Highlights:
- Avanan researchers have identified an aggressive attack against higher-education targets that uses a number of obfuscation techniques developed by the SPAM-EGY group to bypass Microsoft 365 email filters and send users to a personalized login page.
- The fake Microsoft 365 login page dynamically updates to match the look and feel of the targeted school, even fooling users that might take basic steps to detect a scam.
- This attack bypassed both EOP and ATP, but was caught by Avanan.
SPAM-EGY and Education
Avanan researchers have identified an aggressive attack that uses a number of obfuscation techniques to bypass Microsoft 365 email filters and send users to a personalized login page. The specific code is what we call ZeroFont, which still fools Microsoft's Natural Language Processing abilities nearly two-and-a-half years after we first identified it. There are many variants of it, but in general, ZeroFont injects very small characters between the letters—invisible to the user, but not to the Microsoft scanners, allowing it to bypass the defenses and phish the user.
The Attack: This particular campaign is being carried out by SPAM-EGY, an advanced persistent threat group that guarantees access to the inbox. This specific campaign has been targeting universities.
The typical email looks like a link to a Microsoft document share. Clicking on the document link, takes them to the phishing page. Even if the victim uses the client mouse-over 'preview', it looks like their familiar university login.
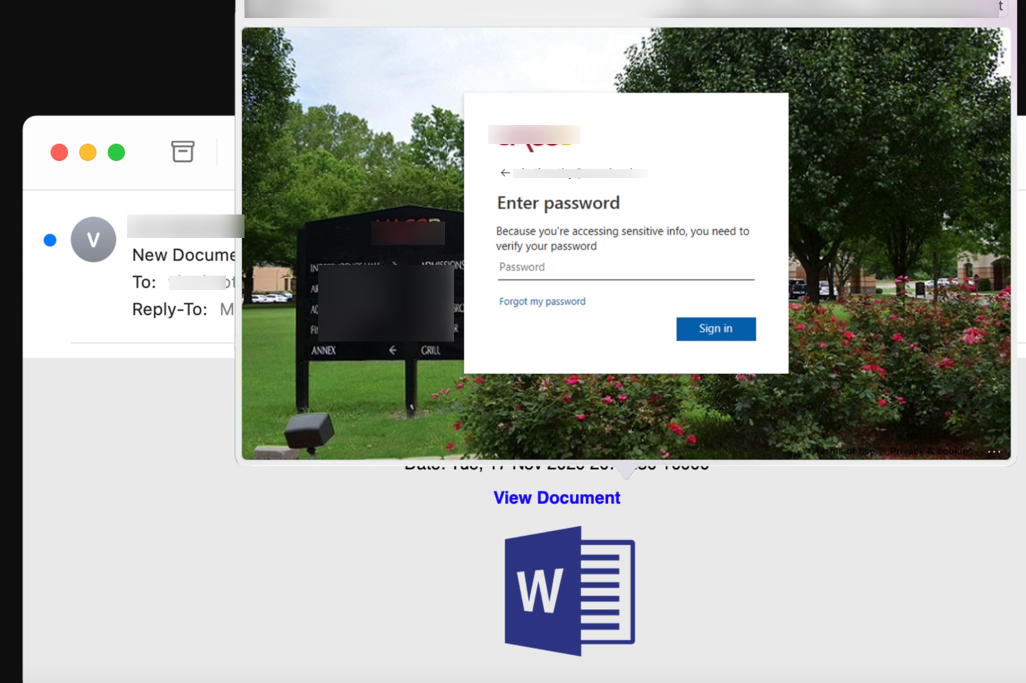
This is because the when you click on the "View Document" button, you are directed to a dynamically-rendered page that matches the look and feel of the university's Microsoft login. Not only does it pre-populate the email address, it updates the logo and background to match. (The universities shown here are examples. It works with any organization that uses Microsoft 365.)
