What is Phishing?
The first mass email in 1978 was sent to just under 400 users. That seems quaint, now. It would be ten years before mass emailing turned into something more pernicious. That was 1988, when multi-user dungeon game players flooded rivals’ emails with junk, which crashed the system. The goal was to prevent rivals from playing.
By the 1990s, the evolution turned into something quite dangerous. Random credit card generators, started by the Warez community, spawned the first wave of attacks. They used randomly generated credit card numbers to open AOL accounts, and then used hacked accounts to send even more phishing messages to the victim’s contact list.
What followed was the start of the cat-and-mouse game of cybersecurity, whereby providers respond to an attack, only to see hackers respond to that new protection. In 1995, AOL responded by implementing new measures to stop the use of random credit-card generators, hoping to stop the problem. But Warez had a new scam up their sleeves. They posed as AOL admins, requesting login credentials and then using those hacked accounts to send even more phishing messages.
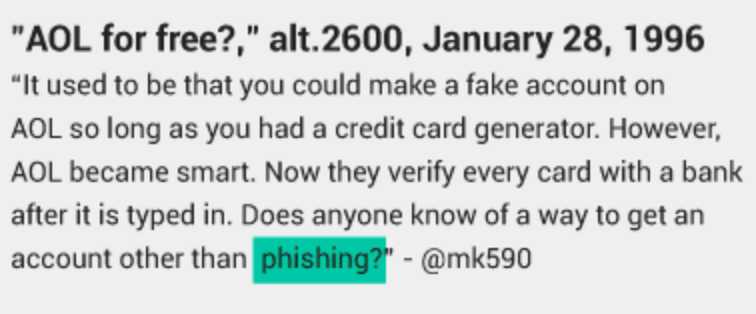
All of this led to one inquiring mind to ask on an AOL message board: “Does anyone know of a way to get an account other than phishing?” It is believed to be the first use of the word phishing.
A phishing scam, then, is when a hacker pretends to be a trusted person in order to access a user’s account, then tricking them into giving up sensitive or personal information, or infiltrating the larger network. Avanan's 2019 Global Phish Report found that one in 199 emails are a phishing attack—one in 25 branded emails are a phishing attack. Further, over 50% of all phishing emails have malware in them; 40.9% are designed for credential harvesting, while extortion of some kind makes up 8%.
It is a real threat that requires a sophisticated solution.
How Does Phishing Work?
Depending on the sophistication of the attack, phishing can either be super-simple to notice or incredibly difficult to detect. In general, though, it is a personalized email, asking the recipient for information that would then be used to steal sensitive information. There are a broad range of attacks, from individual to large-scale. From Nigerian Prince scams, to malware or ransomware, to Business Email Compromise, these all prey on humans who are not trained, not paying attention or both. Both on-premises and cloud email environments are susceptible.
Hackers rely on secrecy, hoping to operate incognito and without victims reporting it to authorities. This is often the case—as many as 50% of phishing attacks go unreported.
More than anything, hackers are relying on humans thinking the email is legit. And because workers see so many emails and are often juggling multiple things, it can work. One study found that 45 percent of those who had fallen for a phishing scam cited distraction as the top reason for clicking. It’s why 89% of companies list phishing as their number one threat.
Hackers prey on this. A successful attack only takes one employee and so they time emails to when employees are most vulnerable—during emergencies, holidays and other major events. It’s why hackers have skyrocketed in their COVID-19 related phishing attempts, sending 18 million malicious messages a day related to the pandemic.
And though some phishing attacks are easy to stop, many still make it to the inbox, sitting ducks for users to click on them. Avanan has found that 25% of emails bypass Office 365 security and land in the inbox.
How to Stop Phishing Emails with Avanan
Avanan was designed to stop phishing attacks, and in particular it was designed to stop the attacks that others miss. Most of today’s phishing attacks that hit end-users are zero-day threats. Avanan built a machine learning algorithm that analyzes each aspect of an email in order to best protect user inboxes.
Its security layer runs after the default security filter that Microsoft and Google offer. Avanan then leverages Artificial Intelligence to be trained on the data, so that it is tuned on the attacks that others miss.
