Over the past two weeks, we detected (and blocked) a new SharePoint scam phishing attack that affected about 10% of Avanan's Office 365 customers. We estimate this percentage applies to Office 365 globally. PhishPoint marks an evolution in phishing attacks, where hackers go beyond just email and use SharePoint to harvest end-users' credentials for Office 365.
Essentially, hackers are using SharePoint files to host phishing links. By inserting the malicious SharePoint link into a file rather than the email itself, hackers bypass Office 365 built-in security. This leverages a critical flaw in Office 365, where their security focuses on email but neglects other Office 365 services.
How the SharePoint Phishing Scam Works
-
The victim receives an email containing a link to a SharePoint document. The body of the message is identical to a standard SharePoint invitation to collaborate.

-
After clicking the hyperlink in the email, the victim's browser automatically opens a SharePoint file. (File rights allow access to anyone with the link.) The SharePoint file content impersonates a standard access request to a OneDrive file, with an "Access Document" hyperlink that is actually a malicious URL.
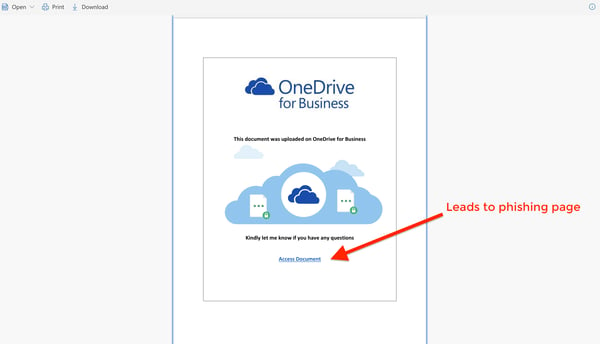 In this example of the attack, the SharePoint file was edited to impersonate a OneDrive document.
In this example of the attack, the SharePoint file was edited to impersonate a OneDrive document. -
The link within the SharePoint file shown above directs the user to a spoofed Office 365 login screen. When the user attempts to login, their credentials are harvested by the hacker.
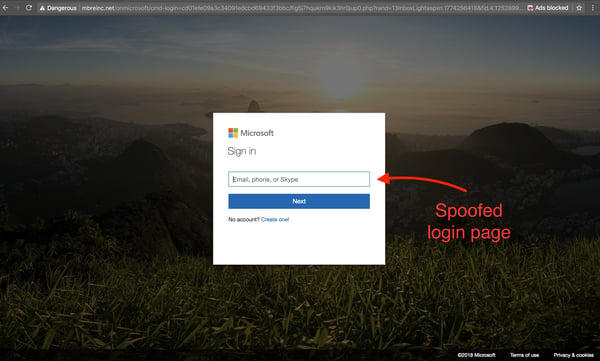
How PhishPoint Bypasses Office 365 Security
To protect against potential threats, Office 365 scans links in email bodies to look for Block Listed or suspicious domains. Since the link in the email leads to an actual SharePoint document, Microsoft did not identify it as a threat.
The crux of this attack is that Microsoft link-scanning only goes one level deep, scanning the links in the email body, but not within files hosted on their other services, such as SharePoint. In order to identify this threat, Microsoft would have to scan links within shared documents for phishing URLs. This presents a clear vulnerability that hackers have taken advantage of to propagate phishing attacks.
Even if Microsoft were to scan links within files, they would face another challenge: they could not Block List the URL without Block Listing links to all SharePoint files. If they Block List the full URL of the Sharepoint file, the hackers could easily create a new URL by uploading a new file with similar content to SharePoint.
How to Protect Yourself
Like many of the more nuanced instances of phishing we analyze, these attacks were designed to be visually indistinguishable from obviously work-related emails that appear safe.
Here are some best practices to protect you from PhishPoint attacks:
-
Be skeptical of any email subject line that capitalizes buzzwords for workplace stress, like URGENT or ACTION REQUIRED.
-
Be suspicious of URLs in the body of the email. (Because cloud service providers have pivoted the way organizations share and collaborate on their work, sending links through email is nearly an obsolete practice.)
When presented with a login page, look at the URL to see if it is actually hosted by the service it is asking you to log into.
If you receive an unexpected or uncharacteristic email from someone at your organization, contact them to ensure they actually sent it.
Activate Multi-Factor Authentication to secure your accounts on software platforms.
Although these best practices will help to avoid or identify these types of attacks, they are not foolproof. For instance, if the link were to trigger a malware download rather than direct to a phishing page, the attack would have caused damage by the time the user clicked and investigated the URL.
How Avanan Caught the SharePoint Scam
Avanan’s unique machine learning algorithm analyzes 300+ indicators of phishing to comprehensively scan every inbound, outbound, and internal email, as well as their attachments or links. These indicators identify irregularities in user behavior, authenticity, recipient-sender relationships, attachments, uploads/downloads, email subjects, and text, to name a few.
In the image below, Avanan's Smart-Phish technology found other indicators in the email that suggested this was a phishing attack.
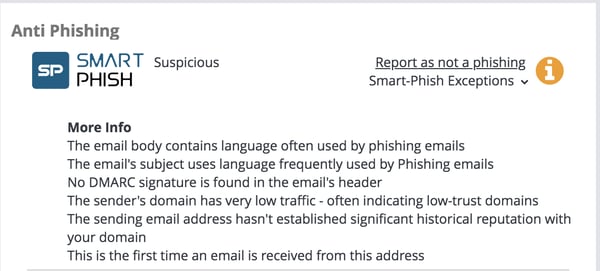
Since Avanan connects to all the Office 365 applications an organization uses, scanning them for malicious links and other threats, we flagged not only the email for phishing, but also the SharePoint file itself for containing a malicious link. Avanan does not rely on domain Block Lists, and can avoid the issues Microsoft would run into if they were to attempt to block this type of attack.








