What is BEC? There is ambiguity about what Business Email Compromise (BEC) means. Is it an email impersonating an executive for financial gain? Is it the same thing as account takeover? Or is it what happens before the takeover?
It’s best to think of BEC as an umbrella term. BEC is the entire act of getting a user to be compromised in some way; it’s much more than an invoice scam or impersonation of a senior executive. BEC often combines phishing techniques (like social engineering) with malware and domain spoofing, making it particularly difficult to thwart. The end result of every BEC attack is to get a business email user to do something they shouldn’t — like divulge their Microsoft account credentials or wire money to a bank.
In 2019, BEC is one of the most pervasive forms of cybercrime. The FBI has labeled it a $26 Billion global scam, and Gartner has designated it a top-10 security project. It affects organizations of all sizes, in all industries, and it victimizes executives and regular employees alike. BEC has fooled Google and Facebook for $100 Million and a small church in Ohio for $1.8 Million.
At its most effective, BEC will dupe business users who have received security awareness training. For this reason, organizations must understand how BEC works (and why it succeeds) so that they can stop BEC before it starts. Email security and business process controls are important first steps.
How Does Business Email Compromise Work?
Like most email-based attacks, Business Email Compromise relies on deception, takes clever planning, and requires patience. What separates BEC from other scams is how it exploits trust.
Pulling off the scam means that all BEC hackers, regardless of the nature of their ultimate attack, take a few common steps.
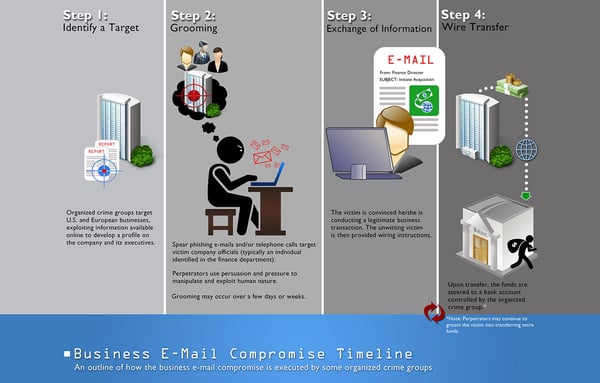
Identifying the Target
In the first step of a Business Email Compromise scam, the cyber criminal searches for a target using publicly available information. They identify a potential victim company online, and then get a deep and accurate understanding of it on their About page and LinkedIn company profile, which links to the profile of their employees.
From there, they learn the names of company executives, particularly, the CEO and CFO. But they may also pay attention to other employees in finance or HR, and may scour social media accounts, blog posts, or images freely available online.
Compromising Email Accounts
Once the hacker decides which company to attack, they attack the company’s email environment through a variety of methods: social engineering, spear phishing, malware, keyloggers, or brute force. Their mission is to obtain the password of the initial victim, often the CEO, which effectively compromises the email account most responsible for the business. (BEC is sometimes referred to as “CEO Fraud” or “whaling,” a reference to the biggest catch in the sea.)
Domain and Nickname Spoofing
But what really makes BEC so widespread is that a hacker doesn’t necessarily have to go to these impersonation lengths to finally execute the scam. A BEC scam could also involve the malicious actor sending a fake email from a legitimate email account.
Hackers will often modify the domain in the email address of a partner or trusted sender by a single character. For instance, deleting a letter that appears twice in a word, or substituting a lowercase “L” with an uppercase “i,” which results in the usually-indistinguishable “l” from “I”. These spoofed domains are sometimes referred to as cousin domains.
Not only can these modifications be extremely difficult to detect at a glance, but if the victim opens the email on a mobile device the entire domain may not even appear on screen.
Surveilling Potential Victims
At this point, the hacker has already committed a crime. But the real victim comes next: the employee targeted by the hacker as the one who will wire funds or disclose information upon the “CEO’s” (or someone else with leverage at the company) request.
To find this victim, the hacker may spend weeks or months surveilling business processes and partners before settling on a victim. Quickly choosing any junior employee could be counterproductive and backfire. That person — for example, an accountant — could be a scrupulous by-the-book employee who has flagged dozens of emails to IT for fraud and always double-checks the CEO’s financial requests with the CFO and accounts payable.
