Over the course of your working lifetime, how many Excel spreadsheets have you been sent?
Thousands, if we're being conservative. So, of course, hackers will leverage that to try to get your information and credentials.
The Attack: Avanan researchers discovered a new phishing email that looks like this:
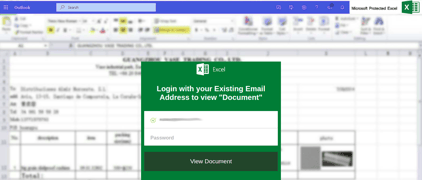
The attackers used HTML to create a fake, but convincing, login page. There's a blurred out file in the box and a login box up front, meant solely to steal the user's password.
Though Avanan stopped this attack, it passed by Proofpoint's scanners.
How?
Simple obfuscation. The attackers put separators between the HTML elements, making it harder for Proofpoint's scanners to identify what was going on.
Why it Matters: Avanan has detailed some of the many ways that hackers use obfuscation techniques to get past email scanners. From ZeroFont to MetaMoprh, SiteCloak to TattleToken and Go HSIPH, hackers are employing a variety of tools to fool scanners and get into your inbox.
What's different about this attack is that it bypasses Proofpoint. So far, we've been tracking obfuscation of Microsoft SafeLinks. And we've seen a number of different methods that have accomplished this.
But this attack is one of a number we're tracking that bypass Secure Email Gateways, including the Not-a-Pay-Pal attack.
Hackers aren't just content to bypass one thing—while they're showing sophisticated in getting through SafeLinks and ATP, the same can also be said for their work in getting past Proofpoint and other SEGs.
Avanan caught this because one of our detection layers uses the hacker's own obfuscation techniques as a way to identify the attack.







