Lookalike domains are a big problem in the world of phishing. Just a subtle difference leads to untold damage.
Here's how it works:
- A threat actor finds their way into an employee's mailbox, usually through a phishing attack
- The threat actors then monitor emails for information about invoices, billing or anything finance-related
- From there, they create a lookalike domain and insert themselves into an existing email thread
- Final step is convincing the target to wire funds to their accounts. Because they appear to be a real colleague, it doesn't seem out of the ordinary
This can lead to massive losses that are hard to recover.
How to guard against this? We can trigger specific workflows when the sender domain closely resembles the domain of a partner.
We have a comprehensive list of partners from our Partner Risk Assessment dashboard. And we can use that as a baseline for phishing detection.
When an email comes in from a new sender in a domain that was recently registered, and the domain closely resembles the domain of one of your partners, the Anti-Phishing engine will consider it as a potential phishing indicator.
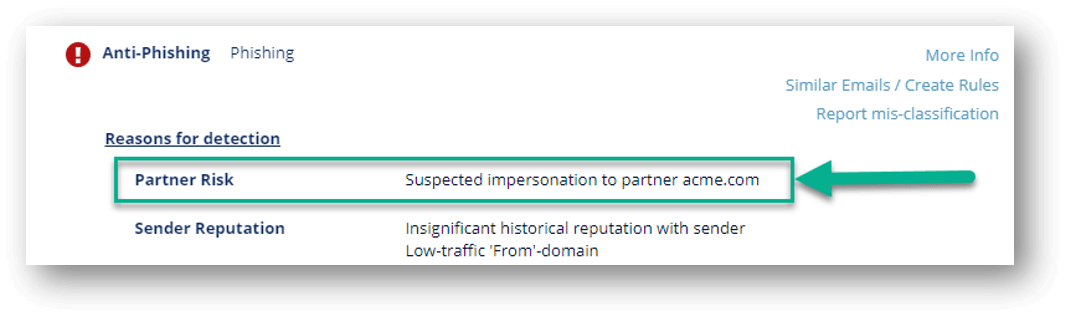
We then allow for workflows in this scenario:
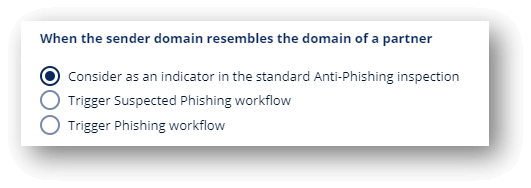
Businesses need email security that not only monitors but prevents these attacks.






