We’ve been writing extensively about BEC 3.0 attacks.
BEC 3.0 attacks refer to the use of legitimate sites being leveraged for phishing. For example, sending an invoice via PayPal, but the invoice is not legitimate. It works since the email comes directly from the site. That means it will pass all sender reputation checks. Natural Language Processing checks can be difficult, too.
We’re seeing a lot of these come from Google’s suite of tools. Whether it’s Google Docs or Collections, Ads or Groups, all of these free services are being exploited to send out phishing campaigns.
Google’s services aren’t exploitable, and an army of hackers hasn’t suddenly taken over Google. Rather, hackers are using Google as a springboard to embed links that might otherwise get picked up by security services.
In this attack brief, Harmony Email researchers will discuss how hackers are using Google’s services to send phishing links.
Attack
In this attack, hackers are utilizing Google pages to send links to fake cryptocurrency sites.
- Vector: Email
- Type: Credential Harvesting
- Techniques: Social Engineering, BEC 3.0
- Target: Any end-user
Email Example
In this attack, threat actors are creating Google Forms. Google Forms is a versatile tool, where anyone can send forms to recipients. The use cases are endless--the forms can be a quiz for students, it can be a place to collect feedback, or just a centralized location for sign-ups. Within this form, hackers are embedding a malicious link. To get the user to act, they send a link to the form. The description in the email notes how the recipient has signed up for a Bitcoin account but hasn’t logged in in a while. To get access to the account and balance. The email links to a Google Form, as seen below.
