Today, we’re writing about cyberattacks we’re seeing via Google Looker Studio and other Google applications. Google Looker Studio is a powerful data visualization software tool. Cybercriminals figured out they could use it to create visualizations to send realistic phishing materials. This attack was first seen on July 13, 2023, and we have seen over a hundred of these attacks since then.
Here’s how it works. Someone creates a Google document or Google Looker Studio page and shares it with a colleague or friend. The recipient receives a notification directly from Google, saying that someone has shared content that is awaiting comment or reply, via a click. The email comes directly from Google and is in fact legitimate. The recipient’s email security service would not and should not block that, because it is legitimate from Google. When the link is clicked, it directs to the Google Looker Studio page, Google Doc or Google Slide. That page is also legitimate—it is a Google page. There’s no spoofing. But embedded within that page, is a link that redirects the recipient to an external page designed to try to steal their credentials and other crypto-related information.
Why is this significant? Previously, cyber criminals spoofed Google in their phishing emails. They did this by using email accounts that were similar to google.com. The URL might have an extra ‘o’ in it, or an extra ‘g’. Or maybe the URL is completely different and the logo is a bit off. These types of phishing attempts are easy to identify.
But in this new attack, it’s more difficult. The email is actually coming from Google—the call is coming from inside the house. Google is not being hacked or exploited here. Rather, hackers are creating free Google accounts like anyone can, and then putting malicious content onto a Google page. When they send that page, both email security services and users see that it comes from Google and think it’s safe. And then when they click on the link in the email, that also goes to a Google page. It’s only when they click on the link on the Google page that the danger is apparent. And by then it’s too late.
Attack
In this attack, hackers are utilizing Google Looker Studio to host credential-harvesting crypto sites.
- Vector: Email
- Type: BEC 3.0
- Techniques: Social Engineering, Credential Harvesting
- Target: Any end-user
Email Example
This attack starts with an email that comes directly from Google, in this case Google Looker Studio.
Hackers have created a report within Looker Studio. The email has a link to the report, saying that by following these investment strategies, users have seen a nice return. To access your account, just click here.
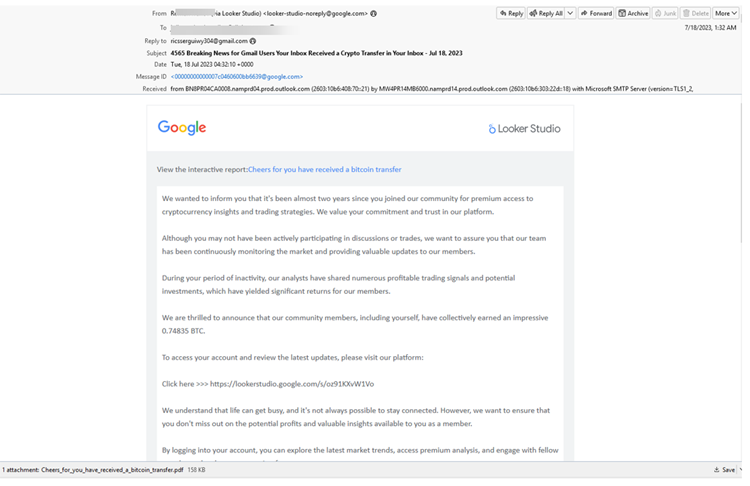
When you click, you’ll be redirected to this page. Again, it’s a legitimate Google Looker page.
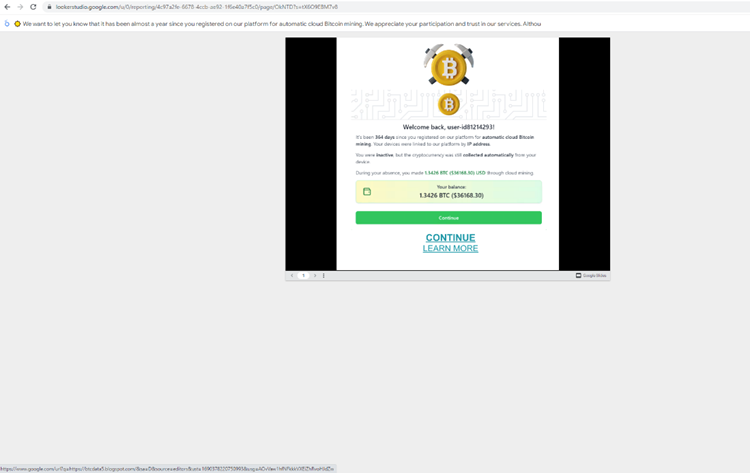
Here, the hackers have hosted a Google Slideshow, saying how you can claim more Bitcoin.