Learning the company’s daily routines and schedules and studying internal and external communication habits will instead help the hacker discover exploitable business processes.
Executing the Scam
Having absorbed the company’s employee roster and email patterns, the hacker finally executes the BEC scam. This almost always comes in the form of a direct email to a direct report.
The three most popular keywords in a BEC email are urgent, request, and important. All are used in an attempt to create a mix of fear and subservience in the victim.
The hacker may also try to catch both victims in a lull. One strategy is to send the email while the CEO is on vacation and the junior employee is running from meeting to meeting. This minimizes the chance that the employee will look closely at the forged email or bother their boss to see if they really did just send an email instructing them to wire funds to a supplier at a new account number.
Types of Business Email Compromise
The term Business Email Compromise has a broad meaning, encompassing a handful of types. The types may slightly overlap with one another, and even be derivative of one another, but they also stand alone because they have proven to be unique effective attack vectors.
Account Takeover
Account takeover is one of the most devastating forms of Business Email Compromise. An account takeover occurs when a criminal acquires login credentials and breaks into the email account.
This often happens through a phishing attack, but credentials can also be purchased on the dark web. The criminal then moves to control the account by changing the password or forwarding the mail to a new account, giving them the ability to monitor all account activity.
Account takeover may not generate the same headlines as large-scale malware or ransomware attacks. But that’s because it happens silently, which can make it even more dangerous. Criminals can lurk in systems for months undetected, learning the communication patterns of a victimized business.
User Impersonation
User impersonation is similar to account takeover, but it operates in a professional sense. Among the most common versions of user impersonation is attorney impersonation, where the fraudster identifies a business in litigation and impersonates their legal representation. Once the hacker compromises the firm’s email account, they will email their client with the aim of “verifying” the account where a settlement is to be transferred. From here, they can divert the funds into their own account.
Partner Impersonation
Partner impersonation is an even more specific variant of user impersonation, where the scammer compromises the email account of a supply chain partner or impersonates their domain with a cousin domain — like company.co instead of company.com. These scams can be particularly tough to recognize because they take advantage of a business’s relationships with multiple vendors.
Furthermore, they can prey on hectic situations, where a business needs or is already expecting a product immediately, and the employee responsible may be under pressure and not in a position to pay too much attention to legitimate-looking, credible-seeming requests for wire transfers to new accounts. Also, they are dangerous schemes because of how easily the hacker can pose as multiple vendors at once.
False Invoice Schemes
A false invoice or billing scheme operates in the same arena as the partner impersonation scheme, harnessing the power of a legitimate invoice to make its exploit, which is what makes it difficult to detect and costly when well-executed.
In a false invoice scheme, the fraudster usually compromises the account of someone who works in a business’s financial department, like an accounts manager. Once they find a legitimate invoice, they alter the bank account numbers. Then they have a number of options: increasing the payment amount, creating a double-payment, intentionally sending the invoice to the wrong vendor and keeping the returned sum.
However it happens, the false invoice scheme requires the hacker to use email to impersonate the accountant, the vendor, or both—techniques the hacker can use in other prominent billing schemes, the ones that rely on shell companies, and the ones that make fraudulent purchases with organizational funds.
Data Theft
Typical data theft BEC scams operate like all the others, but are relegated to the hacker victimizing HR employees who have access to personally identifiable information (PII)—email addresses and phone numbers; social security, passport, and driver’s license numbers; bank accounts and tax forms.
Who Does Business Email Compromise Target?
According to the US Treasury’s Financial Crimes Enforcement Network (FinCEN), Business Email Compromise targets all types of institutions, from financial to educational to healthcare, as well as governments, non-governmental agencies, and nonprofits—especially any organization with publicly available information, which gives the hackers an edge as they research their targets.
