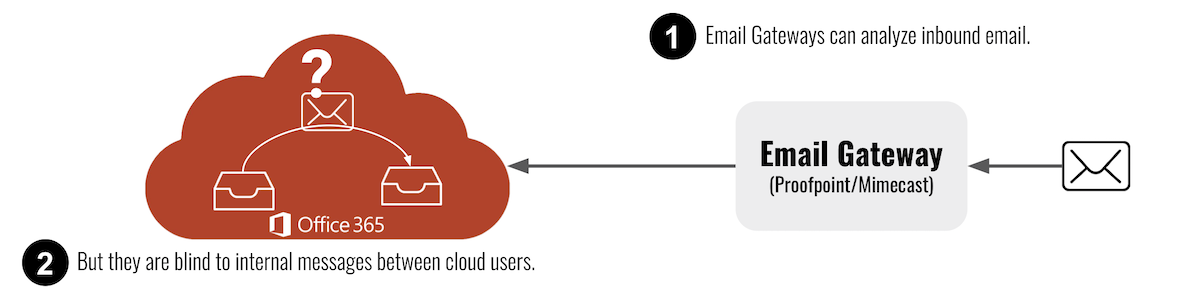
Proofpoint and Mimecast are traditional email security gateways that redirect traffic through a cloud-based proxy before it reaches the email server. This works well if you assume all threats are external, but they can be blind to internal attacks and compromised accounts.
Gateways Secure the Perimeter
Proofpoint and Mimecast are some of the most popular email security products on the market, yet they a fundamental problem with the architecture of their solutions. Because they deploy as a gateway outside your email's cloud, they miss email messages between your employees that never leave your mail provider.

Gateways Use a Work-Around to Scan Internal Email
By default, Mimecast and Proofpoint do not analyze internal email. Because of that, they introduced a workaround product to solve this problem. Unfortunately, it doesn’t provide real-time, pre-inbox security that is necessary to protect against insider threats.
Proofpoint and Mimecast use SMTP journaling to inspect messages after they hit the inbox. (Mimecast also offers POP3 to query up to 100 emails every few minutes.) These gateways periodically pull a set number of emails from your organization’s message flow at intervals for review.
The obvious issue is that the emails must arrive in the user’s inbox before Journaling can take effect. This means that gateways quarantine and remediate threats only after they’ve arrived in the inbox, which is all that is possible for tools that deploy outside your email provider’s cloud.
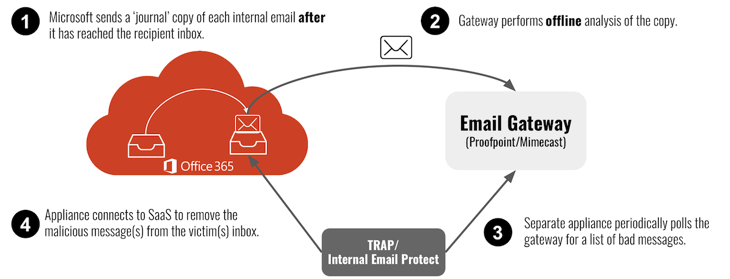
How Proofpoint TRAP and Mimecast Internal Email Protect Work
-
The gateway monitors all this journaled email just like it does for all incoming email. But because they are filtering a copy of what’s already in the inbox, it’s too late to block the email.
-
TRAP and Internal Email Protect poll the gateway for bad messages.
-
If there is a bad email, they log into the victim’s inbox to remove the malicious content, potentially minutes after the user’s clicked the message.
While Proofpoint does this process through the TRAP mechanism, Mimecast protects internal email after three separate policy configurations for content examination, URL protection, and attachment protection.
Gateways Can't Stop Threats in Real-Time
Proofpoint and Mimecast effectively filter inbound and outbound email. But no amount of work can be done to overcome the problems created by their deployment architecture. Their internal message filtering more closely resembles archiving than true internal scanning, which remediates malicious emails and phishing attacks before they hit the inbox.
Journaling internal email for security scans is fundamentally risky, because it analyzes threats at a delay. Only Proofpoint, Mimecast, and their customers can comment on the length of time between a malicious email arriving in a user’s inbox and them clicking it. But knowing the behavior of the average user, who clicks an email within a minute and 20 seconds of it arriving in their inbox, any interval is too long.