From there, it goes to a login page that is designed to steal your credentials.
But first, they give you even more urgency.
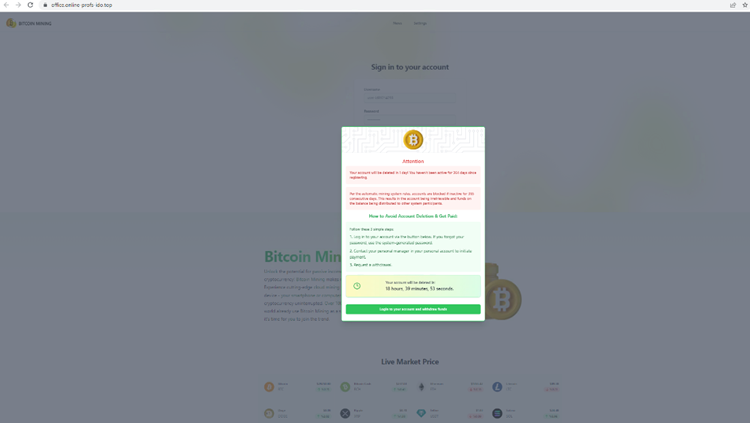
In order to save your account, you have to login immediately.
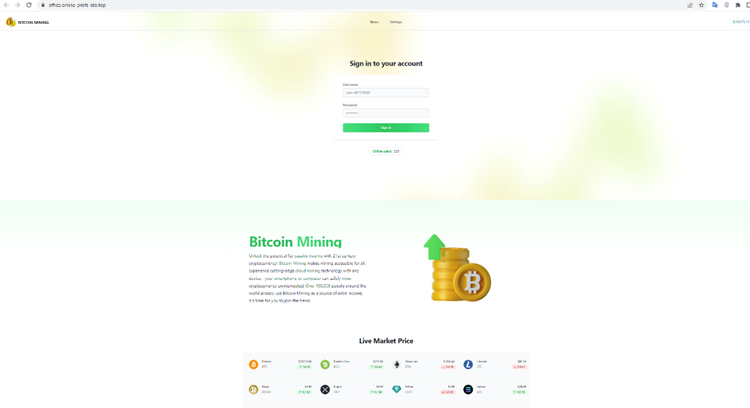
Then, of course, your credentials are stolen.
Here’s another example:
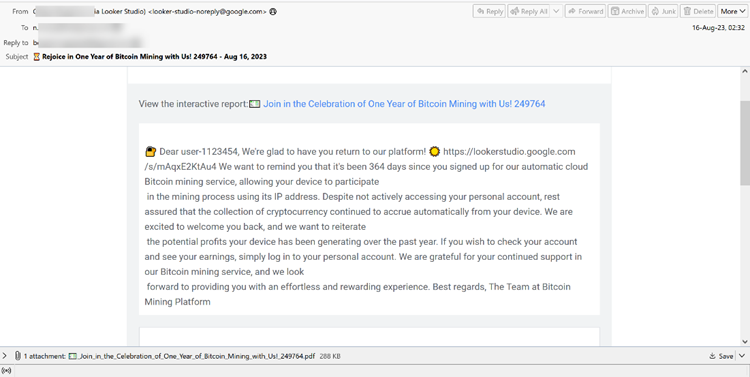
This is a similar example, hoping to get the user to click on the report and allow the user to give access to their IP address to mine Bitcoin. This one has a slight difference, in that there’s a malicious PDF attached at the bottom. This malicious PDF is actually a Trojan:
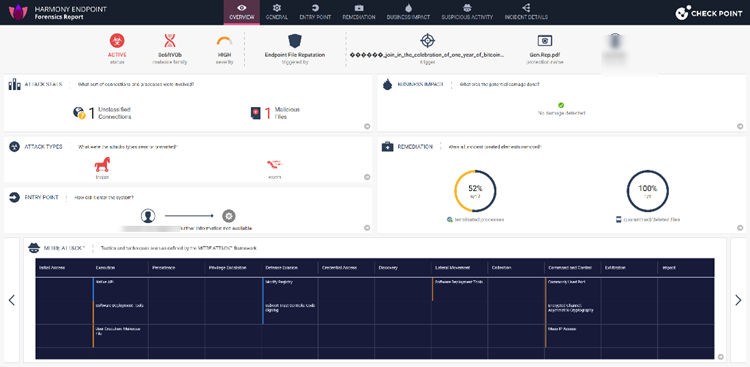
The clever part here is that hackers are using Google Looker to get their malicious PDF into the inbox. Because Google is a trusted service, it often soars right into the inbox, malicious PDF or not.
