Hackers want your credentials. It’s why the Verizon DBIR found that the top threat varieties in breaches were phishing and the use of stolen creds. Phish users to get their credentials; use them to infiltrate bank accounts and more.
What better way to phish a user than make it look like it’s not phishing? If you can convince a user that the email is legit, they’ll be more likely to click. Better yet—make it look like it’s coming from someone they know and trust. Of course they’ll click! Though phishing click rates vary by industry, the general average is around 27%. That’s a lot of potential users to phish.
What is Email Spoofing?
That's one of the reasons why email spoofing is so popular. More than 90% of email attacks have some form of spoofing or impersonation to them. The easier you can make it for someone to click, the better the chance that they will.
It’s become even easier in the age of Software-as-a-Service (SaaS). A SaaS app is often a trusted communication channel for a user and users have trained to frequently re-authenticate and will often receive messages requiring a login—so an ask to login is not out of the ordinary.
How Does Email Spoofing Work?
To create a spoofed message, email spoofers fabricate the email header to make it seem like it’s coming from someone they trust. It can look something like this:
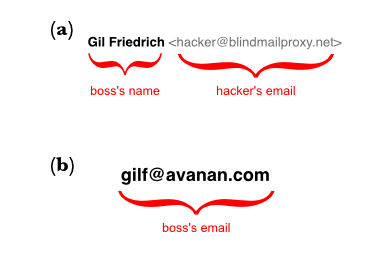
This is what one attack used back in 2017; using the nickname feature in Gmail to obfuscate the actual email used by the hacker. There are scores of ways to do that. The idea is to make it look like it’s coming from a real person, a person that you normally email with. This is often how business email compromise attacks work. Hackers often hope the recipient will first check it on their phone, where users will most likely not inspect the email name.
Further, this is more of a long-term game; a rapport will be developed before the ask is made. Spoofed emails can be incredibly difficult to detect. This attack works because it tends to be casual and personable, no different than any other email a user would receive. But it has real effects. The hacker can gain access to an account, requesting credentials or protected information from an organization, or use it to infiltrate other accounts.
Different Types of Email Spoofing
