This week we saw a phishing attack at one of our customers that is using Proofpoint before their Office 365 email—a pretty basic phishing attack that bypassed both Proofpoint and Microsoft. But without Proofpoint, Microsoft is actually detecting it. This begs the question, is Microsoft actually safer without Proofpoint? How could it be? This is the subject of this blog.
Why have we looked for such attacks? We received a tremendous amount of feedback on last week's blog 8 Security Considerations When Moving to Office 365—especially questions about email attacks that are only reaching users who deploy MTA-based email security gateways like Proofpoint and Mimecast. These attacks are not targeting these customers in particular, but are only reaching the inboxes of customers who deploy an MTA-based email security before Office 365 and Gmail. It happens because the MTA-based solutions actually disable Microsoft’s and Gmail’s default anti-spam and anti-phishing security.
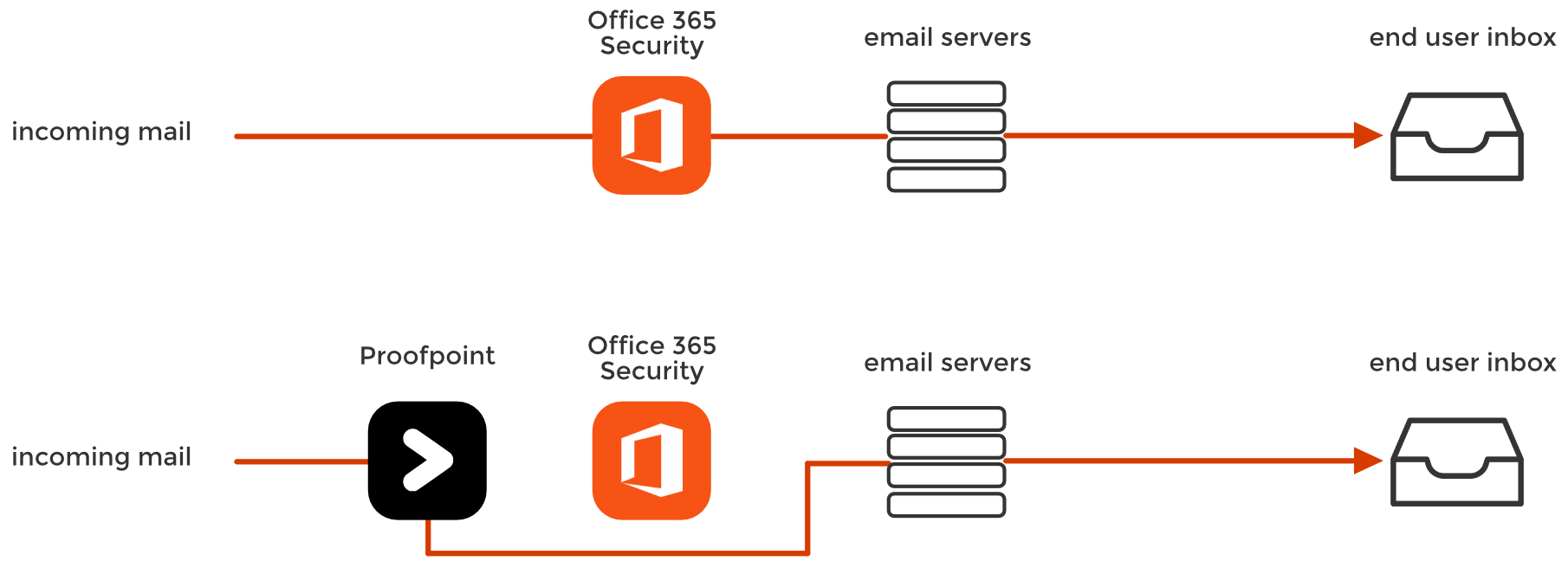
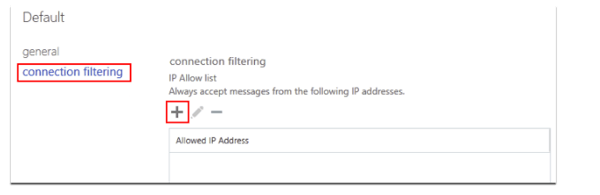
The basis of this comes from the fact that when deploying an external, MTA-based solution, you must bypass EOP anti spam features as discussed below.
