Highlights:
- Attackers have expanded the battleground from the inbox to the web
- This is the hacker’s response to click-time protection and the technique is able to bypass Microsoft’s Safe Links feature
- Hackers are applying similar tools they used to fool email filters to obfuscate credential-harvesting websites
- If you use Microsoft EOP or ATP, you are vulnerable.
The New Front in the Cybersecurity War
The battleground has expanded from the inbox to the web.
In the cybersecurity arms race, the battleground has always been the email inbox. Hackers use countless techniques to obfuscate email messages—hiding their malicious content in order to bypass Office 365's security filters.
ATP Safe Links create a layer of protection after the inbox, around the URL, and hackers have responded with new obfuscation methods after the click. The new cybersecurity front is being fought on the phishing websites.
This is the hacker’s way of hiding a malicious website from Microsoft’s click-time protection.
SiteCloak Methods Obfuscate Credential Harvesting Sites
Microsoft’s click-time protection service (better known as Safe Links) was introduced to detect malicious links. Originally, it had been a value-negative, because it obscured the original URL with a rewritten link and thus worked against decades of user-education about visual cues and phishing. In 2018, we recommended using Safe Links only as a way to conduct post-mortem analysis, not as a tool against phishing, especially after it was used in Open-Redirect Vulnerability in 2017.
In 2019, Microsoft added Native Link Rendering, which allowed users to inspect the original link and make an informed decision about clicking it. That helped in the battle against phishing.
For attackers, Safe Links meant that they had to find a new way to bypass this layer of defense.
SiteCloak is how hackers are responding, a way to bypass the time-of-click scanning by “cloaking” the malicious website. It does this by showing a benign page to Microsoft, but a realistic-looking credential harvesting page to the victim.
SiteCloak Methods in Action: How it Works
In the simplest version of the attack, the credential harvesting page uses the same ZeroFont technique that was once a popular method to bypass Microsoft’s email scanners. Even old techniques can successfully fool the website scanner.
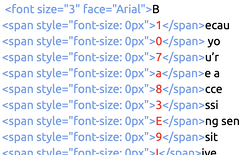
This method of attack is incredibly easy to implement, whereby the attacker embeds random characters of font-size zero between characters in the page. Natural-language filters see the random text while human readers see what the attackers want them to see.
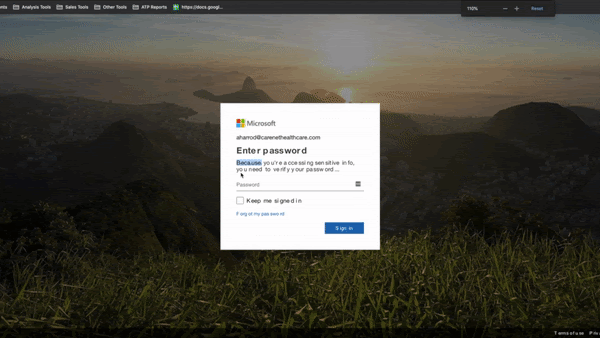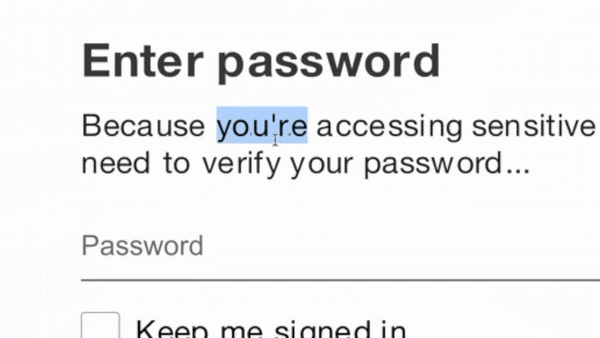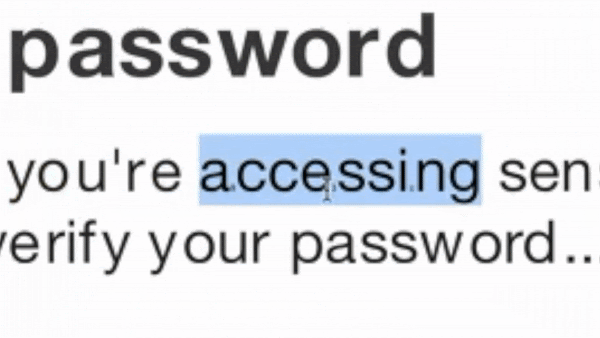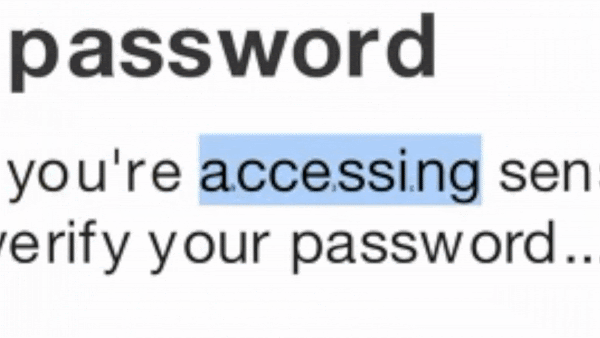
In more advanced methods, the webpage is encoded using multiple layers of java script obfuscation.
