Lucidchart is a popular site used to collaborate on drawings, charts, diagrams and more.
It’s favored by engineers and product managers, as it’s easy to integrate documents with flowcharts and diagrams.
This cloud-based tool is used by a whopping 99% of the Fortune 500. From diagramming business processes to data flows, the app has a number of uses.
Since it is such a popular site, it is more likely to be trusted by email security services. This is a tactic we’ve referred to as the Static Expressway. Static Allow and Block Lists condense the Internet by focusing on trusted sites to go through into the inbox.
Hackers know this, and so they embed phishing links into these shareable documents. The offending page is not scanned, and thus the phishing link goes undetected.
In this attack brief, researchers from Avanan, a Check Point Company, will discuss how threat actors are embedding phishing links in Lucidchart documents, using the site’s legitimacy to steal credentials.
Attack
In this attack, hackers are embedding credential harvesting links into Lucidchart documents.
- Vector: Email
- Type: Credential Harvesting
- Techniques: Static Expressway
- Target: Any end-user
Email Example #1
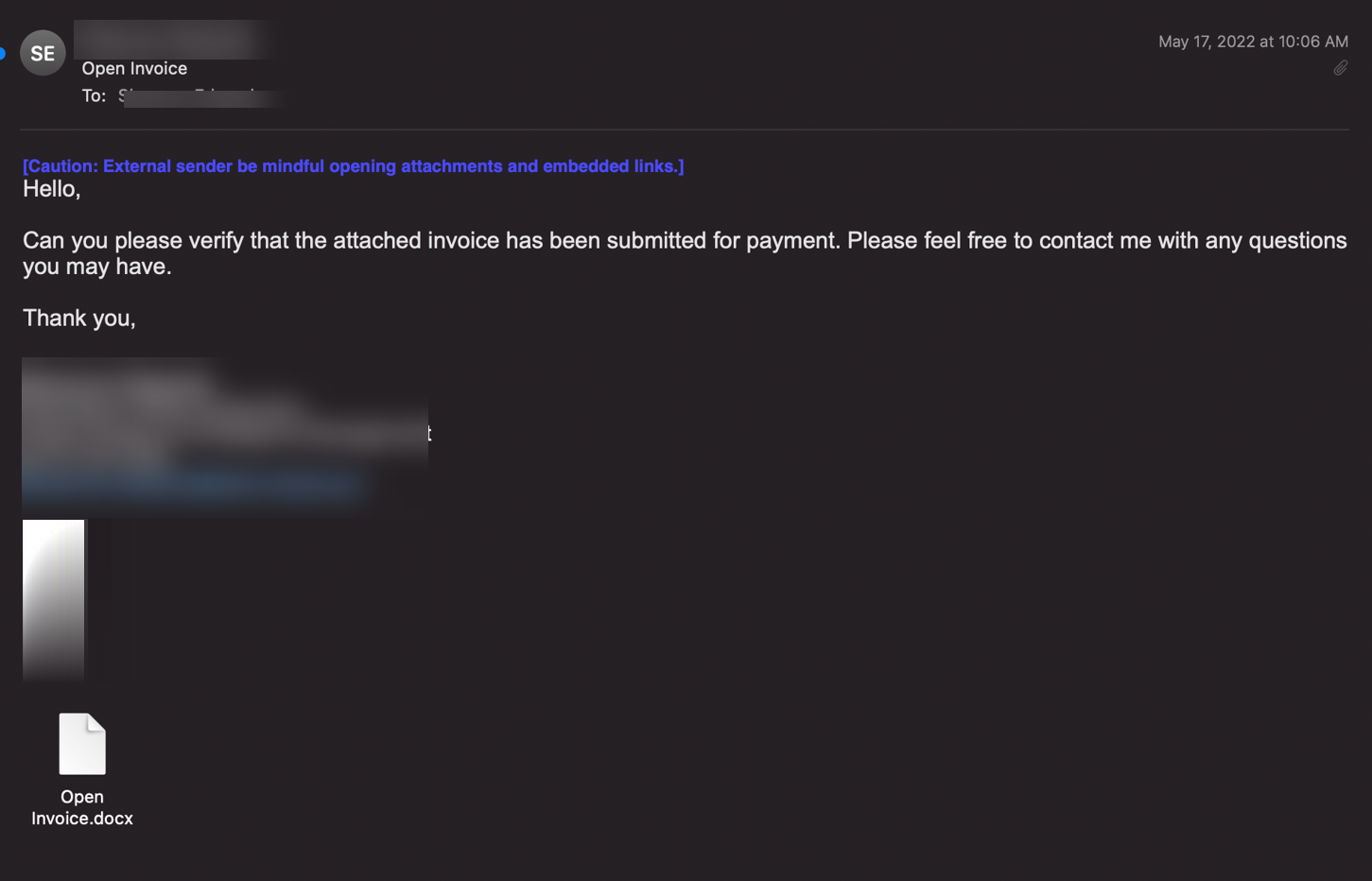
The user is presented with an email that asks to verify an invoice has been submitted for payment. The user is encouraged to click on the attachment, which says “Open Invoice”. The document goes to the Lucidchart page.
The Lucidchart page has a message saying a new document is attached. That “Open Docs” link goes to a credential harvesting page.
-png.png)
The user is then directed to this fake Microsoft login page, which actually steals credentials
Techniques
Hackers continually leverage legitimate sites to embed phishing materials that get delivered directly to the end-user. Whether it is PayPal or QuickBooks, we’ve seen a significant jump in these attacks. Because they rely on the legitimacy of the site, it is more likely to not only get into the inbox, but also be acted upon by end-users.
This particular attack takes advantage of classic social engineering techniques, like urgency. The “Open Invoice” subject line and document name imply that it hasn’t been paid, which could cause employees to act quickly. Further, since the invoice itself is not specified, users may be more likely to enter their credentials to see what the invoice is.
Combining social engineering with legitimacy is an effective way to get into the inbox and gain credentials from users.
Best Practices: Guidance and Recommendations
To guard against these attacks, security professionals can do the following:
- Always hover over any link to see the destination URL before clicking on it
- Encourage end-users to ask IT if the email is legitimate or not
- Encourage users to ask finance before acting on invoices