Last week the National Law Review published a short news article about the massive data breach that happened through email at the Henry Ford Health System. What they didn't publish is that this customer has been using Proofpoint, a leading email security provider, to secure their email security.
No security is 100% and we definitely don't want to pick on a security vendor at their moment of failure, it could happen to anyone and Proofpoint is securing many leading companies every day. We also already covered the reasons email security platforms that worked for on-premises email, fail to protect against today's advanced phishing attacks on Office 365 and Gmail here, and here.
This blog is about the importance of protecting against account takeover. We will be discussing the oft forgotten security layer that springs into action after a successful attack when hackers are finding a way in to the compromised account.
Phishing through email has become the number one security issue for most companies. In the age of SaaS based email, it appears to be even more dramatic because as most organizations move to Office 365 or Gmail, stolen credentials is all that the hackers need in order to get into the account. Since the same credentials also grant the hackers access to OneDrive, Sharepoint or Google Drive, once they're in, they have access to the entire Office 365 or G Suite environment.
The Challenge
Adding an Anti-phishing security layer is a must. If you are using Office 365 Email or Gmail and still haven't deployed anti-phishing, then you should absolutely start there. Google and Microsoft don't solve this problem well, mainly because the hackers test their attacks against the default security until they are able to get through. We explain the challenge Microsoft is having in our blog post, Five Reasons Microsoft Doesn't Secure Office 365. We also discuss why the legacy email security platforms, like Proofpoint and Mimecast, are struggling with similar challenges in a recent post, Why Proofpoint and Mimecast Can't Secure Office 365 and Gmail.
Even if you already have an anti-phishing layer, you still haven't completely eliminated the risk of account take-over. First, security is all about layers. Any anti-phishing is not 100% and hackers may have multiple other ways to get their hands on your end-user's credentials. Whether it's a man-in-the-middle attack when connecting through a shady WiFi, or an end-user that used the same credentials for another account that was then breached (Like we've seen with the massive LinkedIn and Yahoo breaches that happened recently).
So, CISOs can never assume that credential harvesting will not occur and that an account can not be breached. This is where account takeover protection becomes an important part of the security puzzle.
Some believe Microsoft and Google already provide some detection of suspicious logins but they generally focus on the web-login itself and not on IMAP/MAPI logins, and hackers have reversed engineer that security in their lab environment and found ways to avoid its detection. Legacy email security solutions don't even claim to have an answer, they focus solely on the email flow.
Protecting Against Account Take-Over
In the world of SaaS, a username and password is all the hackers need to take over all of your accounts. There is no need to put malware on your endpoint or get in through a Firewall. In fact, there is very little practical security after they have your username and password.
Educating your users on how to spot phishing attacks is important, but attacks are getting so good that there is often no way to differentiate an impersonation email from a real one, even for a savvy and educated end-user.
Trying to deploy MFA? if your end-users are not tech savvy and/or if your organization is larger than just a few end-users, you will face difficulties implementing MFA, or will have to increase the helpdesk center to handle the dramatic increase in end-users support calls.
First Generation Solutions
The idea of account take-over protection is not new. The first generation of these technologies relied on two main data monitoring techniques - monitoring suspicious logins and monitoring end-users' activities. Customers added these layers to their SSO or their SIEM and started to track geographically suspicious activities, simultanious logins, massive downloads etc. These methods were good but deployment was limited for several reasons:
a. They require an SSO or a SIEM. Deployment of these can be a large undertaking and detecting account take-overs is only a small part of their intended use.
b. SSOs only look at login events and are blind to what happens next. This isn't helpful if the suspicious activity is not the login itself, for example when the hacker was smart enough to login from the same GEO and at the right time-of-day. What if the suspicous activity is a massive download of files or sending 1,000 emails in 1 hour? SSO could not see those events and could not protect from them.
c. SIEMs don't apply automated action. Some of them claim to take action, but since they are intended to be monitoring platforms, SIEMs do not truly prevent anything from happening. They don't detect in real-time so they can't auto-remediate.
d. False positives are probably the most important issue, especially for SIEMs. What could be considered an anomaly, may also happen regularly within the legitimate end-user activity. Customers that are getting 100x false-positives and and therefore can't in good conscience take automated actions. After a while, end-users will stop paying attention to these alerts.