One of the challenging things about email spoofing is that it doesn’t come in one form. As long as one part of the email is spoofed, it has a chance to work. Hackers will exploit a number of different factors when trying to spoof a message and steal credentials or other information.
Brand Name Spoofing
We’re all the recipients of an onslaught of branded emails—promotions from our favorite stores, notices from our banks, shipping notifications. Because of this, hackers attempt to do what they can to exploit it. According to Avanan’s 2019 Global Phish Report, 1 in 25 branded emails is actually a phishing attack.
Brand name spoofing is playing on that, hoping that the individual is familiar enough with the brand to take it at face value. Let’s say you get an email from your bank. There’s some inherent level of trust in that email, because you’ve often gotten emails from your bank. Because it looks close enough to the real thing, it may be enough to get the user to click.
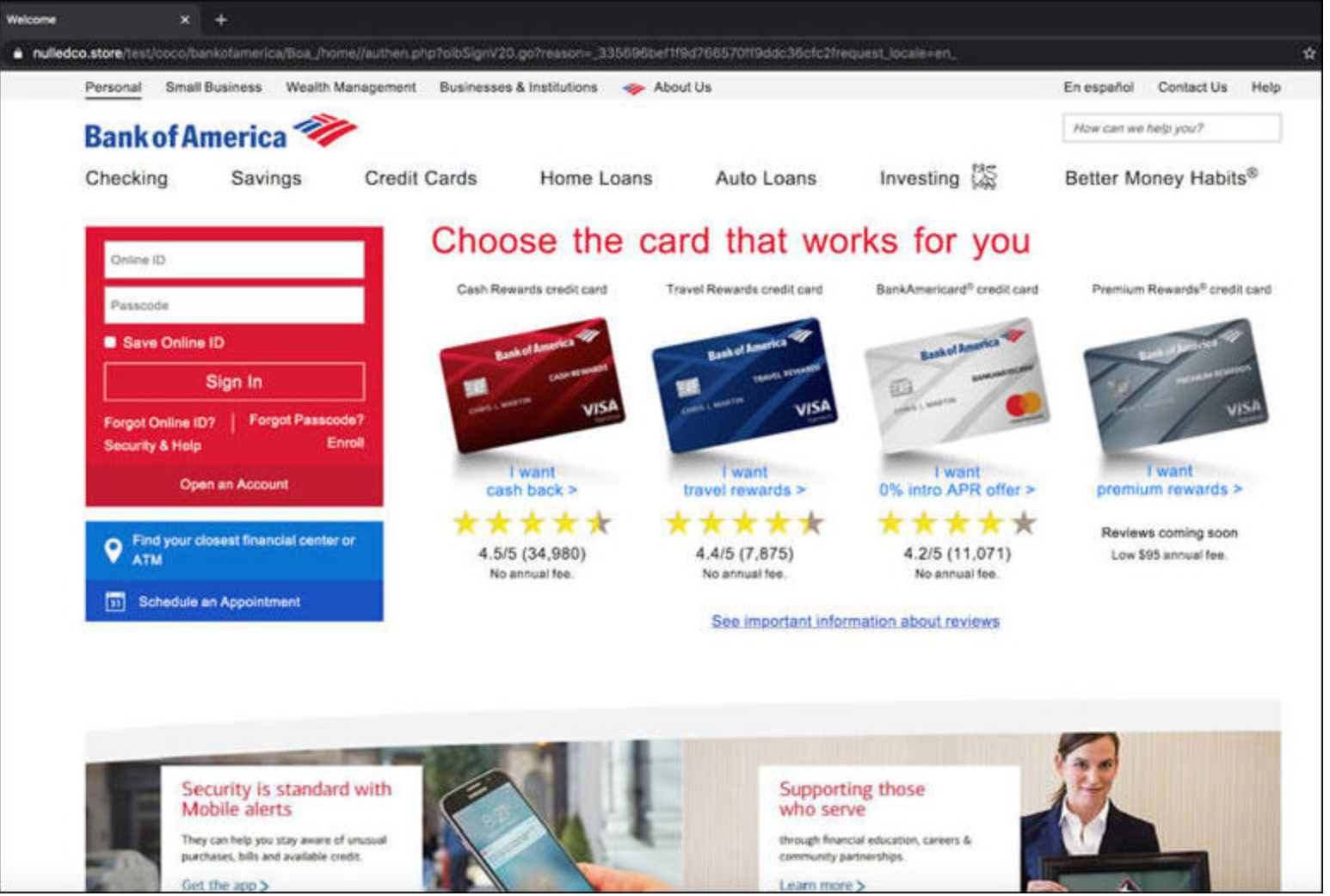
We’ve seen this attack play out recently, particularly in the financial sector. Bank of America’s website was used in a brand impersonation. The hackers sent an email asking for an email change request, and took the user to a page with Bank of America’s logo. If successful, the hacker gets the login information, and because it asked for security questions, the hacker gets those too.
That page looks pretty convincing—but it's not legit. It's a front for a credential harvesting page.
These sorts of things are common. In these sorts of attacks, the email contains an ask, but it's an ask that’s been heard before—email verification, password change, etc. It’s urgent and demands action, usually in the form of clicking a malicious link. That link can often look just like the real thing.
Perhaps because these have been so successful, Google is trialing a feature with authenticated logos next to brand names. The idea is to mimic the blue checkmark on Twitter—a way to know that the email is coming from where you think it’s coming from.
Domain Name Spoofing
Another way to spoof is by mimicking a domain name. Many users will not inspect a URL; even if they do, hackers can leverage actual URLs to host phishing attacks. That’s what happened in the PhishPoint attack, which relied on domain impersonation to harvest credentials and ended up targeting 10% of the Office365 user base. The hackers hosted the malicious content on an actual SharePoint file, and since the URL is acceptable to Microsoft, it easily passed scanners.
