Before you continue reading, you should check to see if your email address is one of the millions that has already been compromised: HaveIBeenPwned.com. An attacker could have your account password without sending you a single piece of malware or phishing email.
What does a hacker do once they have access to your account?
As an email security platform, learning about hacker behavior is a significant part of what we do. When we deploy in a new customer’s environment, we go back in time to analyze months worth of event behavior that might include previous attacks and currently compromised accounts. What we have found is that the initial phish is often only the beginning, and the real attack takes place over a much longer period of time.
Our last blog post, Post-Breach Protection: What to Do When You're Already Compromised, gives an overview of some of this behavior and how to recognize it, but we think it is vital we provide a much deeper explanation of some of these methods. This the first in a series of blogs about each of the post-breach behaviors that we use to identify a compromised account. Because we assume that we may not see the actual compromise event (a user loses their password in a third-party breach, for example), we identify insider threats by both anomalous behavior and common attack behaviors.
The Alternate Inbox Method
Most attackers seek to take over a user’s email account in order to perform reconnaissance and compromise additional users, sending and receiving emails from the victim’s account in a way that avoids detection. One method is the “Alternate Inbox”.
The “Alternate Inbox” method describes the tactic of using an email folder, usually the trash folder, within a compromised email account in order to send and receive emails in way that is invisible to the owner.
How does it work?
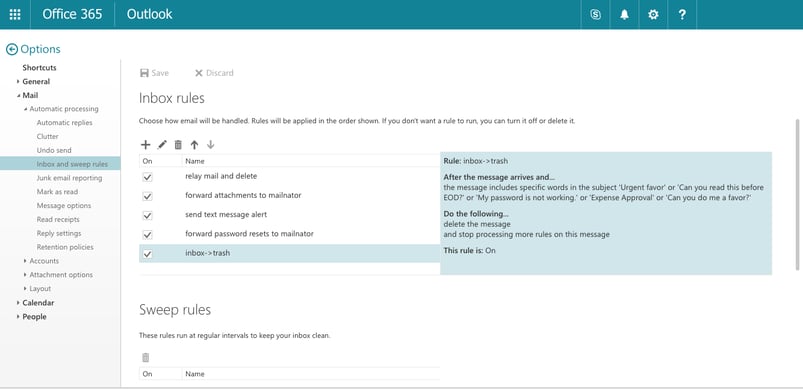
Once the hacker has gained access to an email account, they create inbox routing rules to move or delete emails with specific terms. A term might be the subject of an email they send to coworkers:
If subject = “Can you do me a favor?,”: move to trash
When the hacker sends emails with the subject “Can you do me a favor?” the original email will be deleted along with replies. The hacker can carry on a complete conversation from within the trash folder.
But what if one of the recipients of those emails gets suspicious? They may try and warn the user of the compromised account that they sent a phishy email. That is why the hacker often creates other rules of the form:
If email contains “hack”, “phish”, “account”: move to Deleted Items
Now the hacker can use the email account at their own leisure, as long as they keep their activities to the trash folder. Meanwhile, completely oblivious to anything being wrong, the owner of the compromised account is also using the same email account as the hacker but will likely be unaware of anything occurring outside the inbox and sent folder.
They may even create rules to forward attachments out of the company or text themselves, should they be discovered.
Why is it done?
This is done as a way to cover the tracks of the hacker as they attempt to move through an organization. Often the first account they compromise is not their end-goal, as it may not have administrative rights or have access to proprietary files. For this reason they will use internal email addresses to phish increasingly more important accounts until they can acquire what they are after. Sometimes this can take months.
How to Detect The Alternate Inbox Method
We use hundreds of metrics to look for compromised accounts, but these are some of the clues you can use to identify an insider threat.
- Logins from odd places or times: If you see logins coming from geographical areas that seem unfamiliar or at times when you are asleep, it can be a dead giveaway that your account has been compromised.
- New device login: It’s always a good idea to check for new devices accessing an account, they should all be your own. You should sign out all other sessions and monitor as you connect.
- New inbox rules: Take a look at your inbox settings and see if there are strange rules you did not create. Outlook-InboxRules for Office 365 and Gmail-Filters for Gmail.
- New folders: Check for new folders you didn’t create. Instead of using the trash folder, hackers will sometimes create new folders with inconspicuous names like “Reminders” to use as their inbox.
- Emails with many recipients: Looks for emails with multiple recipients in your trash folder and sent folder. Hackers may be sending emails with lots of employees in the BCC field to better their odds of compromising another inbox.
- Someone mentions getting an odd email from you: You might not see the malicious email, but someone you know might. Also, if someone sends you a suspicious email, use an external method of communication like the phone or text message to validate it. The hacked account may be theirs.
- Failed logins or password reset messages: If you find yourself having to reset your password for any of your accounts—banking, work, an attacker might have sent a password reset to himself through your account.
What to do if you have been hacked.
If a single account has been breached, you must assume that more than one account could be involved. We will go into more detail in a later article, but the response should be immediate.
- Logout all users and force the resetting of passwords upon next connection.
- Turn on 2-factor authentication for all users.
- Search all inboxes, outboxes and deleted emails for signs of the attack.
- Identify and remove any third-party SaaS that a malicious user might have authorized.
The damage that can be done is proportional to the administrative access of the compromised account, but the access rights of a single employee are typically enough to embed and spread throughout the organization, exfiltrating a tremendous amount of data along the way.






