Hackers are using Microsoft Azure Blob Storage to specifically attack Office 365 admins to take over the Office 365 environment. Although windows.net phishing attacks surfaced late last year, this is the first instance we have tracked where hackers are validating the Office 365 credentials and providing an end-to-end genuine experience. Even after being hacked, the most advanced IT admin will not know their account was compromised.
What's interesting about the Office 365 credential validator attack?
We have seen this attack going specifically after IT managers and Office 365 admins. That’s probably why every step of this attack mimics the Microsoft Office 365 experience: the nickname, the subject, the email body, the Microsoft-owned URL (with a malicious link), the validation of login information, the failed login error messages, and the end-result of a successful login: redirection to the victim’s real Office 365 inbox.
- The hacker uploads an Office 365 fake login page to Microsoft Azure Blob Storage and gets a link in Microsoft’s windows.net domains, which have a valid Microsoft SSL certificate. This is the first step in convincing the recipient it is a legitimate Microsoft page.
- The hacker HTML page includes a script that validates the Office 365 credentials by triggering a back-end IMAP client that tries to login in real-time.
- If login is successful, the hackers immediately start syncing the victim’s emails to a remote client via IMAP protocol, while the victim’s browser directs to the real Office 365 portal. This provides a genuine “conclusion” to the attack so that the victim isn’t aware of the account compromise.
- If the login fails, the end-user is presented with a fake Office 365 login error, asking them to provide their credentials again — as they would in a genuine Office login. This method is something we have not seen before.
Real-time account compromise attacks open the door for hackers to make instant configuration changes, mailbox deletion, or organization-wide password resets.
Immediate Recommendations to Protect Office 365
Enable Multi-Factor Authentication (MFA) for all users — especially admins.
- Under specific circumstances, IMAP can bypass MFA. Disable IMAP access globally if possible, particularly for admins.
IT employees should not have admin access for their day-to-day account. It is recommended to have two separate Office 365 accounts: one for admin purposes, another for everyday use.
- To take this a step further, the admin account should not have a licensed mailbox. This separation of duties will hinder hackers.
Educate your users that windows.net, though a Microsoft own domain, is open to anyone. Genuine logins to Office 365 are expected to be in microsoftonline.com
Office 365 Credential Validator Attack Methodology
1. The victim receives a spoofed Office 365 quarantine notification.
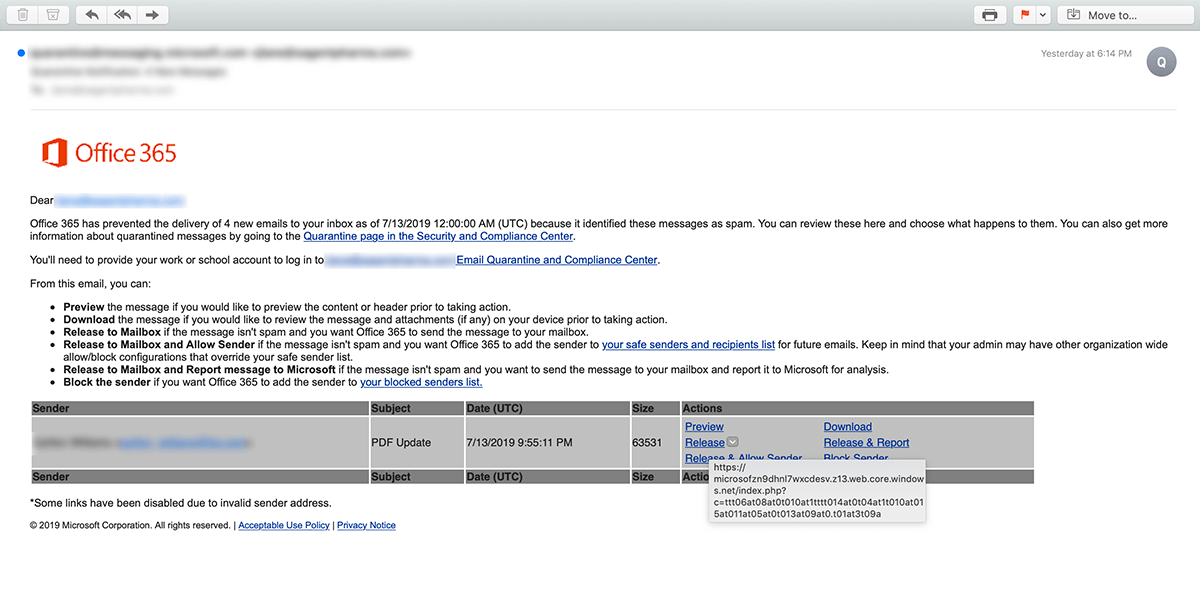
2. They click “Preview” or “Restore.”
All of the links in the email point to an Azure blob under windows.net, and lead the admin to a spoofed Office 365 login page.
For example:
3. The victim enters their credentials.
In standard phishing attacks, submitting to the spoofed login form takes no more than two seconds. In this attack, it takes 10 to 12 seconds, because the PHP script actually validates the credentials against Microsoft.
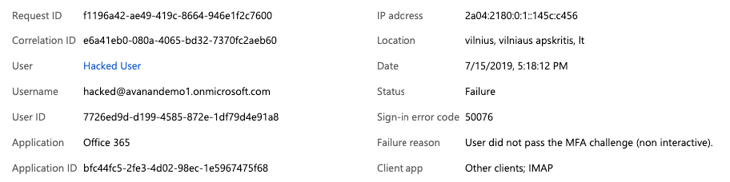
From our testing of the attack, this is a MSFT log for a login attempt from Italy using an IMAP client. In this account, we also enabled MFA, to demonstrate that it prevents hackers from compromising the account.
4. The victim is redirected to their outbox at outlook.office.com.
After a successful login, the admin never knows they were hacked.
Conclusion
This attack marks a point in phishing evolution. Hackers target IT managers to gain admin access to take full ownership of the domain, apply configuration changes in the admin console, delete mailboxes, forward mail, etc..
User training just became harder. Users who have completed phishing training know that they can confirm if a login form is suspicious by entering fake passwords multiple times. If the page accepts the invalid password, then it’s harvesting credentials. In this attack, that training doesn’t work because fake credentials are not accepted.