essentially firewalls for email. They reroute inbound and outbound email via proxy through its own agent, which then performs a scan of the email. The scan looks at different aspects of the email to decide whether it contains threats. If so, it filters the email.
Secure Email Gateways’ filtering technology uses dynamic threat intelligence feeds to determine which emails are malicious. These feeds may include blacklisted URLs, flagged keywords, or other suspicious qualities that suggest an email may contain a security threat.
Secure Email Gateways’ basic functions conform with the latest published standards: anti-spam and signature-based anti-malware; marketing and graymail classification; and personalized controls to manage these types of messages.
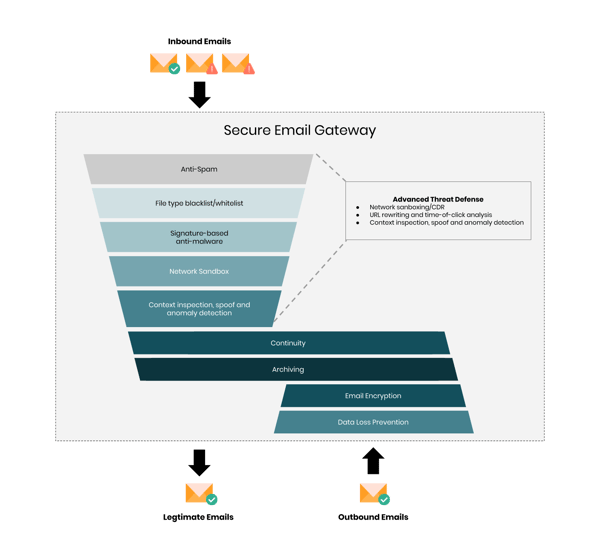
Network sandbox
A network sandbox is used to inspect attachments and URLs that the Secure Email Gateway cannot identify as benign or malicious using other methods. The network sandbox should cover an extensive set of file types (including zip, wsf, js, and macros that are commonly used in attacks) and embedded URLs. It should have strong anti-evasion capabilities and accurately identify malware that runs in a virtualized sandbox environment.
Content disarm and reconstruction (CDR)
CDR breaks down files into their discrete components, strips away anything that doesn't conform to that file type's original specification, and rebuilds a "clean" version that continues on to the intended destination. This real-time process removes zero-day malware and exploits, while avoiding the negative business productivity impact that is typically caused by sandbox detonation and quarantine delays.
CDR can be used as a supplement or replacement for network sandboxing, depending on the use case. Many recipients don't mind receiving a copy of a document that is visually identical to the original, but that does not contain any code. However, that is not the case for every user.
URL rewriting and time-of-click analysis
URL rewriting and time-of-click analysis secure URLs before they are delivered to the user. This provides stronger protection than time-of-delivery URL inspection. This technology can disarm the URL, making it non-clickable. Then, it replaces the URL with a text text warning ("embedded URL removed for security reasons") and redirects the link to the inspection service for time-of-click analysis protection. The Secure Email Gateway generally leaves URLs in attachments untouched, although several have this on their product roadmap.
Display name spoof detection
For imposter-based threats, display name spoof detection identifies spoofed messages based on email headers and the sender names. Some products support the fuzzy matching of sender names with a list of names that the email security administrator can set up. This is typically a list of VIP users.
Domain-based message authentication, reporting and conformance (DMARC) on inbound email
Enforce DMARC on inbound email traffic to protect internal users from receiving spoofed external messages from domains that have implemented DMARC in rejection mode. This also checks the alignment of the domains used in the FROM and MAIL FROM email addresses.
Anomaly detection
To thwart BEC attacks, this detects anomalous messages based on sender, recipient, envelope, content, history, and other context.
Graymail handling
This is an area where many Secure Email Gateways require further investment. Most products are capable of identifying graymail, which includes solicited bulk email messages that the recipient "opted-in" for at some point in the past. But many lack methods for end users to configure the handling of these messages based on their individual and subjective preferences.
Some attacks masquerade as graymail and hide a malicious URL in a seemingly innocuous unsubscribe link. A safe unsubscribe capability solves for this by effectively replacing the links in such messages with a secure one.
DLP and email encryption
Outbound email security features such as DLP and email encryption are critical for intellectual property (IP) protection and regulatory compliance (such as PCI and Health Insurance Portability and Accountability Act [HIPAA] data). That’s why more than 50% of organizations leverage the DLP and email encryption capabilities of a Secure Email Gateway.
Although they can be used separately, DLP and encryption are typically used in a complementary approach. Users should be provided with readily available email encryption options that empower them to make the right decision when handling sensitive data via email. However, if they inadvertently or intentionally fail to do so, then the DLP inspection engine for outbound messages can block or remediate this as a fail-safe.
Post-delivery Protection
These detection and response capabilities address threats that were not initially caught by the Secure Email Gateway and consequently landed in a user's inbox. Using API integrations with cloud email systems (such as Office 365) or plug-ins for email clients (such as Outlook), this technology "claws back" a malicious message, removing it from the user's inbox after initial delivery.
