Google's G Suite brings much-needed convenience and organization to the enterprise cloud. But, can a Google Drive account be hacked? Because of its popularity, it is a favorite target for hackers.
Every day, we catch new and innovative attacks perpetrated against our customers who use G Suite, but some of the strategies are common enough that everyone should be aware of them. In each of the attacks described below, the hackers leverage the trust and familiarity of the Google brand to fool people into doing something dangerous.
Hosting Zero-Day Malware on Google Drive
Although Google scans for known malware uploaded to Drive, it has no way to identify Zero-Day malware. This presents an easy way for hackers to spread a malicious file through a trusted platform. They can host malware with a public docs.google.com/ link that will be considered a trusted domain by every email filter. It is very unlikely that any organization will block the Google domain. More importantly, even savvy users, who check the domain before clicking on a link, would not hesitate to click on a google.com link. This was the method used by the Shurl0ckr Ransomware attacks discovered earlier this year.
Using Google Drive Files to Host Malicious Links
In a similar but more subversive strategy, hackers will hide a malicious URL within a Google document. Google would see the URL as benign text and do no filtering on the web link. Hackers use Google's trust of its own services to their advantage by putting malicious links into Google Drive files and hosting that file publicly. They then will send the link to the file in an email to their intended targets. Since the link in the email begins with docs.google.com/, it is trusted and the recipient will receive the seemingly harmless Google Doc containing the a malicious link in its body.
Using Google Redirects to Disguise Malicious Links
As we have established, Google places a lot of trust in its own links. If it sees a link going to google.com, it will often wave it right past its malicious link scan. Unfortunately, hackers have found a way to make links that begin with google.com but redirect to any URL they choose.
A simple redirect using a Google redirect to go to our homepage would be:
www.google.com/url?sa=D&q=https://www.avanan.com
For these redirects, Google does provide a warning to prevent those who click on the link from unwittingly being taken to a malicious site. The warning looks like this:
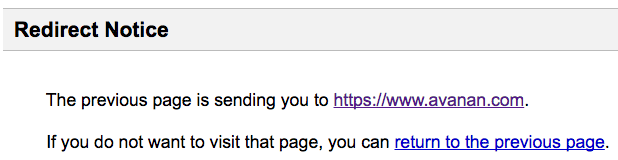
But by also redirecting through Google's app engine, the notice can be skipped. A link implementing this strategy to lead someone to our homepage would like this:
www.google.com/url?sa=D&qhttps:/appengine.google.com/_ah/logout%3Fcontinue%3Dhttps://www.avanan.com
The addition of the App Engine link in the middle tells Google that the redirect is trusted without giving the user a chance to even view it. We discuss this type of attack in greater detail here.
Conclusion
Protecting your email from attacks is important, but still only part of the equation. When you are on the cloud, attacks can come from anywhere. Implementing full cloud security that scans links in emails as well as in folders and documents is vital if you want your cloud environment to be truly fortified from attacks. This is where Avanan comes in. We use advanced AI to protect your inbox and catch what others miss. Learn about our G Suite Security software to keep your Google accounts safe from hackers. Try Avanan free for 14 days or request a demo.





