We have written ad nauseam about something we call The Static Expressway. This refers to the idea of hackers using legitimate web pages to host or send phishing content to end-users. Because these sites are popular, they are often on static Allow Lists and end up directly in the end users; inbox.
We've seen this across a number of popular sites. See our latest examples on PayPal, QuickBooks, AWS, Google and more.
We've also seen this on sites that are designed for collaboration. We've seen it most recently on the chart and diagram site LucidChart; last year, we found it in Milanote.
Now, we're seeing an example of this Static Expressway that's targeting healthcare organizations.
According to the Department of Health and Human Services Cybersecurity Coordination Center, threat actors are using Evernote in an attempt to harvest credentials.
The email comes across as a "Secure Message".
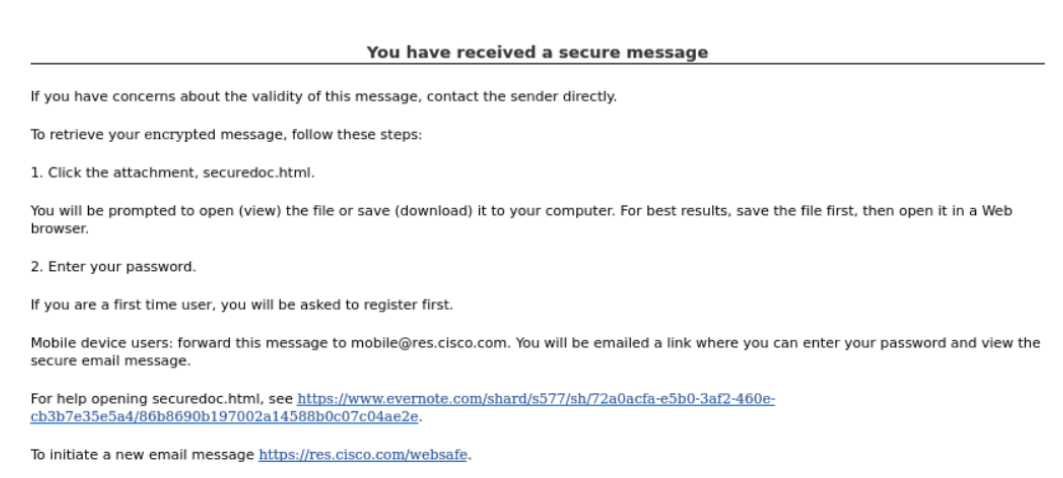
There's a link that goes to an Evernote page.
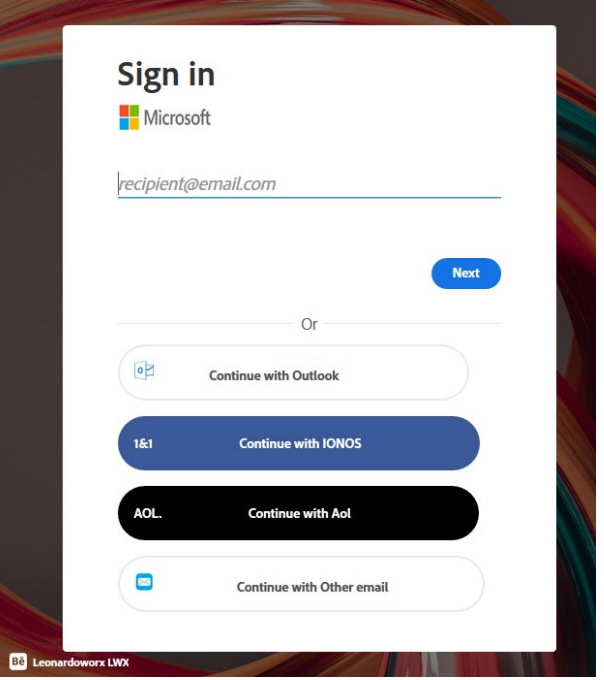
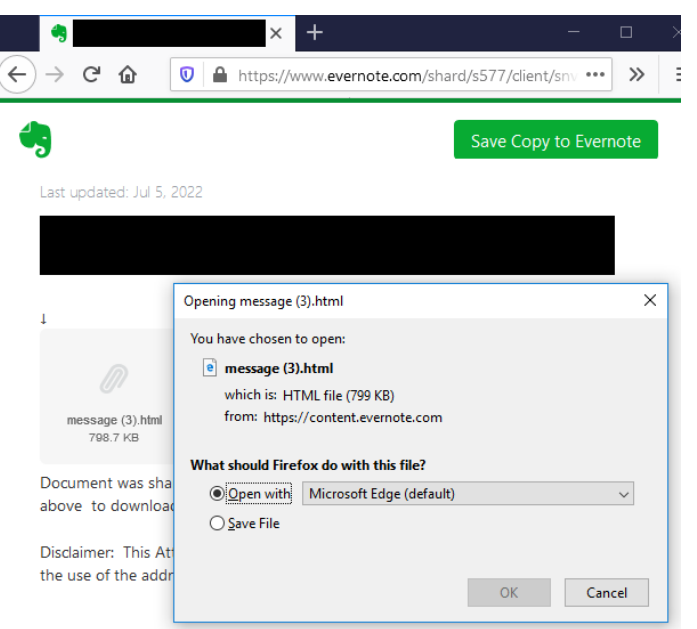 On On the Evernote page, there's a link that instigates an HTML download which is in fact a malicious Trojan. The file contains code that renders either an Adobe or Microsoft-spoofed login page to steal credentials.
On On the Evernote page, there's a link that instigates an HTML download which is in fact a malicious Trojan. The file contains code that renders either an Adobe or Microsoft-spoofed login page to steal credentials.
According to Check Point Research, attacks against healthcare have increased by 69% from H1 2022 over H1 2021. That is the highest increase across all industries.
For organizations under the type of assault that the healthcare industry is under, static allow lists won't cut it. Hackers will continue to see these popular sites host phishing content, knowing it will end up in their inbox.