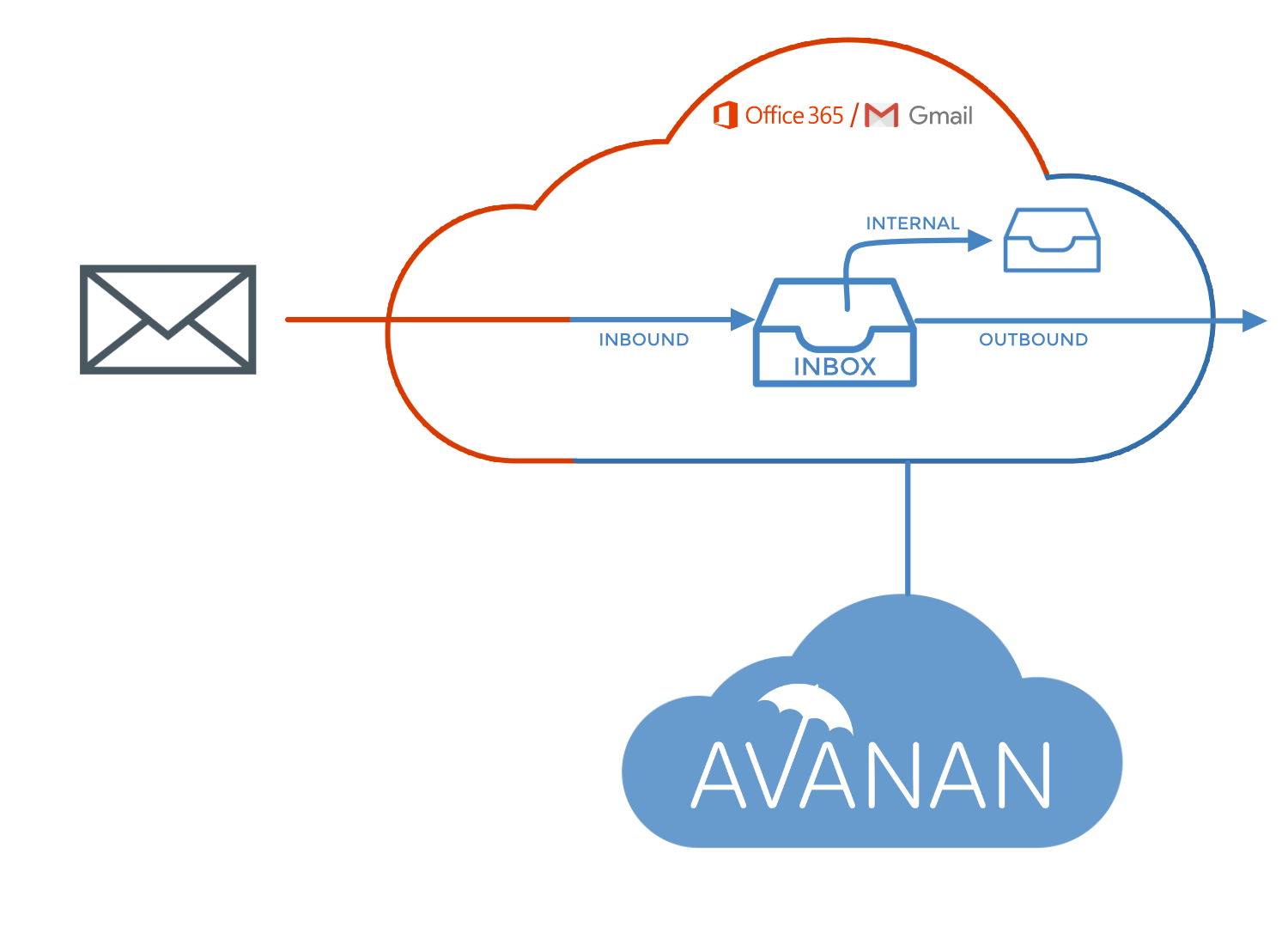
Because most hackers leverage vulnerabilities in Office 365 or Gmail to bypass default security, such as HTML obfuscation methods, Avanan uses these methods as indicators of phishing in our AI algorithm. To block similar attacks in the future, that list is continually added to—we now analyze over 300 (and growing) indicators of attack.
Some email providers, like Secure Email Gateways, only scan inbound emails, which means that their dataset for attacks is just related to the scope of all inbound emails. Avanan scans inbound, outbound and internal emails, meaning that its dataset is the entirety of all emails. Because internal attacks are an increasing point of entry, Avanan has a specialized AI model for scanning internal traffic, using indicators relevant to an internally-originated attack. As hackers use internal accounts to send malicious content to employees, customers and partners, Avanan is able to identify those emails as phishing and block them accordingly.
Additionally, by deploying inline via API, Avanan is able to scan a year’s worth of email conversations—within hours of first deployment—to build a reputation network. This helps reduce false positives and our AI learns from the relationships between employees and other communications to create a custom threat profile to block attacks specific to an organization.
Avanan is also the only security provider to monitor and protect the entire productivity suite within your organization. Avanan is able to leverage the same tools that secure email to protect file-sharing apps like Dropbox, Box, SharePoint and OneDrive, as well as communication apps like Slack and Microsoft Teams.
Why Avanan’s Solution Works
Avanan is the only company that sits behind email. That gives it a 30,000-foot view, in addition to a granular one, allowing it to see new threats develop and catch them. Avanan takes the entire world of known indicators of attacks that all email providers use, and supplements that with even more, real-time data, the only data of its kind.
Additionally, unlike SEGs, Avanan’s security doesn’t change MX records. There’s no way, then, for hackers to know that Avanan is the protection solution. Being invisible to hackers means that they can’t create specific attacks meant to bypass Avanan security.
Final Thoughts on Stopping Phishing with Avanan
One phishing attack can cost a mid-sized business as much as $1.6 million in losses. For large companies, it's even worse. After a company is breached, 1 in 4 consumers won’t continue to do business with them.
Standard email clients don’t provide the type of security that gives confidence that phishing scams will be eliminated. Anti-phishing software has to be all-encompassing and catch everything—not just some things.
That’s how the Avanan solution works, and companies large and small have used it to their advantage. It’s why Gartner has chosen it as the top-rated email security solution.
Get a demo and see how easy it is to eliminate phishing attacks against your organization.