What Can You Do?
Using the breadth of data SaaS applications are able to provide via their APIs and running it through a machine learning algorithm, Avanan implemented a focused security layer that doesn't rely on a SIEM or SSO. For each SaaS app our customers have installed, we monitor for:
- "Superman" logins (Same user, across SaaS from remote GEOs in a short time)
- First seen in a new country
- First seen with this device
- Unusual number of used devices
- Suspicious Configurations like Forward-all-to-outside-email (Office 365 + gmail)
- Suspicious emails like an unusual number of BCC in an email (compared to to other emails in the user's history)
- Login outside a defined geography
- Multiple failed login
- Same machine with login by multiple people
- Same machine sending an email and trying to login (Some hackers use hacking tools on their PC to send out phishing emails and then login to O365 from the same IP)
- Session characteristics such as length, time-of-day, behavior (For example, sending emails without reading emails, to spread an attack)
- Existence of suspcious configuration changes (For example, a Gmail rule that deletes all incoming email to hide tracks of a hacker)
- Disabling MFA
- Unusual number of 'reset password' emails received by a user
- Email rules that hide incoming emails
- Email rules that leak data to outsiders
- Phishing emails originating from an internal user
- Suspicious activity that follows the reading of a suspicious email
- Tokens with access given to low-reputation applications
- And others... (Total of over 100 indicators)
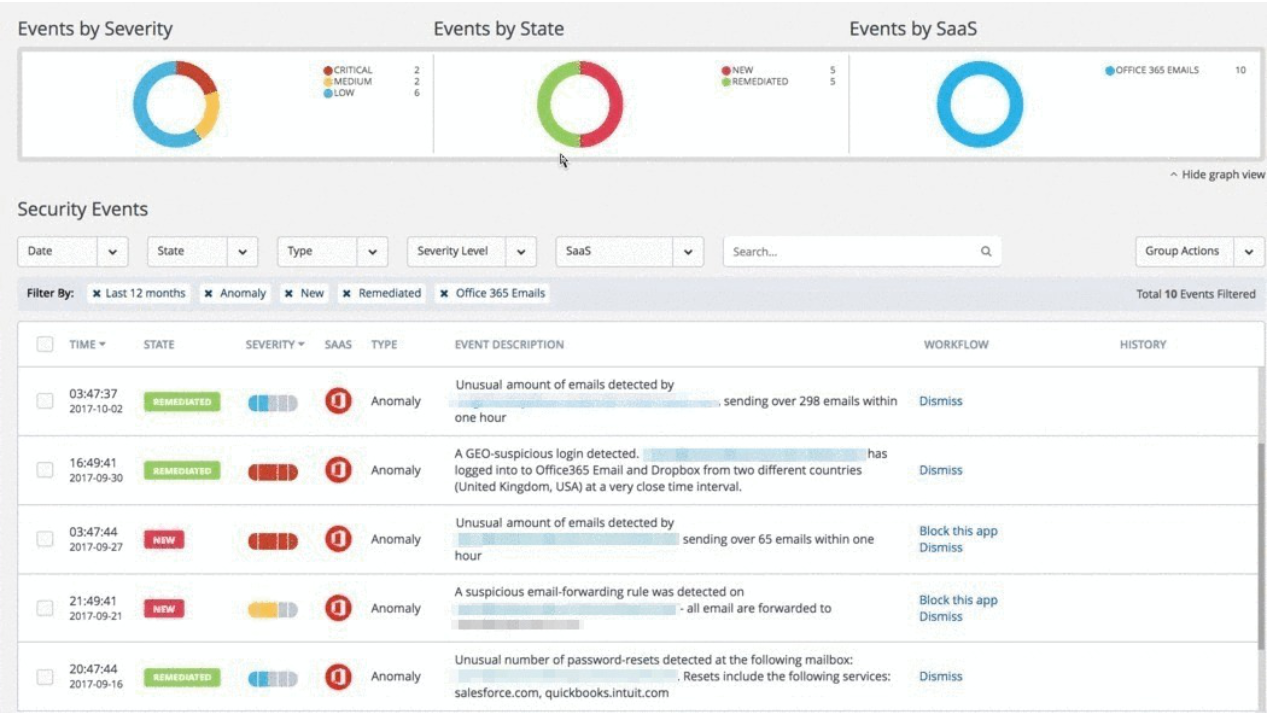
A customer who was the victim of an account takeover (From the Avanan Portal)
How Is The Avanan Solution Different?
