The Twitter attack that saw a number of major accounts—like Joe Biden, Barack Obama, Elon Musk and other celebrities—overtaken and hacked was done via a spear phishing campaign.
Though Twitter hasn't released full details, they have shared the broad outlines of the attack. Hackers were able to dupe a number of Twitter employees to give over their access credentials. Through those credentials, the attackers were able to access internal systems and breach account tools. They were then able to send tweets from the affected accounts and receive bitcoin transfers totaling over $115,000 before it was shut down.
Twitter called the attack a "phone spear phish" though it's unclear exactly how the hackers used a phone to get inside. (Twitter's CEO Jack Dorsey had been the victim of a "SIM swap" attack in 2019, but it's not known if that was repeated in this most recent iteration.) Regardless, as Twitter noted, "This attack relied on a significant and concerted attempt to mislead certain employees and exploit human vulnerabilities to gain access to our internal systems."
However the hackers got inside, the spear phish exploited what is quickly becoming one of the most popular form of breaches—stolen credentials. The Verizon Data Breach Report found that credential stealing is the top data compromised in phishing breaches. Further, Cofense has found that 74% of all phishing attacks are credential scams.
Twitter has said that they are updating their processes and are "taking a hard look" at how they can make them better.
However the breach occurs, and whether an internal employee is acting maliciously or their accounts are taken over, insider threats are a real problem. A Wall Street Journal poll found that 70% of companies worry about malicious employees; Verizon found that 30% of all attacks are perpetrated by internal actors.
By 2023, 65% of organizations are projected to inspect their internal email traffic for phishing and malware—but as of 2019, that number is at just 7%.
A large reason for that is Secure Email Gateways (SEGs) like Proofpoint and Mimecast cannot, by nature of their architecture, see or analyze internal messages between cloud users:
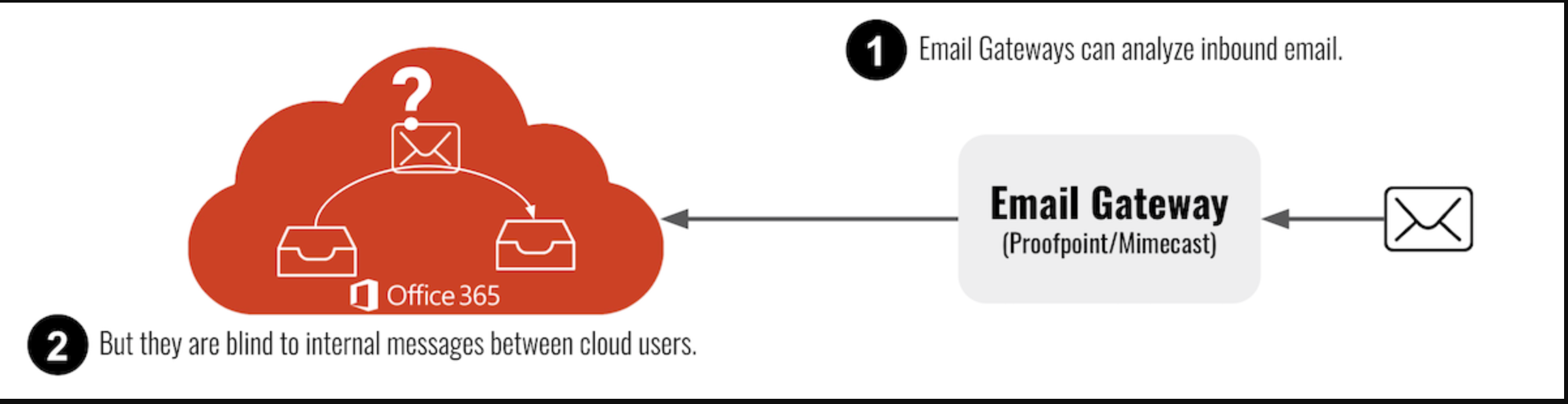
Because Avanan installs as an app via API, it can scan all email, whether it's inbound, outbound or internal. Additionally, Avanan has a specialized AI model for scanning internal traffic, with indicators relevant for internally-originated attacks.
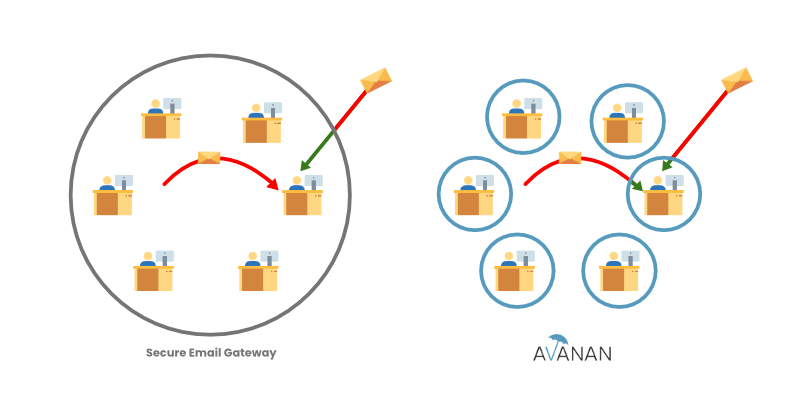
Regardless of platform, securing internal email and applying a zero-trust approach is crucial. Your internal employees may not have access to a former President's account—but it doesn't mean an internal attack won't hurt.