By mimicking an actual Microsoft login page, the hacker is able to steal your credentials easily. The below is a fake page—but it looks real:
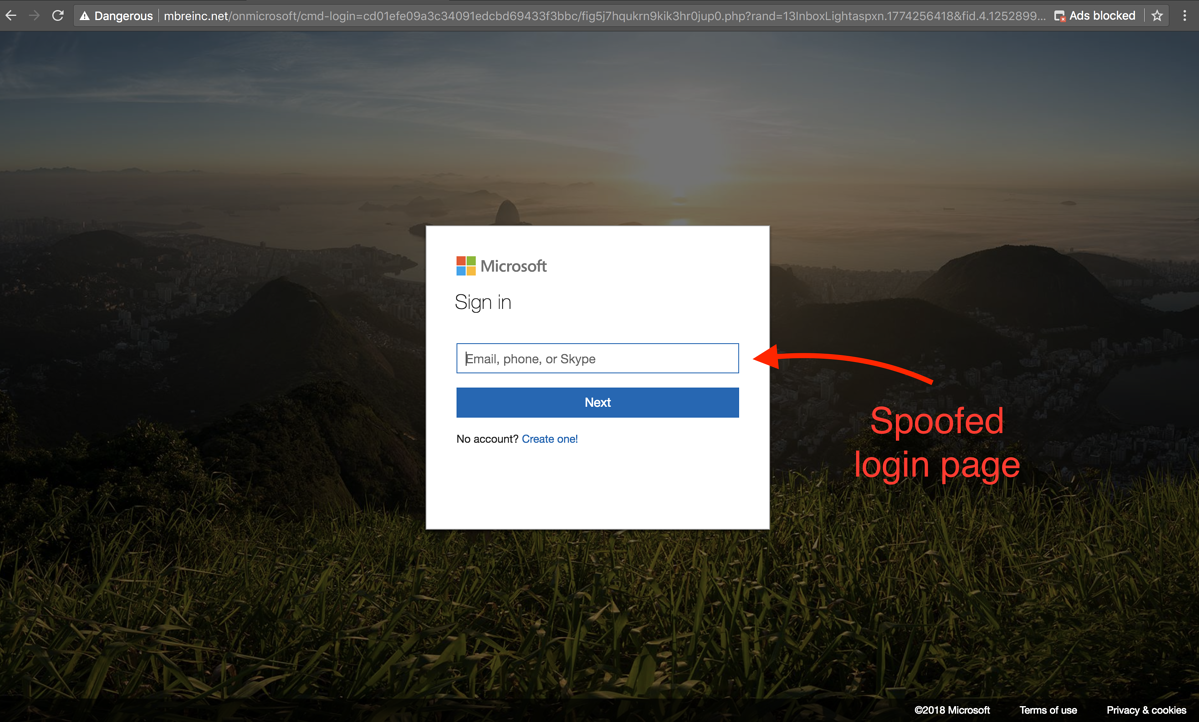
Beyond these, hackers can make URLs look just like the original, but with one minor change, perhaps a different character. Sometimes, a hacker will insert characters from a different language or use Unicode when there is a nearly-identical swap available. To the naked eye, these can be practically indistinguishable.
How You Can Prevent Email Spoofing
Preventing email spoofing is doable, and it starts with powerful anti-phishing technology.
That’s what Avanan provides and it starts by leveraging its API integration and AI to help. Because of its complete AI integration, Avanan knows your employees by name—even nickname–and role, so that it can identify when messages are attempting to impersonate someone real.
Avanan also uses the hundreds of thousands of data points it collects to undergo impersonation analysis, scanning the sender and message content for impersonation. The algorithm looking for user impersonation, and whether a single sender exists in the organization with a different address. Avanan can do that by cross-referencing several fields, such as sender and signature.
To protect against domain impersonation attacks, Avanan will check if the sender is sending from a domain that’s similar to a known domain, but with a different mail-flow path. That’s similar to the analysis we do for brand impersonation, where we detect if the mail-flow path doesn’t fit the sender. That’s buffeted by the scanning of files and email (inbound, outbound, and internal) to look for URLs—even if recursively embedded—and by actively following redirected links to measure domain risk and perform individual page analysis.
Because hackers are so good at spoofing login pages to look like the real thing, Avanan uses dynamic analysis tools that simulate the action of the file or link in a sandbox environment. That means we can follow a URL and compare the rendered image to known login pages.
Further, Avanan consistently improves its AI algorithm, by presenting a message to the end user asking if they trust the particular sender. This helps the algorithm learn what’s legitimate or malicious based on user activity.
This is all on top of Avanan’s standard scanning of 300 (and growing) indicators of attack that are checked before every email. In addition, because Avanan protects the entire collaboration suite, so any east-west attempts are picked up on.
Final Thoughts on Email Spoofing
Hackers are betting that end-users will be distracted enough to click on links that look close enough to the real thing.
Often, that is the case. But anti-phishing technology that leverages AI to know when something is impersonated is an essential tool in your arsenal to stay protected.
Try Avanan and see how these unique features can apply to your environment and protect you from email spoofing.