See: Add Proofpoint Essentials IP Ranges to the Connection Filter Policy
See: Add Mimecast to the Allowed List in Office 365's Connection Filtering Policy
This design would be fine if the MTA gateway is able to block 100% of incoming phishing attacks. In fact, even though there is a lot of overlap in protection (most malware caught by Proofpoint and Mimecast would have been blocked by Microsoft, anyway), we've found there are quite a few attacks that Microsoft can detect and that the MTA-based solutions from Proofpoint and Mimecast don't.
A Recent Attack
The Avanan platform uses API to add security after Microsoft's and Gmail's default filters, but before the user's inbox. This "virtual inline" approach gives us a unique vantage point to identify threats that bypass Microsoft and Gmail security. We add security instead of replacing it.
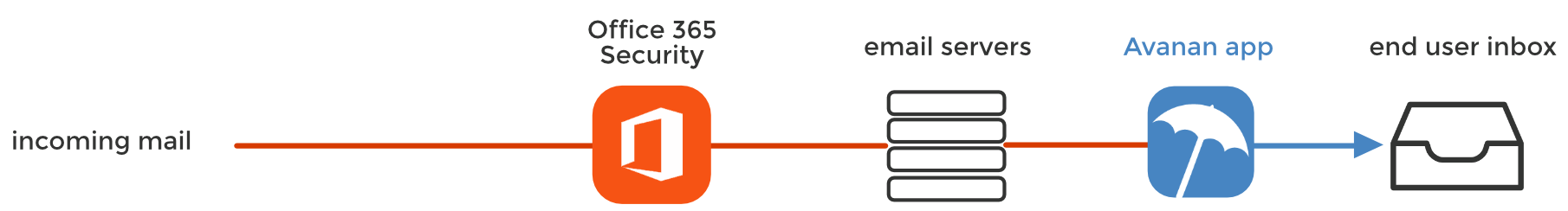
Because some of our customers continue to use their external MTA gateway even after deploying our platform, we are also able to see attacks that bypass Proofpoint and Mimecast
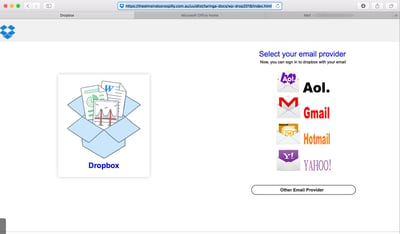
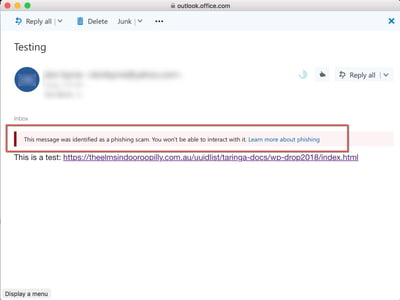
For example, here is a recent attack missed by Proofpoint but blocked by Microsoft. Because a Proofpoint installation requires customers to disable Microsoft's filters, an attack would bypass both and end up in the user's inbox.
|
Phishing Link Passed by Proofpoint
|
Email with Same Link Detected by O365
|
Most Office 365 customers were protected from the attack by Microsoft's warning embedded in the email. (Avanan's filters deemed the URL malicious enough to block the message entirely.) Only Office 365 customers with Proofpoint received the email with the malicious URL, and without Microsoft's warning.
In short, if you are currently using an external mail security gateway, you are not getting the best of Microsoft security. Click to learn more about Avanan vs. Proofpoint and the important differences in email security.
For more information on this topic, you can read some of our earlier blogs, including our discussion when we first discovered this phenomenon:
Why Proofpoint and Mimecast Can't Secure Office 365 and Gmail