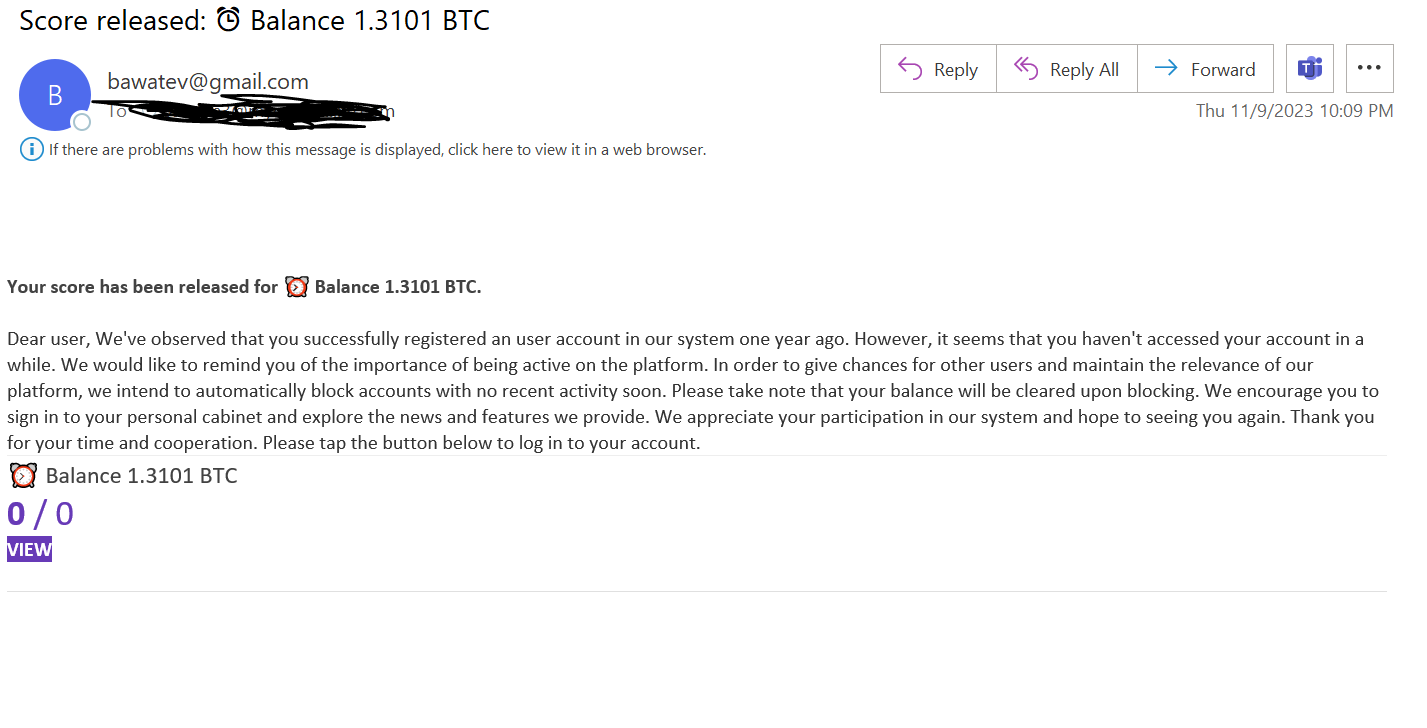
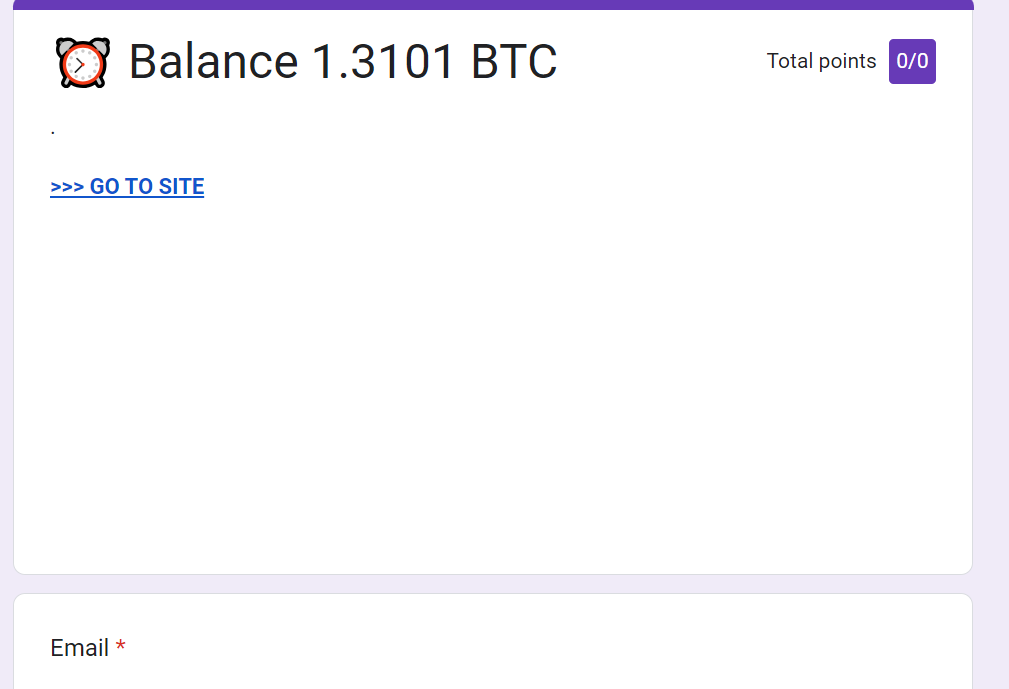
Clicking on “go to site” redirects you to a malicious link.
Techniques
Google is a safe service. It has not been exploited. However, hackers are using its services as a springboard to launch their attacks.
By starting the phishing trail with Google, a few things are happening. One, security services will think the email is clean. And that’s because it is clean.
The end-user will also be more likely to click on a link from Google since it’s something they likely do all the time without issue.
The end-user indeed has to give up their information, and that’s not a guarantee. That's the case for every phishing attack. But because it’s on a Google site, users are going to give it more credence.
These attacks are happening on Google and similar sites because signing up for an account is free. It’s easy to do. It doesn’t require a lot of effort or specialized knowledge.
It takes advantage of our trust in solutions like Google to get us to do something we wouldn’t normally do.
It’s not just a veneer of legitimacy. It’s a legitimate email with one thing off about it. But that one thing can cause a ton of damage.
Best Practices: Guidance and Recommendations
To guard against these attacks, security professionals can do the following:
- Implement security that uses AI to look at multiple indicators of phishing
- Implement full-suite security that can scan documents and files
- Implement robust URL protection that scans and emulates webpages





