We are seeing a rise in the number of phishing attacks that bypass Office 365 due to the attackers’ use of obfuscation techniques on the credential harvesting website.
These SiteCloak methods bypass Microsoft’s real-time URL-filtering scanners by obfuscating the credential-harvesting page. This behavior is widespread, using a variety of techniques from multiple threat actors.
Quick Summary of Obfuscation Attack Target
Platform: Microsoft 365 Email
Email Security: Exchange Online Protection and Advanced Threat Protection
Targets: All organizations. All sizes.
Payload: Malicious Link
Technique: Obfuscation of Credential Harvesting Page
What is a SiteCloak Attack?
- Background: In order to identify a malicious URL within an email, Microsoft will follow a link to scan the target page for potential malware or phishing behavior.
- Email Attack: Attackers are hiding the intent of the target page using a variety of obfuscation techniques. This behavior is widespread, using a variety of methods of varying levels of sophistication from multiple threat actors. Most are capable of fooling Microsoft's scanners.
- Payload: In most cases, the target page is a credential harvesting site, but because these techniques are now in widespread use by a number of organizations, they are independent of the purpose of the page.
- Result: If the user is not vigilant and provides their credentials, the user account is compromised.
Why are SiteCloak Obfuscation Techniques Effective?
- Concealed Page Intent: Microsoft URL filters are unable to determine the intent of an obfuscated page, so a malicious email is allowed to reach the user inbox.
- Multiple Vulnerabilities: While categorized as a single method, attackers are using a variety of obfuscation techniques, so that there is no single vulnerability to close. Even simple techniques are successful today, but as these are eventually caught, more advanced methods will continue to remain effective.
- Multiple Actors: Page obfuscation is now in use by multiple actors. The techniques are typical of email obfuscation–many of them old–so there is no direct link between a threat actor and their methodology.
How Can You Prevent Obfuscation Attacks?
- Use a Password Manager: The best defense against most credential harvesting attacks is the use of a password manager. Most are free and none can be fooled into entering a password into a malicious site, no matter how seemingly authentic. You should never actually know your own password.
- Enable Multi-factor Authentication: MFA renders a username/password pair useless to an attacker.
Examples of The Attack:
These techniques are in use by a large number of threat organizations, so their methods vary widely.
Basic SiteCloak Obfuscation: ZeroFont
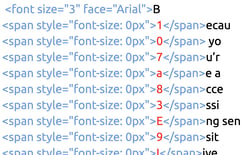
In the simplest version of an obfuscation attack, the credential harvesting page uses the same ZeroFont technique that was once a popular method to bypass Microsoft’s email scanners. Even old techniques can successfully fool the website scanner.
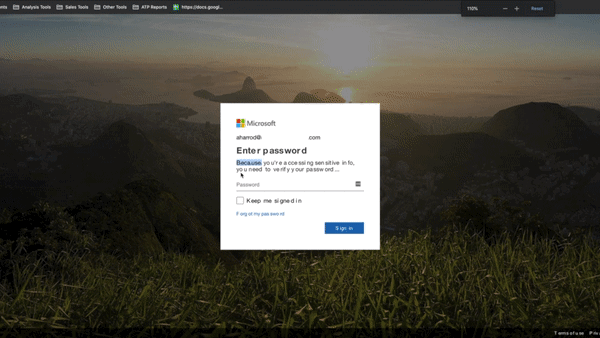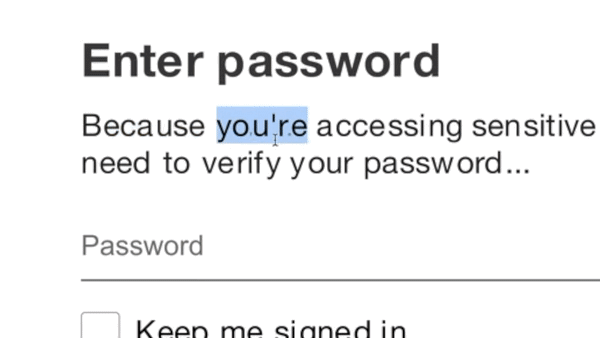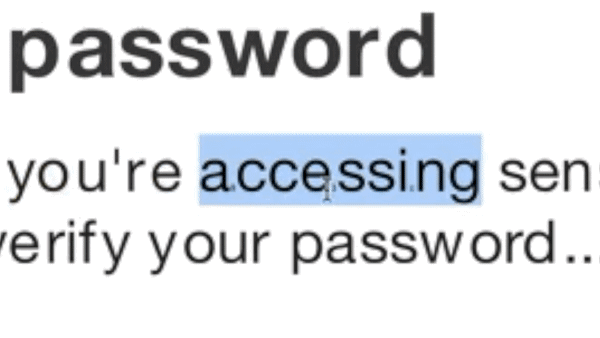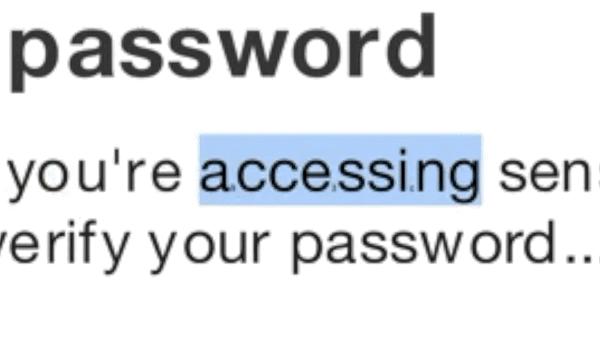
Advanced SiteCloak Obfuscation: Java Script Encoding
In more advanced methods, the webpage is encoded using multiple layers of java script obfuscation.