Techniques
In the backend, you can see the signatures that Google uses to legitimize this page.
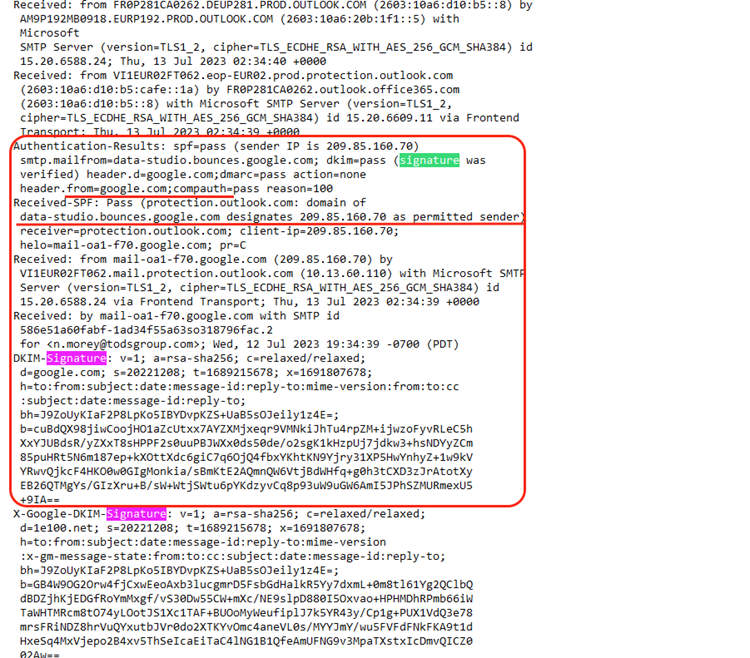
Let’s break this down a little bit. Sender Policy Framework, or SPF, is an email authentication method that is designed to prevent email spoofing by specifying which IP addresses or servers are authorized to send emails for a particular domain.
In this case, the SPF check has passed (spf=pass) because the sender’s IP address (209.85.160.70) is listed as an authorized sender for this domain: data-studio.bounces.google.com
Then, there’s DomainKeys Identified Mail, or DKIM. It’s another email authentication tool that uses cryptographic signatures to verify that the email’s content has not been altered during transit, and that it actually comes from the domain it says it does. In this case, the DKIM signature has passed (dkim=pass) and was verified for the domain google.com
Next is Domain-based Message Authentication, Reporting, and Conformance, or DMARC. DMARC is a policy framework that builds on both SPF and DKIM to further enhance email authentication. It allows domain owners to specify what actions should be taken for any emails that fail SPF or DKIM. In this particular case, the DMARC check has passed (dmarc=pass) for the domain google.com, and the action specified is none. That means that no specific action is taken for failed emails.
This is a long way of saying that hackers are leveraging Google’s authority. An email security service will look at all these factors and have a good deal of confidence that it is not a phishing email, and that it comes from Google. And it does! Because the attack is nested so deep, all the standard checks will pass with flying colors.
Now, this does require cooperation on the part of the user, to go through all the links and enter the required information. Not every user will do that. But as we say often, it just takes one successful attack.
Check Point researchers reached out to Google to inform them of this campaign on August 22nd.
Best Practices: Guidance and Recommendations
To guard against these attacks, security professionals can do the following:
- Adopt AI-powered technology capable of analyzing and identifying numerous phishing indicators to proactively thwart complex attacks.
- Embrace a comprehensive security solution that includes document and file scanning capabilities
- Deploy a robust URL protection system that conducts thorough scans and emulates webpages for enhanced security
Check Point Customers remain protected against the threats described on this blog while using Harmony Cloud Email & Collaboration Security.
Harmony Email & Collaboration provides complete protection for Microsoft 365, Google Workspace and all your collaboration and file-sharing apps. Email & Collaboration is designed specifically for cloud email environments and is the ONLY solution that prevents, not just detects or responds to, threats from entering the inbox






