We’ve talked a lot about how hackers utilize legitimate services to reach inboxes.
Many of these campaigns have focused on Google tools. Why? For one, Google is free and easy to use.
For another, Google has a lot of tools. From Docs to Sheets, Gmail to Forms, there are countless ways to utilize Google’s services.
That’s great for users. It also makes things easier for hackers.
With all the available tools at their disposal, hackers are able to send legitimate messages from these tools, directly to user inboxes, with malicious content embedded within.
In this attack brief, Check Point Harmony Email researchers will discuss how hackers are using Google Groups to send spoofed McAfee emails. compromised accounts to switch banking information.
Attack
In this attack, hackers are utilizing Google Groups to send out emails pretending to come from McAfee.
- Vector: Email
- Type: Credential Harvesting
- Techniques: Social Engineering, BEC 3.0
- Target: Any end-user
Email Example
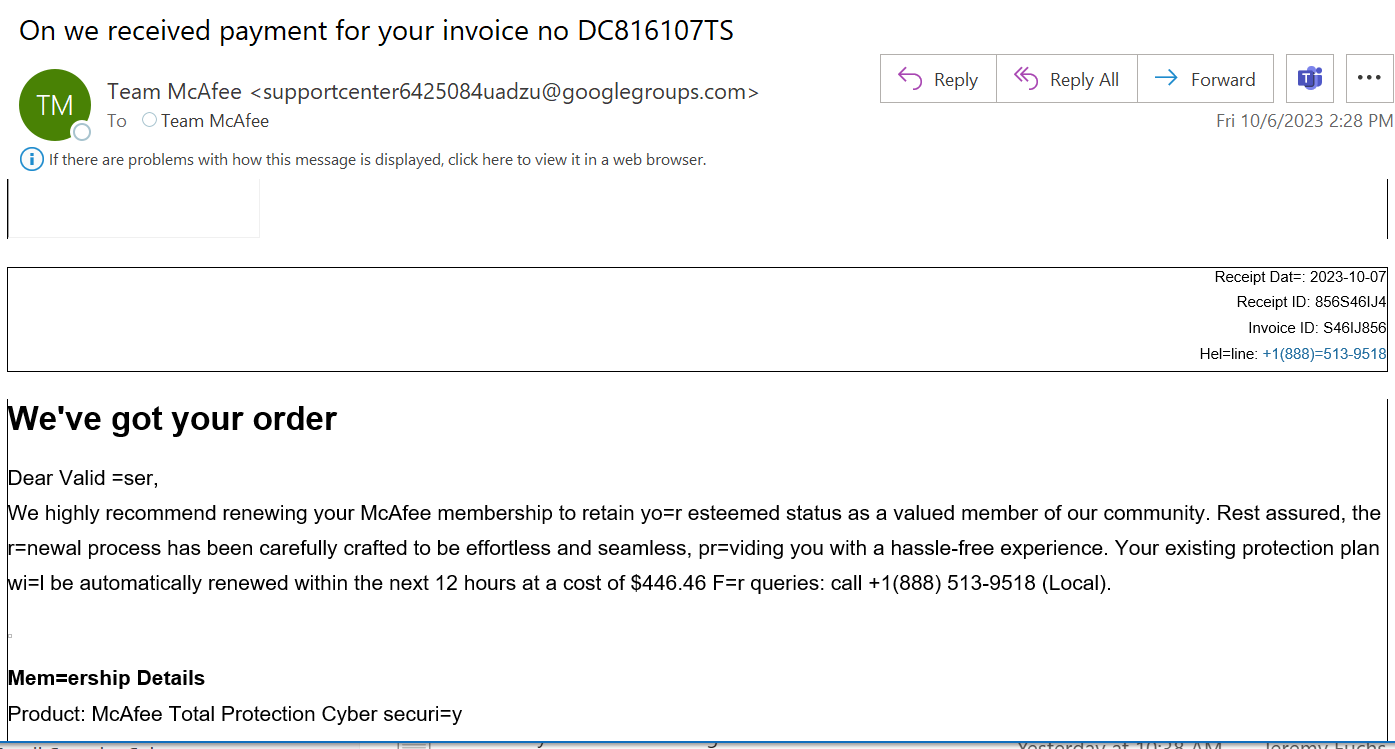
At Harmony Email & Collaboration, we analyze a lot of malicious emails. One thing is clear: some are more convincing than others.
The above email? Not the most convincing.
But to us, sometimes the methodology used is more important than how successful the hacker is at deploying it.
This email is riddled with errors, inconsistencies and a lot of equal signs.
But the method behind it is interesting.
By utilizing Google Groups, this message is more likely to get into the inbox.
Google Groups is a discussion forum and can be used to set up mailing lists and email lists.
This email is sent from Google Groups, and thus a Google domain.
When email security solutions see a Google domain, they are liable to trust it.
And security administrators can’t block Google, since it’s used for everyday work.
That’s what makes these tricky.
Techniques
These emails that come from legitimate sources tend to want to get you to go to an illegitimate source.
So the attack may start in Google, but the attack will lead you to a fake website that eventually steals your credentials.
Because the links are embedded deep within, many email security solutions aren’t going to follow the page to its intended destination.
That’s where something like browser security can come into play. For example, when someone tries to enter their corporate Microsoft or Gmail credentials on a site that’s not the actual login page, but instead a fake, browser security can notice that and block it. So essentially, even if an employee does fall victim to these emails, the browser security is there to help.
This is the layered security that’s vital to keeping organizations secure. And it allows for organizations to better protect against legitimate attacks that often end up being illegitimate.
Best Practices: Guidance and Recommendations
To guard against these attacks, security professionals can do the following:
- Adopt AI-powered technology capable of analyzing and identifying numerous phishing indicators to proactively thwart complex attacks.
- Embrace a comprehensive security solution that includes document and file-scanning capabilities
- Deploy a robust URL protection system that conducts thorough scans and emulates webpages for enhanced security