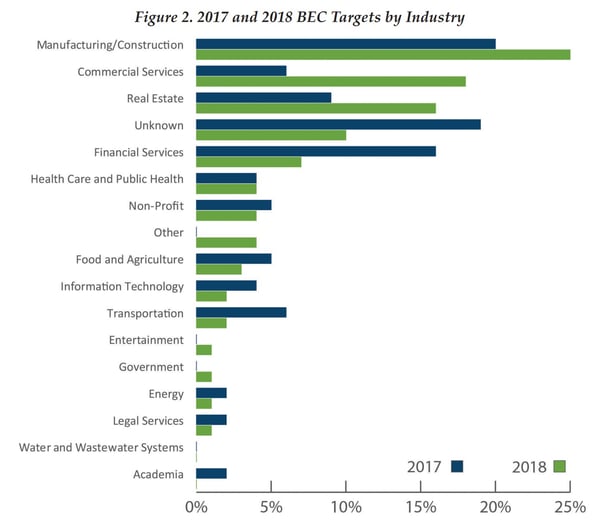
As of late, the top-three most-targeted industries are manufacturing and construction (25%), commercial services (18%), real estate (16%); ones where multiple vendors, suppliers, and contractors work together on multiple, oftentimes decentralized, projects.
The Payroll Diversion Scheme
A signature characteristic of BEC is constant evolution until a scheme taps a goldmine, followed by milking that scheme before the authorities finally crack down.
For instance, recently there has been a significant uptick in payroll diversion scams. The specifics of this scam involve a compromised business email account emailing the payroll or human resources department to request a change in direct deposit information. If approved, the money usually flows into a fraudulent prepaid account.
For years, the FBI’s Internet Crime Complaint Center (IC3) fielded minimal reports of payroll diversion for years. Then, from January 2018 until June 2019, the IC3 fielded over 1,000 payroll diversion complaints. The 18-month surge represented a 815% increase in this particular scheme. Losses totaled $8.3 Million, with an average of nearly $8,000 per complaint.
The History of Business Email Compromise
The FBI is the lead federal agency for investigating cyber attacks, and the IC3, which was founded in 2000, fields complaints and issues public notices about them. But the IC3 didn’t start tracking Business Email Compromise until 2013, and in 2015 it still considered BEC just an emerging global threat.
But from May 2018 to June 2019, there was a 100% increase in total global exposed losses from Business Email Compromise. Altogether, since the IC3 starting counting, there have been 166,349 domestic and international incidents reported, totaling $26.2 Billion in total exposed losses. BEC has been reported in all 50 US states and in 177 countries.
The good news is that Business Email Compromise investigations have produced results. In 2018, Operation WireWire, a multi-agency, multi-country international BEC operation, resulted in 74 arrests, nearly $2.4 Million seized, and approximately $14 Million in fraudulent wire transfers disrupted and recovered.
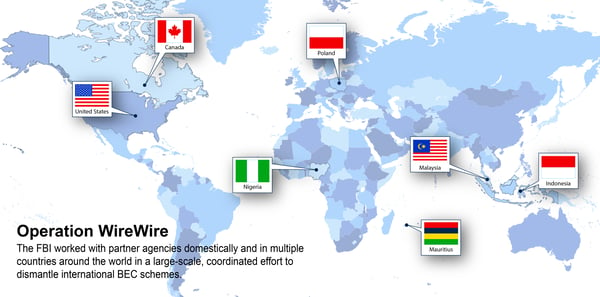
And a year later, Operation reWired went further, arresting 281 worldwide, seizing $3.7 Million, and disputing and recovering approximately $118 Million in fraudulent wire transfers. All in all, the IC3’s Recovery Asset Team (RAT) boasts a 75% recovery rate for stolen BEC funds.
Of course, it’s better to stop a crime before it gains momentum.
How to Prevent Business Email Compromise
In a cloud environment, organizations are especially vulnerable to Business Email Compromise. Employee awareness is a good start, but with BEC actors willing to spend months learning the habits of a single victim and building networks of money mules amid technological and logistical infrastructure, a comprehensive technological defense is in order.
The essence of preventing BEC in a cloud environment is a robust Cloud Email Security Solution. A reliable vendor would include all kinds of monitoring (event, shadow IT, shadow SaaS) with risk reporting; data classification, management, and encryption; and detection (phishing, malware, advanced threat).
