The average person interacts with HTML every day while surfing the internet. Unless they are a UX developer or designer, however, they probably shouldn’t expect to receive HTML attachments in their emails.
If you’ve recently received an email with an HTML attachment, then there’s a growing chance that it’s a phishing attack. These HTML attachments host webpages on the victim’s device instead of the public internet, which is a strategic way for hackers to avoid URL reputation checks.
Malicious HTML attachments in these attacks use links, JavaScript, embedded images, HTML entities, and custom CSS to evade detection. Some attacks include sophisticated obfuscation techniques, such as the ones we found in the baseStriker and ZeroFont attacks. This attack is particularly dangerous in collaboration suites such as Office 365.
Immediate Recommendations
- Be suspicious of any email that contains an HTML or .htm attachment.
- Admins should consider blocking HTML attachments and treating them just like executables (.exe, .cab).
How an HTML attachment attack works
While users typically have to click on a link to reach a fake cloud/bank login page, hackers are now tricking them into downloading a fake login page. When a user downloads and opens an HTML attachment in the browser, the webpage is hosted on their device and not the internet, which requires a public URL.
Without a URL pointing to the phishing page, there is no reputation associated with it. This is convenient to the hacker because he or she escapes the strict HTML limitations enforced in email bodies while saving them the headache of hosting a phishing page on a compromised site.
1. Hackers send a phishing email with an HTML attachment to victims.
The HTML attachment contains a <script> tag, fetching a script from what appears to be HTML entities:
2. When the victim opens the attachment in the browser, HTML rendering converts the HTML entities into a URL.
This is the HTML-entity-decoded <script> tag looks like, revealing the hidden URL of a malicious JavaScript file:
3. The JavaScript file hosted in the URL contains escaped code.
The browser, rendering the HTML, automatically fetches the JavaScript file from the URL.

The code in the JavaScript file looks like gibberish but actually, it’s escaped JavaScript: code that has been converted into hexadecimal to make it unreadable to humans and most security tools.
The escape function is considered undesired/depreciated and is not recommended for usage under JavaScript’s current best practice.
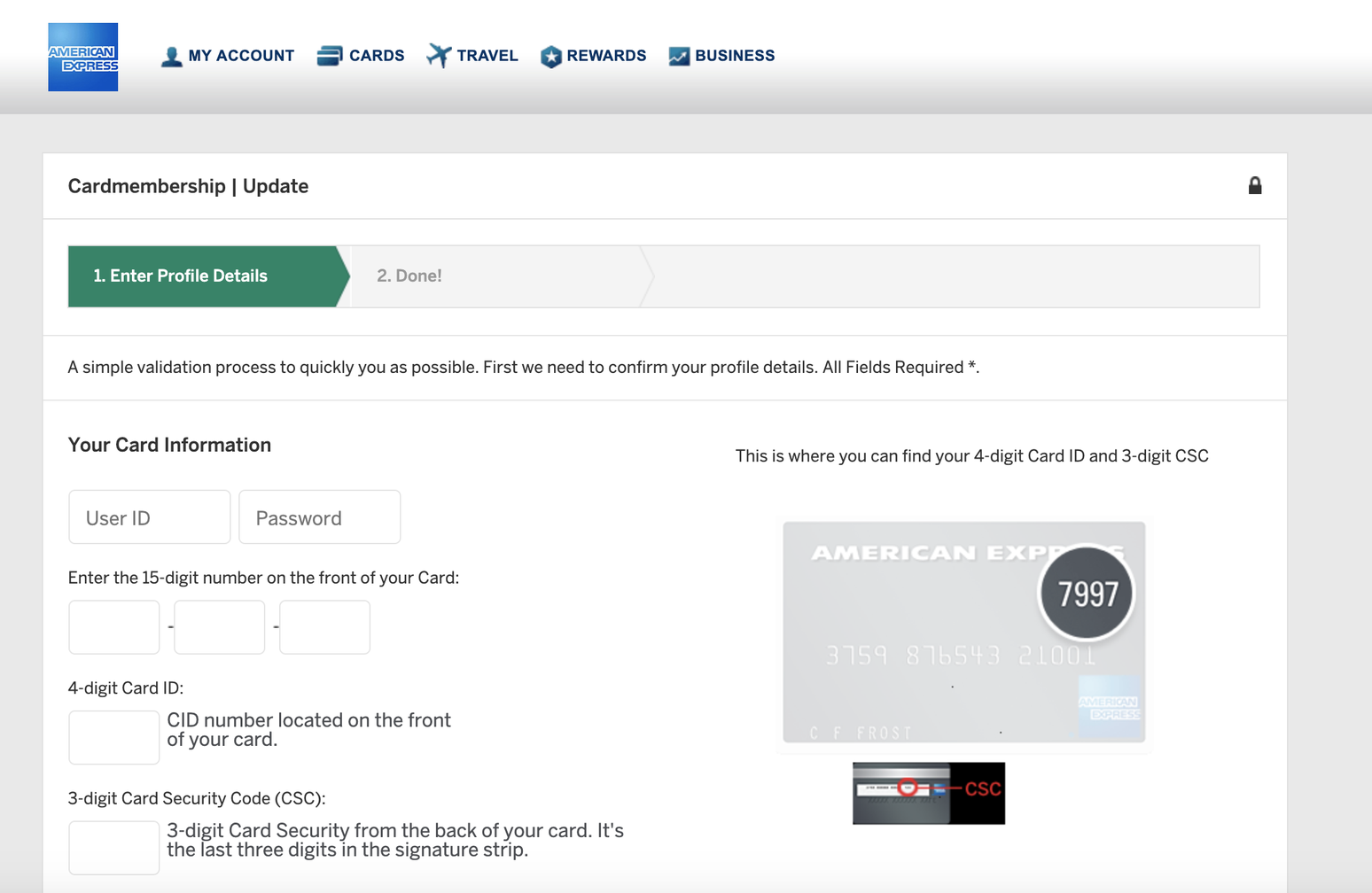
4. When the JavaScript is unescaped, the browser loads a malicious page with an American Express banking form.
After the browser fetches the JavaScript file, it executes the JavaScript unescape command. This converts the hexadecimals into code that creates HTML. The HTML, as seen in the image below, contains embedded images (base64 encoded), a form, and most importantly, a visually appealing page that begs for sensitive information. When the user submits their information into the HTML form, it is sent to an external server managed by the hacker.
Summary
These attacks bypass security features, especially when coupled with links, JavaScript, CSS, embedded images, and HTML entities. You should report any email with an HTML attachment for further investigation, because it likely leads to a credential harvesting page.






