Introduction
Hackers want you to think that you’re doing an expected action, when in fact you’re doing something you shouldn’t be.
They want you to enter your login credentials in a page that looks secure, but actually isn’t. They want you to reply to an email that looks like it comes from your boss, but doesn’t.
In this case, they want you to click on a link that looks like one thing, but is in fact another.
In this Attack Brief, researchers at Avanan, a Check Point Software company, will discuss how hackers create “magic links” that transform from safe to malicious upon pasting in the browser.
Attack
In this attack, hackers are creating magic links that change into the intended destination upon pasting.
- Vector: Email
- Type: Malicious Link
- Techniques:URL Deception, Obfuscation
- Target: Any end-user
Email Example
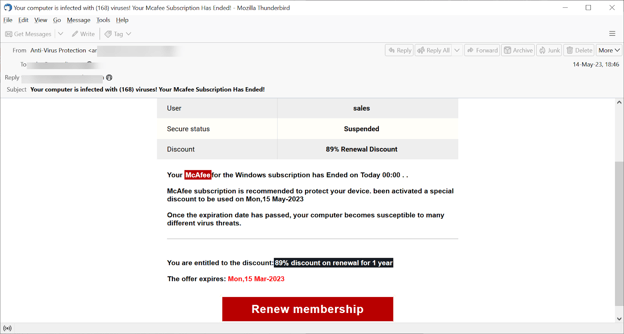
This is a fairly standard McAfee subscription scam. We see these all the time and they’ve been floating around the Internet for some time. But that’s not what makes this attack unique. What makes it unique is what’s hiding under the Renew Membership button.