Since the message may have already been opened by the user, the capability should also be able to alert relevant personnel and products— such as an administrator, security operations center, EDR or security information and event management (SIEM) — about this potential compromise for remediation or recovery. As interoperability gets better between products, remediation actions can be taken in real time to decrease both incident response time and the level of human effort required.
Are Secure Email Gateways Viable?
As organizations move their email to the cloud and away from on-premises, Secure Email Gateways have become less reliable as a means to protect users from email-borne threats. This is largely due to the architecture of a Secure Email Gateway, which was originally intended for on-premises environments and was only later adapted for the cloud.
Secure Email Gateways are a critical protection technology, but the market is both highly saturated and very mature. Market growth has leveled off to low single digits, and differentiation between vendors boils down to just a few criteria. Additionally, there is a low percentage of revenue from new buyers, a low number of new entrants to the market, and a low level of vendor consolidation.
Email does much more than send and receive messages. It connects to file sharing suites, essential workplace applications, and links every facet of our online identity. The inbox-level protection that Secure Email Gateways provide simply does not suffice in this interconnected landscape.
Secure Email Gateways Only Secure Inbound and Outbound Emails
Since Secure Email Gateways connect to the mailflow outside of the email provider’s cloud, internal emails are not scanned for threats. In a cloud environment where account compromise is much more common because of credential access, internal emails can be just as threat-prone as inbound and outbound emails.
Some email gateways use journaling rules as a way to scan internal emails, but this method only scans emails post-delivery, and does not prevent the email from making it to the inbox. This does not adequately protect users from malicious internal emails, since the email is clickable by the recipient in the time between the delivery and the scan.
Secure Email Gateways Are Limited to Email
In a cloud environment, email is not the only entry point. File sharing, messaging applications, and other SaaS applications are all interconnected, providing additional avenues for threats to reach users within an organization. Unless the customer purchases an add-on, Secure Email Gateways do not have visibility to these connected applications and therefore can not identify threats in that part of the environment.
Secure Email Gateways Broadcast Themselves to Hackers
In order to reroute email through a Secure Email Gateway, an organization must change their MX records to that of the Gateway. This is public information through sites like MXToolbox, which enables hackers to design targeted attacks calibrated to bypass the scan of a specific Secure Email Gateway.
Alternatives to Secure Email Gateways
Supplement gaps (if replacement is not an option) in the advanced threat defense capabilities of an incumbent SEG by adding a specialized product tailored for email security.
Given the limitations of securing cloud email with a Secure Email Gateway, many organizations have opted for alternative solutions to fight phishing and malware. According to Analyst Firm Gartner, the most promising of these solutions is a CESS or Cloud Email Security Supplement. A CESS supplements the default security by connecting within the cloud environment via API and scanning emails after the email provider’s built-in security scan. This has several advantages over the proxy method utilized by Secure Email Gateways.
Firstly, by scanning after default security of the email provider, the CESS fully utilizes the built-in security features. (Secure Email Gateways scan before default security). This allows CESS scans to focus on more sophisticated phishing attacks that are designed to bypass the filters in place by Office 365 and Gmail.
Secondly, by connecting to the cloud environment via API, CESS solutions can extend their security beyond just inbound and outbound emails to scan internal emails as well as other SaaS applications such as messaging and file sharing applications.
Finally, deploying a CESS requires no change to MX records, which not only makes the deployment process substantially faster (only a few minutes, rather than the weeks required for a Secure Email Gateway) but also results in the security being completely invisible to hackers. No one can see what security you are using so they can’t design attacks specifically to bypass it’s scans.
Why is a Secure Email Gateway Important?
Secure Email Gateway attempts to solve for the biggest security issue facing organizations: phishing attacks. The vast majority of threats to an organization’s security come in the form of phishing attacks and the short-comings of built-in security solutions necessitates an additional security scanning technology to prevent attacks from reaching the inbox.
Although Secure Email Gateways were the preeminent email security technology for on-premises email, in a cloud environment they are often not a complete solution. “A traditional security appliance vendor says you can use their firewall or web gateway on cloud infrastructure. These products are virtual appliances of the original hardware spec and are not architected to be delivered from or in the cloud and are often minimally featured.” (Verizon 5 Considerations for Evaluating a Modern Enterprise Security Platform, 2019)
Why Avanan
Avanan catches the advanced attacks that evade default and advanced security tools. Its invisible, multi-layer security enables full-suite protection for cloud collaboration solutions such as Office 365™, G-Suite™, and Slack™. The platform deploys in one click via API to prevent Business Email Compromise and block phishing, malware, data leakage, account takeover, and shadow IT across the enterprise. Avanan replaces the need for multiple tools to secure the entire cloud collaboration suite, with a patented solution that goes far beyond any other Cloud Email Security Supplement.
Using the multi-vendor, open platform solution from Avanan lets organizations customize protection with preconfigured components selected from trusted security providers.Due to the patented in-line scanning technology, Avanan offers a cloud-native platform well-suited to supplement or replace the need for a Secure Email Gateway.