Here is how email security providers help prevent Business Email Compromise specifically.
Behavioral Analysis/Account Takeover Detection
BEC fraudsters are so sophisticated and have so many cloud applications as entry points, that simply monitoring emails to look for signs of account compromise is insufficient. Instead, solutions have some form of anomaly detection. It analyzes user logins and activity events across all applications for signs of suspicious behavior.
The key to account takeover protection is pattern analysis. For instance, user logins from new browsers, devices, and locations are a potential sign of suspicious activity. If a hacker does access an account, they may reconfigure the mailbox by deleting all mail, filtering it, or forwarding it to an outside account. The security solution should alert instances of suspicious configurations like these.
Hackers may disable multi-factor authentication, reset passwords, or change contact groupings in a short period of time. If they are operating from another country, then the hacked account may be active at unusual times, like the middle of the night, for unusual periods of time. Monitoring session characteristics is key to takeover detection.
Access Control
User and entity behavior analytics (UEBA) is the analysis of user activity data from logs, network traffic and endpoints. Understanding and correlating this data with threat intelligence to identify activities — or behaviors — likely to indicate a malicious presence is part of a sound process to thwart BEC attacks.
The key aspects of UEBA include an understanding of user login locations (e.g., log-ins from locations too geographically distant as to be reasonable in a short period of time, often called a “Superman Attack”), suspicious mail-forwarding rules (like forwarding all mail to an external account), and user activity aberrations (e.g. a user who normally sends 50 emails per day sending 500 in one day).
Impersonation Detection
With impersonation detection, all aspects of an email—header, sender, attachments, keywords—are instantly scanned for content abnormalities. Special attention is paid to new domains and external addresses, and controls are in place to thwart looks-like and sounds-like domains.
DLP
Data Loss Prevention (DLP) security measures consist of tools that prevent employees from emailing sensitive information to malicious actors. This is especially important in a cloud environment, where file sharing among internal and external users is inherently frictionless. Employees benefit from enhanced workflow capabilities, but they risk accidentally or unknowingly sharing sensitive information with seemingly trusted confidants — possibly even those who have been victims of Business Email Compromise.
Today’s cloud environments need AI- and ML-enhanced DLP practices to protect against the most sophisticated BEC schemes. When an email is sent, DLP software scans it, checks it against a set of rules, and encrypts it instantly. The rules should be universal across multiple cloud applications, while still being specific enough for individual departments.
For instance, HIPAA email compliance is relevant not just to healthcare businesses but to any HR department that stores employee health information. DLP software must ensure that if HR emails healthcare-related PII, it is going to a trusted, uncompromised recipient.
Payment Verification
In the end, BEC is always about exploiting trust to steal money. It tricks one employee believe they’re directing funds to a legitimate person or entity. Not having a form of payment verification in place increases the likelihood that this final step of BEC will succeed.
Successful payment verification solutions should be out-of-band (OOB). For instance, whenever a payment is requested, a text message can be sent to the requester. These are forms of multi-factor authentication (MFA). MFA isn’t foolproof—nothing is—but it can be the final safeguard against a hacker who’s made it that far.
Avanan: Preventing Business Email Compromise
Avanan uses anomaly detection and a patented antiphishing algorithm (called Smart-Phish) to stop BEC and nickname impersonation.
Resources
https://www.ic3.gov/media/2019/190910.aspx#ref1
https://www.gartner.com/smarterwithgartner/gartner-top-10-security-projects-for-2019/
https://www.nytimes.com/2019/03/25/business/facebook-google-wire-fraud.html
https://www.statista.com/statistics/983167/top-bec-email-keywords-used-worldwide/
https://pdf.ic3.gov/2018_IC3Report.pdf
https://www.fbi.gov/news/stories/business-e-mail-compromise-on-the-rise
https://www.fbi.gov/news/stories/business-e-mail-compromise
https://www.fbi.gov/news/stories/international-bec-takedown-061118
https://www.fbi.gov/news/stories/operation-rewired-bec-takedown-091019
https://www.hipaajournal.com/hipaa-compliance-for-email/