It’s linked to the following IP address: 0xd.0125.0x50.0236.
But, let’s see what happens when we place that into the address bar:
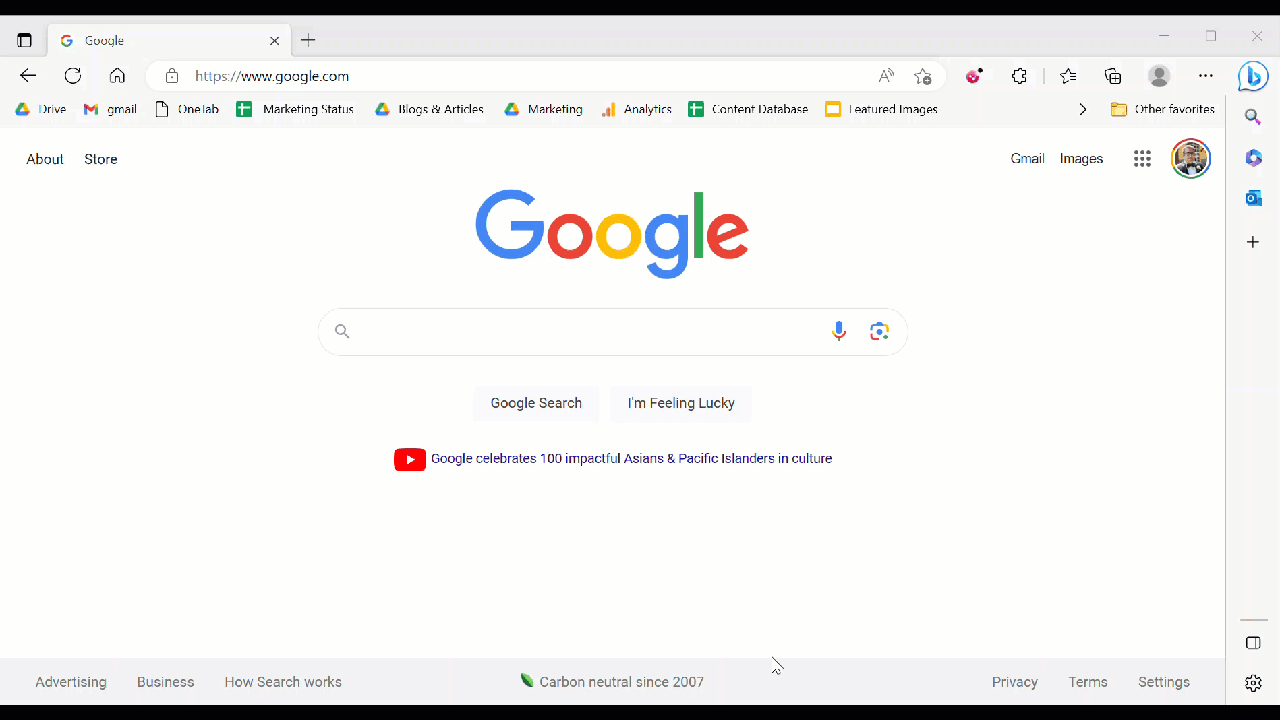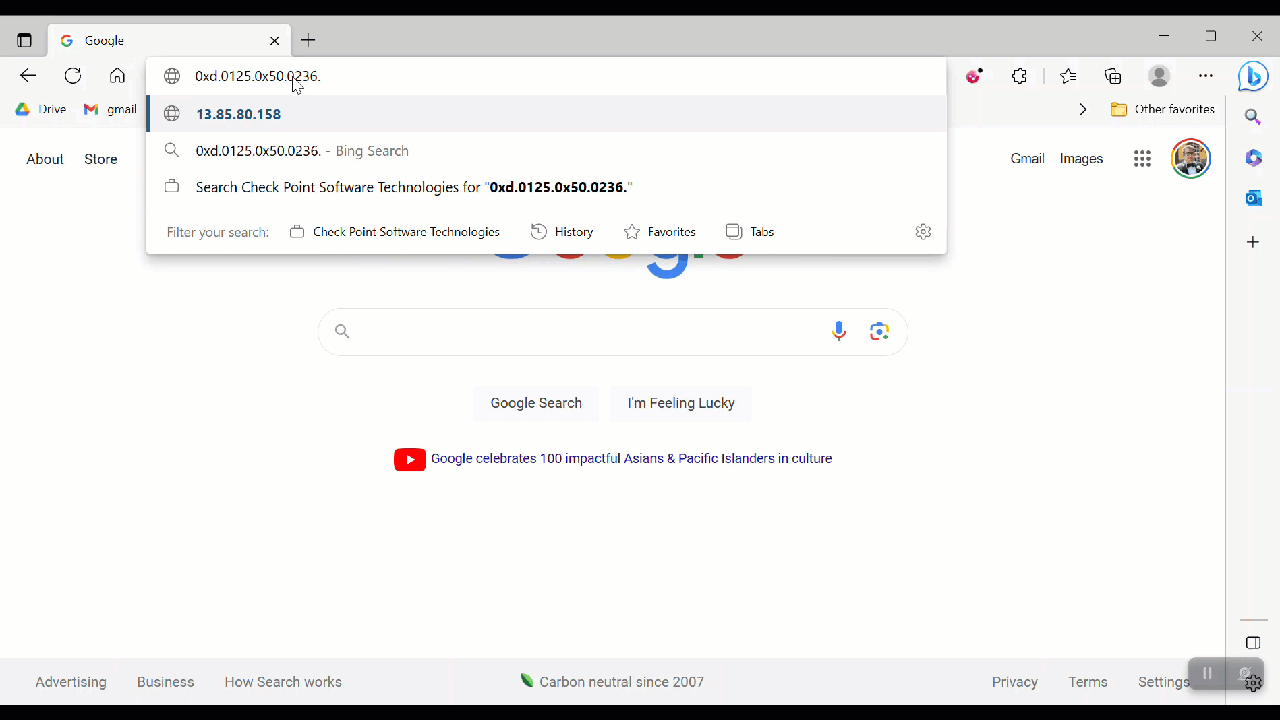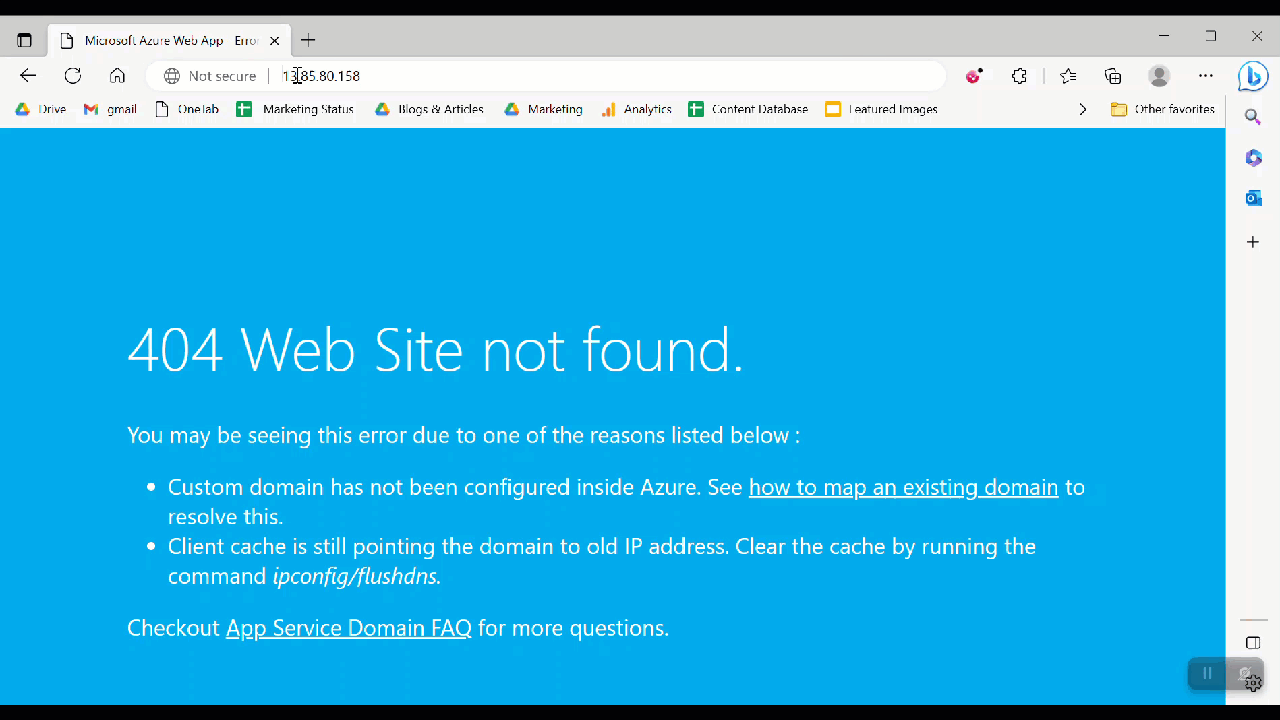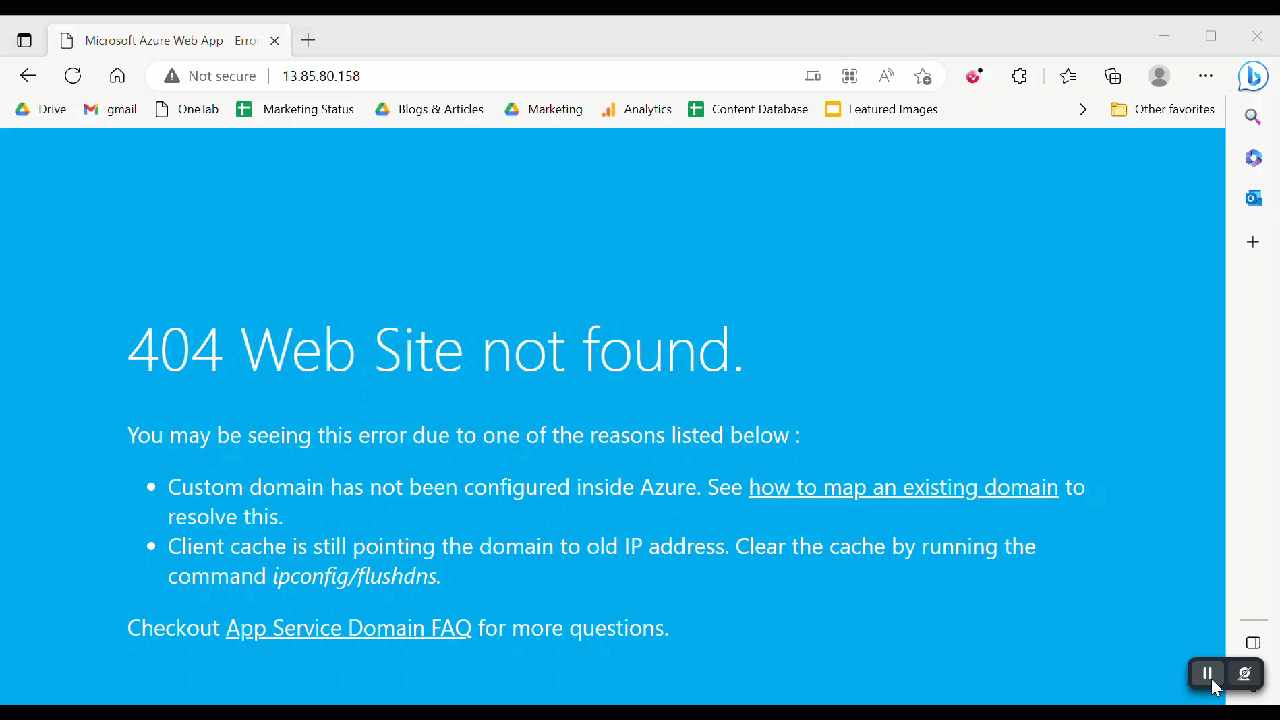
What kind of sorcery is this? We copy and paste the original address and it transforms upon click into something else.
That page has since been taken down (hence the error message). But how does it change?
There’s a lot of behind the scene coding here. Most likely, this type of IP format is called a “hexadecimal” format. This means there’s obfuscation that starts with 0x, and that decimal encoding was used.
Before it was taken down, the link led to the web server running on that IP address. From there, the server can do a few things–it can show malicious content, force a malicious download or redirect the user to another malicious site.
Techniques
