This targeted phishing attack against Office 365 Outlook customers impersonates Excel Online in an HTML attachment in order to trick users into entering their credentials. Avanan security analysts confirmed that this attack bypasses both Gmail and Office 365 email security.
What it looks like
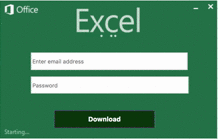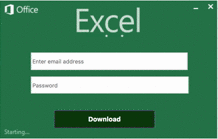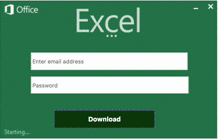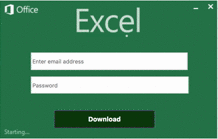
The email attack mentions a Purchase Order and includes additional details in an HTML attachment. The HTML loads in a browser and features:
- Base64-encoded images to mimic Excel Online loading.
- A form asking for credentials required to open the confidential document.
- An active login image, to add realism.
What makes this attack interesting
Every phishing attack attempts to fool the user into compromising important information, in this case, their Office 365 credentials. In the same way that credit card companies add holograms and banks add microprinting to their checks, many SaaS providers have added motion graphics to their logins to make them harder to copy.
As you can see in the image, the attackers have done a good job of simulating the real Office 365 login box that a user would typically have to enter in order to open a shared document.
Watch the recorded webinar "Understanding Cloud Security in 30 Minutes"
How it works
Entering credentials in the form leads to a POST request going to a PHP server belonging to Avguro Technologies in Russia:

The data entered is validated with simple Javascript to check if the email entered has one of the following extensions: com, net, org, edu, int, mil, gov, arpa, biz, aero, name, coop, info, pro, museum, and ws.
Why Microsoft and Gmail missed the attack
Microsoft and Google utilize a macro-strategy of malware analysis which looks across all users on all accounts as a way to identify widespread attacks. They do a very good job of catching major attacks that affect their userbase en masse. For this reason you do not want to employ a security tool that bypasses Microsoft or Gmail's default defense like an email proxy or MTA.
What they miss, however, are the more targeted attacks that may only be sent to a handful of organizations or even to a single company. They also commonly miss attacks that use multiple variants or possess a complexity that makes them take a long time to sandbox. This is where your third party security tools come into play.
Utilizing multiple security tools simultaneously is the only way to ensure that complex and targeted attacks will be identified before reaching your users.
The Avanan response
Security is hard. No single layer of protection is good enough. Even the best isn’t perfect. At Avanan, we actively seek out new technologies that use fundamentally different security techniques so no matter the attack strategy, there will be at least one solution within our platform that detects and blocks it.
Now what if an attack gets by all of our partners? What if an attack is clever enough to fool the industry's most advanced antivirus engines, best-in-class sandboxing and the latest next-gen machine-learning malware and anti-phishing technologies? Or what if the user's password was lost in one of the many password data breaches?
One of the benefits of being integrated within the SaaS environment is that we analyze every user event—in real time and going back in time for months or years—continually monitoring for suspect behavior and compromized accounts.
Behavior analysis is the phisher's Achilles' heel
In the same way that your desktop malware tools look for suspicious function calls, network connections or memory writes, Avanan monitors every SaaS event to identify a compromised account. Because users might use the same password across multiple services, or lose their credentials in breached database, we assume that we won't see the actual compromise event. This might be the very first and the very last line of defense.
We look for anomalous behavior, based upon a profile that we've built from each user's event history. Should a user lose their credentials, we can identify the compromized account and respond immediately.
Over time, we have identified the most typical behaviors of an attacker after they have gained access. While phishing attacks become more sophisticated, the post-attack use of the compromised credentials have not. We have used this knowledge to go back in time to identify breaches that might have taken place months or even years before we were deployed. More importantly, we can trigger a response immediately and undo malicious behavior before it has a chance to spread.