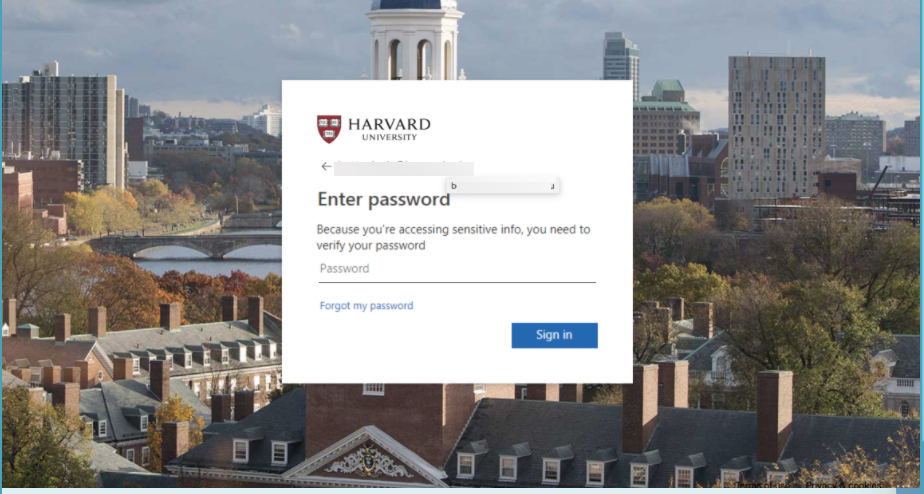
But here's the impressive part. The code actually imports the school’s login page on the fly so that it is an exact match. If you change the URL of the email address, it updates the background to match. And it's a bit-for-bit mirror of the actual site. We programmed in an email address for Columbia University. Look what comes up:
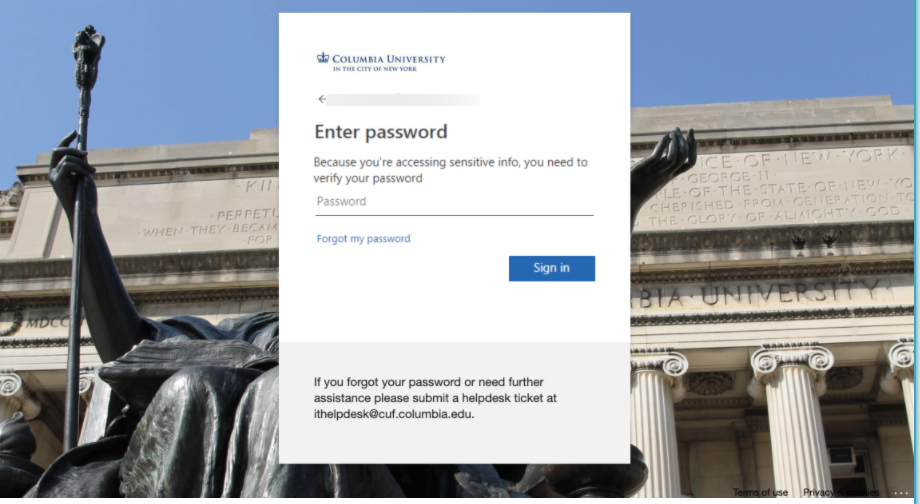
Any college works and the recipient get the exact same login window that they expect to see. Students and faculty from statecollege.edu, will see the statecollege.edu login page and background.
How does this email get past Microsoft? (And remember, this passed by both EOP and ATP.) The classic ZeroFont obfuscation technique. Here's what it looks like to Microsoft:
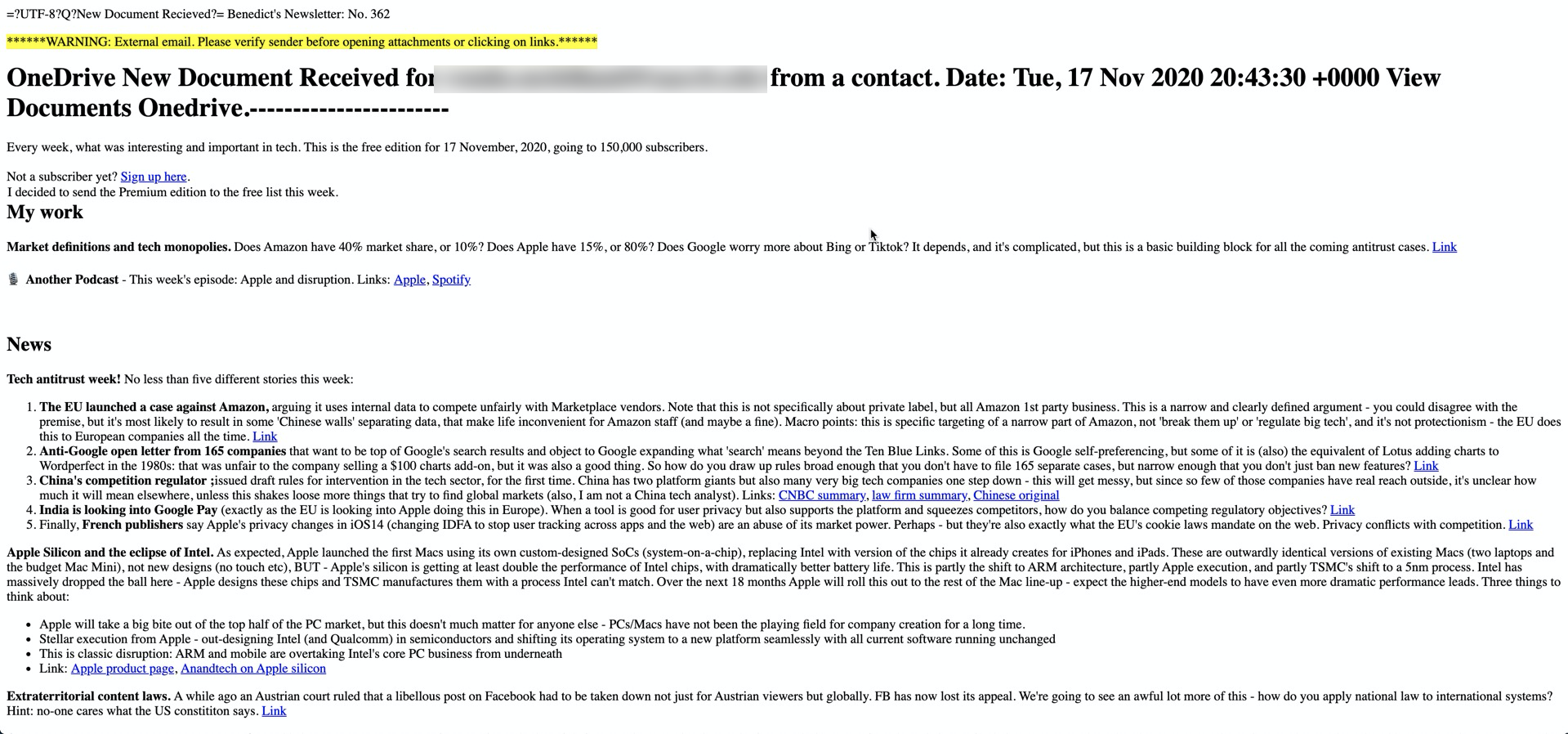
When read by Microsoft filters, it appears to be a newsletter, but to the end-user, it is a document share.
We've written a lot about Zero-Font and its variants. Essentially, hackers insert hidden words with a font of zero. It's invisible to the recipient but it fools Microsoft Natural Language Processors.
The group behind this clever attack is a persistent threat organization called SPAM-EGY. And by using ZeroFont, they claim "10,000% access to the inbox". .
SPAM-EGY is "Phishing-as-a-Service" subscription organization that guarantees:
- The ability to reach the inbox using ever-changing obfuscation methods,
- Re-direction to a phishing page that appears to be the second page of the Microsoft 365 login with a pre-populated email address.