You might feel that you have seen these detection methods before (and you probably have). What is unique about the Avanan solution is that those indicators along with many more, are fed into a Machine Learning algorithm that is trained to find attacks and to filter out false-positives. For example - a user that starts using a new device is something you expect to see often, at larger organizations this event can easily happen multiple times a day. However, seeing a new device at an unexpected time of day from an unexpected geo-location and demonstrating irregular behaviorsfor this particular user - increases the likelihood that this is indeed a compromised account. Avanan collects numerous real-world incidents of acount take-over events to train our AI algorithm to find real compromised accounts at a high-accuracy while minimizing the likelihood of false-positives.
In addition, as soon as you connect the Avanan platform to your SaaS, it start scanning all historical activities. This allows us to go back to history and find the accounts that are already compromised. In a few of our customers, we found the hackers broke into the accounts of key people, such as the CFO, and waited quetly in ambush for 6 months waiting for an opportunity to monetize based on one of their schemes.
Real-time is also key for an effective security layer. Finding out that an account was taken over immediately after the malicous login is critical to prevent the hackers from gaining access to what they shouldn't see or using the account as jump-board to launch additional attacks.
So, now that you have accurate detection in real time, what next?
Automation
Automation is important because you often don't have time to wait for someone to review every event. It is vital to revoke the hacker's access to the account immediately before any damage is done. In addition to a low false-positive rate, your automated protection should include a method for end-users to manually remediate themselves because if it's not 'self-service' then you are relying on helpdesk calls and have users getting locked out of their accounts.
Common automated actions for account takeovers include password reset or retriggering MFA (Where applicable). The SaaS service themselves often have a built in mechanism to retrieve lost password (i.e. back-up accounts, an SMS to a mobile phone, or a secret question). By initiating this process the end-users can manually set a new password to replace the one that may have been compromised.
Summary
As organizations move their email platform to SaaS based email: Office 365 and Gmail, account take-over becomes easier for hackers because all it takes is the username and password. It also becomes more valuable because all the corporate data resides in the cloud both in the emails and the other services of the suite such as OneDrive, Sharepoint and Google-Drive.
A best of breed anti-phishing solution is a critical component, but is not enough because legacy email security solutions have limited success blocking current phishing attacks and because users can lose their credentials in other ways. Therefore, adding a post-attack layer to detect account takeover is a critical part of email security.
Traditional MTA-based email security platforms like Proofpoint and Mimecast cannot add this layer because they only analyze the email traffic and not the end-users' activity in the account. This is one of several reasons legacy email platforms have struggled to properly security Office 365 and G-Suite.
An effective account take-over security layer needs to detect and respond in real-time. It has to be automated when taking action and therefore it also has to be accurate and allow self-remediation for the end-users. In addition to this, it must also be able to review historical data, which can provide useful indicators of compromised accounts and give insight into what range of behavior should be considered anomolous for each end user.
To learn more about how to protect from phishing and account takeover on the Avanan platform, schedule a demo or start a free trial.