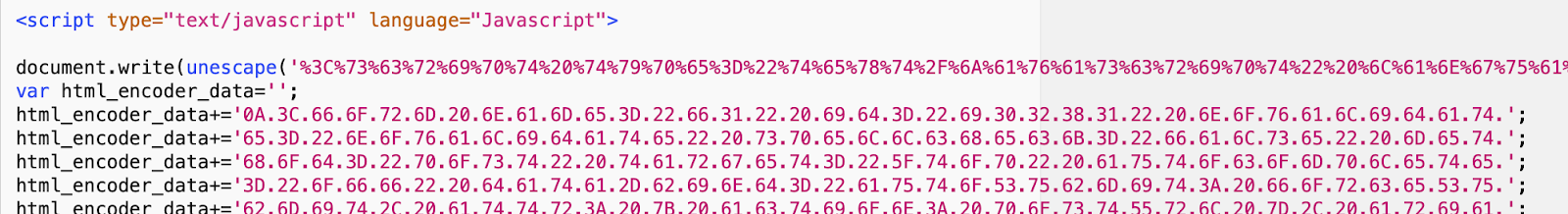
In this example, the ‘unescaped’ command is actually another javascript function that reads the ‘html_encoder_data’ to render the malicious web page within the user’s browser. While site-scanning tools cannot decipher the intent of the page, the users see a very high-quality rendering of a Microsoft login.
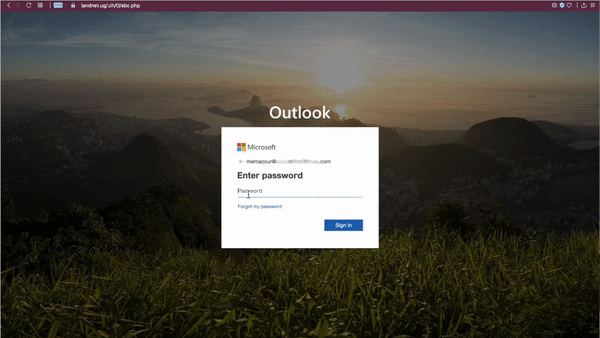
Because Microsoft filters are unable to fully render the full javascript, they see the ‘java-free’ version, a more benign form that would not trigger Safe Links to mark the site as malicious.
These are just two examples that cover the range of techniques–from simple HTML hacks to advanced Javascript encoding. Because the tools used to identify malicious websites have not yet caught up with the filters that identify malicious email, many of these techniques are long-outdated methods that have found new life in SiteCloak obfuscation.
How Avanan Catches These Attacks
It is these sorts of attacks that illustrate why an additional, non-Microsoft layer of security is needed to protect the inbox, because hackers test the attack with the default security and design it to bypass that layer.
One of Avanan's detection layers uses the hacker's own obfuscation techniques as a way to identify the attack. Because the web-scanning algorithm looks for known obfuscation methods as Indicators of Attack (IoAs), these sites self-incriminate themselves by their usage of a hacking method.
Avanan analyzes links both when the email is delivered and at click-time. This is important because some attackers enable the malicious content only after the email message has reached the inbox.
The Future of Hacking: Hackers Learn to Abuse New Protection
The battleground has evolved. From email to the web to any number of cloud-based applications, any online citizen is at risk. Microsoft’s success has made it a target so each day brings new and maliciously innovative ways to bypass its security. It’s imperative that companies and end-users have a security solution that responds to these new threats in real-time.
SiteCloak is the latest way of hacker’s responding to new ways of protection and attempting to outwit it. We know it won’t be the last.