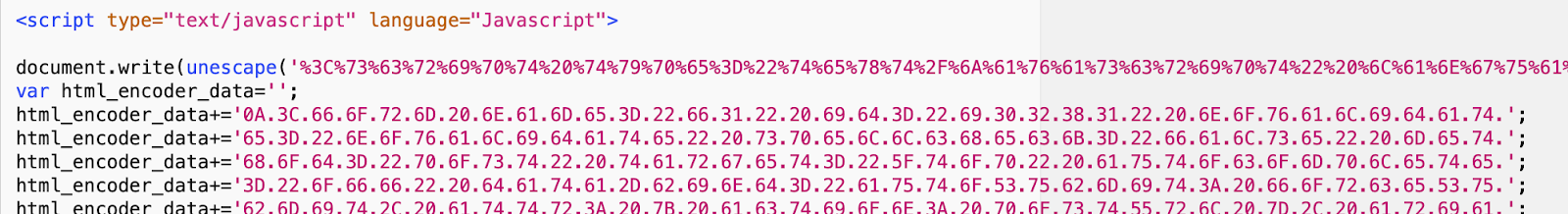
The ‘unescaped’ command is actually another javascript function that reads the ‘html_encoder_data’ to render the malicious web page.
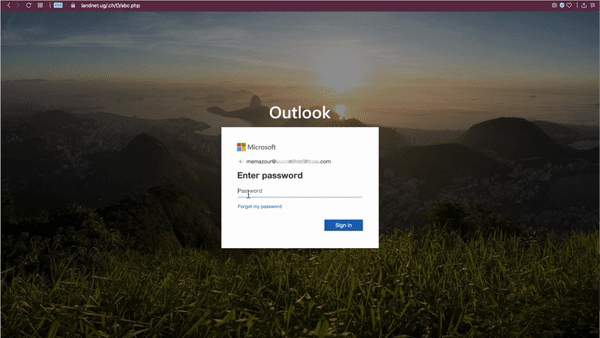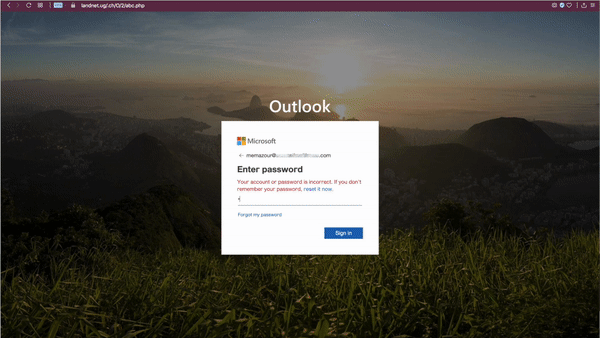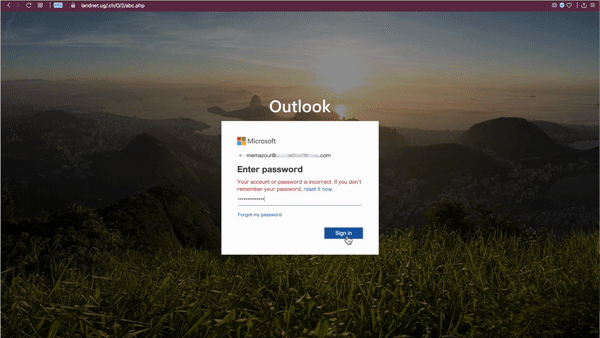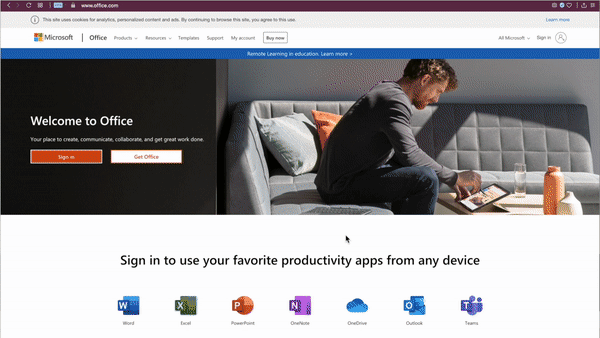
The rendered page is fairly advanced in that it does not ask the user to enter their email address (it is encoded in the URL) and asks for the password twice before redirecting the user to a real outlook.com page. Not only does this error-check the password for the attackers, but the user is also left with no hint that they entered their password on a fake site.
The Avanan Advantage
Avanan is able to identify SiteCloak obfuscated websites because the web-rendering and scanning engines utilize the same indicators of attack discovered by the email-rendering and scanning filters.
We stop these obfuscation attacks from reaching your inbox in the first place.






