In yet another example of a phishing campaign impersonating Microsoft’s voicemail notification, we see an HTML attachment that leads to a credential-harvesting URL.
These malicious HTML attachments use meta refresh to redirect the end-user from an HTML attachment hosted locally to a phishing page hosted on the public internet. Because the hacker uses this <meta> refresh tag to obfuscate the URL, the built-in link parsers of Office 365 (used by both the default EOP and E5 ATP) don’t detect the threat.
What is Special About MetaMorph?
What makes this wave of attacks unique is the way the URL is hidden using <meta> tags within the HTML attachment. Instead of focusing on the typical tags like <script>, <a href>, <link href> or <form action>, we see an uptick in <meta> refreshes that redirect from the local HTML file to a malicious public site.
- Example: <meta http-equiv=”refresh” content=”1:url=malicious.com”>
MetaMorph Obfuscation Attack in 5 Steps
Step 1
The victim receives a spoofed “Voicemail Notification” from Microsoft. Here’s the look of a standard email body in these <meta> phishing URL attacks.
Step 2
They click the HTML attachment at the bottom of the email.
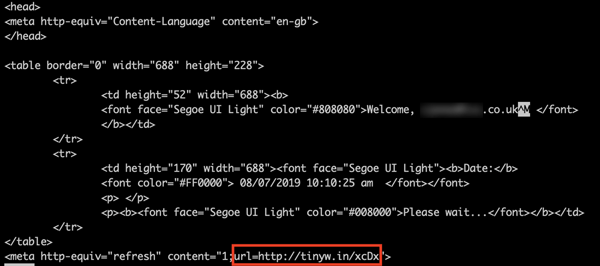
This is the HTML code for the malicious attachment, which is not seen by the user. At the end of the code, we’ve highlighted Tinyw.in — a link-shortening service. It redirects to the following compromised WordPress site:
http://mototamburi. [com] /wp-content/http/Vcenter/Listen/McrSoft/VM/
Step 3
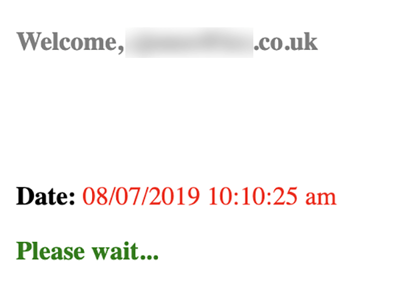
When the locally-hosted HTML attachment renders in the browser, this is what it looks like:
You’ll notice that the content of the HTML attachment is pretty sparse. It says the time (10:10:25am) and “Please wait…”
After a few seconds, the page will meta refresh to the tinyw.in URL from Step 2.
Step 4
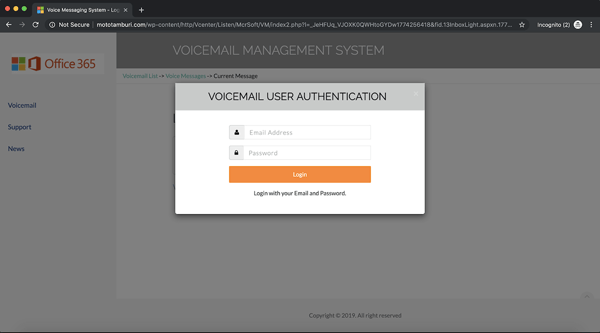
A spoofed login page loads. The victim enters their email address and password, which are forwarded to the hacker.
Step 5
Every time the form is filled with end-user credentials, it sends a hard-coded IP to the hacker’s IP: 37.111.130.203
This detail is unusual. Hackers typically don’t offer up information like this. The IP is geo-located in Pakistan, so we assume that it’s the hacker’s backend server IP.
Indicators of Compromise (IOCs)
|
IP |
37.111.130.203 |
|
IP |
81.169.146.213 |
|
URL |
http://mototamburi. [com] /wp-content/http/Vcenter/Listen/McrSoft/VM/ |
|
|
apache.serv.ssl.appdcxdcpxma1.notifications@post.webmailer.de |
|
Domain |
post.webmailer.de |
|
Domain |
hotsocks-ev.de |
|
SMTP Server |
cg4-p07-ob.smtp.rzone.de |
**Avanan clients are protected from the MetaMorph attack.
Summary and Immediate Recommendations
This attack builds upon the wave of HTML attachment attacks that we’ve recently observed targeting our customers, whether they be SMBs or enterprises. It adds another layer of sophistication to malicious HTML attachments with the <meta> tag, which obfuscates the URL to evade link analysis and redirects to a compromised domain on the public internet.
- Be suspicious of any email that contains an HTML or .htm attachment.
- Admins should consider blocking HTML attachments and treating them just like executables (.exe, .cab).
For a deep dive on HTML attachment attacks, check out our other blog, “HTML Attachments: The Latest Phishing Trend Targeting Office 365.”