Money transfers have always been popular online, even more so as cash has become less relevant.
The most popular peer-to-peer payment service is PayPal. And, of course, hackers are leveraging that information to try and steal your credentials and get into the platform to potentially take your money.
The Attack: Avanan researchers discovered a new phishing email that looks like this:
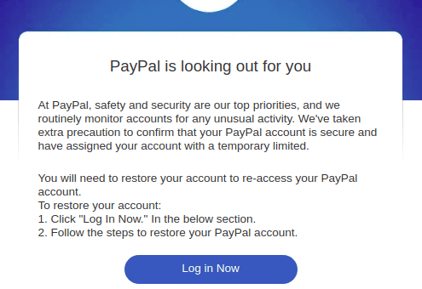
Looks pretty convincing, right? (Take a close read, though, and you'll notice a few grammatical errors. In the second sentence, "precaution" should be "precautions." In the first numerated point, it should be one sentence, not two.) If you were to click on "Log In Now" you'd be directed to this page:
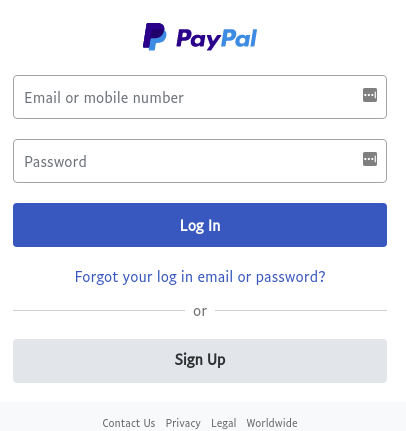
This is looks pretty close to the real deal. But it's not.
Though Avanan stopped this attack, it passed by Proofpoint's scanners.
How?
Take a look at the source code.
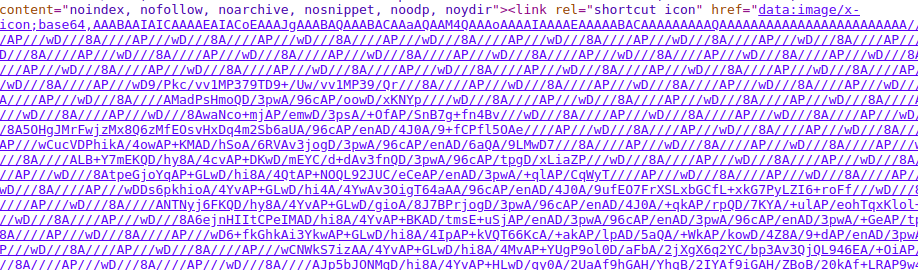
The hackers used obfuscation techniques that hides the PayPal logo.
Why it Matters: Avanan has detailed some of the many ways that hackers use obfuscation techniques to get past email scanners. From ZeroFont to MetaMoprh, SiteCloak to TattleToken, hackers are employing a variety of tools to fool scanners and get into your inbox.
This is yet another way, using "type=hidden" and unknown characters. Until adjustments are made, these types of attacks will continue to flummox many email scanners.
Avanan caught this because one of our detection layers uses the hacker's own obfuscation techniques as a way to identify the attack. Because the web-scanning algorithm looks for known obfuscation methods as Indicators of Attack (IoAs), these sites self-incriminate themselves by their usage of a hacking method.