One of the most potent tricks in the hackers’ toolbox is obfuscation.
Show the end-user one thing. Show the computer another.
We’ve covered these extensively over the years. There’s MetaMorph and OneFont, NoDisplay and ZeroFont, SiteCloak and Blank Image, and much more.
What’s happening is that attackers are hiding the intent of the target page. Because URL filters are unable to determine the intent of an obfuscated page, the malicious email can reach the inbox.
The idea is to blind anti-phishing scanners so that they can’t see the danger. This allows the end goal, in this case, malicious sites, to more easily make the inbox. And since users can’t see the obfuscation, they are more likely to click.
This email is probably not the hackers’ strongest offering–the McAfee renewal scam has been around forever. The sender address isn’t legitimate. The reply-to address is different from the sender address. The link–both the seen version and the magic version–aren’t typical links, they are just IP addresses.
So there are many things that would tip off an eagle-eyed end-user.
However, what this attack demonstrates is hacker ingenuity. It shows the creativity of modern hackers. By utilizing a magic link, they can bypass typical URL scanners and get their intended malicious page into the inbox.
This is part of the cat-and-mouse game of cybersecurity. Hackers find vulnerabilities that obfuscation can take advantage of; security systems, like Microsoft or Google, will patch it. And then the hackers will find another. On and on it goes.
Caught in the middle are end-users, who will receive these emails and are none the wiser to the trickery going on behind the scenes.
Best Practices: Guidance and Recommendations
To guard against these attacks, security professionals can do the following:
- Implement security that looks at all URLs and emulates the page behind it
- Leverage URL protection that uses phishing techniques like this one as an indicator of attack
- Leverage AI-based, anti-phishing software capable of blocking phishing content across the entirety of the productivity suite.