- Dynamically-rendered landing page that changes the logo and background to match the domain of the email address.
- The landing page will either request the email twice as validation or, optionally, attempt to use the credentials in real-time in order to verify the password.
- If the password is good, the user will be directed to a real document or to the Office.com home page.
- Once the user has entered their credentials, a cookie in the browser will render the phishing page 'unreachable', frustrating any further analysis.
And though they have stopped their frequent YouTube and social postings, they are still attacking end-users every day.
Their arms race with Microsoft filters typically grants them a few weeks or months of access before the Microsoft response requires a new release.
Today, we are seeing a targeted campaign using these SPAM-EGY techniques. Because each phishing page is embedded with their "Phishing-as-a-Service" license key and email address, we can track the group that is using the SPAM-EGY service to attack these universities:
var arrl = “Enter vic.tim@university.edu”;
var licensekey = ‘UZER58ERE8RWV4’;
var emailkey = ‘cmVkYWN0ZWRoYWNrZXIxODE4OUBnbWFpbC5jb20=’;
Of course, this is not the only attack targeting higher education this season. University-targeted Ransomware is on the rise and it seems that they are taking advantage of Covid-confusion to step up their campaigns.
Join our upcoming webinar on Thursday, December 10th to discuss these attacks and more.
And make sure to subscribe to our Attack Alerts for the latest on SPAM-EGY and all other attacks.









