Back when email was on-premises, your email server sat somewhere in a data center, protected by your security stack that was designed specifically for on-premises email. The security stack was super customizable, and best of all, no one outside your organization knew what security you’d deployed.
By 2021, 70% of companies will use cloud email services, while the other 30% will keep email on-premise. In the cloud, email security is different.
It doesn't integrate with Office 365's built-in gateway
When you’re on-premises, you have to secure everything yourself. When you move to cloud email, you don’t have to. Cloud email comes with its own security stack. Exchange Online Protection (EOP) security provides anti-phishing and anti-malware to anyone with an Office 365 subscription. This is essentially a free gateway that Microsoft built into Office 365 email.
Gartner says that “Microsoft has improved native Office 365 security controls to the point where an Office 365 tenant can be more secure than an on-premises deployment of the same services.” (5 Steps for Securing Office 365.)
Even with the security of EOP, many organizations buy a secure email gateway to use as their primary security layer. To get the gateway to work as intended, you must redirect all incoming mail to flow through the gateway first. This involves changing your MX records and whitelisting the gateway. As recently as 2017, some gateways recommend disabling EOP during configuration.
When a secure email gateway is added to the mail flow, EOP either breaks or becomes the second layer.
It's not built for cloud cyberattacks
Since the early 2000s, gateways have secured email at the perimeter, because that approach worked with email architecture at the time. In 2020, the cloud requires a modern security architecture designed to block insider threats, identify anomalous user behavior, and quarantine attachment-based phishing attacks.
Secure email gateways analyze emails before Office 365 security, meaning they don’t leverage Microsoft analysis. Because they’re not integrated in the Office cloud, gateways can’t stop internal phishing. By 2023 65% of organizations will inspect their internal email traffic for phishing and malware, which is a major increase from 7% in 2019. Not inspecting internal email also means the risk of Business Email Compromise attacks rise dramatically.
Gateways have fallen behind the curve of innovation in email security. Many email gateways can’t scan URLs in attachments, even though this is a known vector for phishing links.
It's not delivering security via APIs
Unlike gateways, modern email security quickly manages the outbreak of phishing campaigns, learns the relationships between users at an organization, and scans intradomain email traffic without rerouting mail flow.
New detect and response capabilities are available via direct API-integration with G Suite and Office 365 environment. Gartner says as the market matures, “Traditional perimeter protection gives way to an identity- and information-centric strategy, which is focused on secure access and usage, complemented by threat protection via native capabilities, APIs or other mechanisms.” (How to Enhance the Security of Office 365)
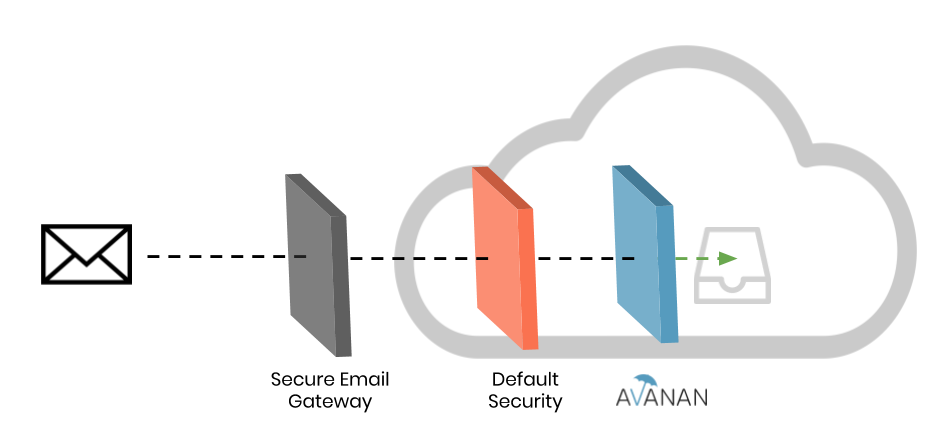
Avanan is the only cloud email security solution in this space that can stop phishing and malware attacks before they reach the inbox. Avanan uses EOP, gateways, and/or ATP as primary layers, then scans after them — before email arrives at inboxes at your organization.
Try Avanan Instead
Avanan builds email security with an architecture that supports the native security capabilities of cloud providers, and leverages identity plus behavior as an indicator of attack.








