Mail Exchange records—or MX Records—is a public way of notating the mail server responsible for receiving and sending messages. Think of it like a public address, similar to how in a vast network of roads, emails are vehicles traveling to their destinations, guided by a map known as MX Records.
We’ve discussed MX Records in the context of secure gateways. When deploying a Secure Email Gateway, you need to change the MX record to that of the gateway, essentially updating this "map" to reroute mail for extra screening. This information is publicly available on sites like MXToolbox.
Depending on the company’s configuration, the MX record can point to a SEG or it can show the default MX record for the email service they’re using. Check Point uses Microsoft 365 for email, so it appears like this:
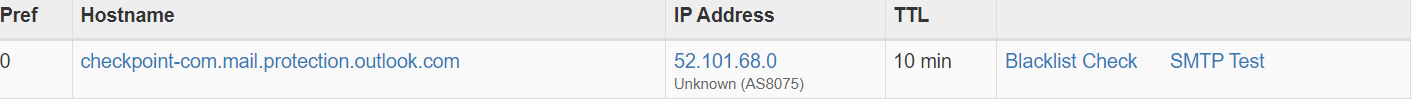
Prior to the acquisition, Harmony Email, previously Avanan used Gmail, so it would look like this:

This is public information. And we’ve noted the concerns about hackers using this information, particularly to target attacks at organizations with gateways. Now, Check Point Harmony Email researchers believe we’re seeing hackers using this information to target attacks specifically aimed at companies that use Google.
The Specific Attack
In the specific attack mentioned below, the first step the bad actor took was to route their invoice-based attack through a dummy Microsoft 365 workspace.
In over 100 examples of the attack, Harmony Email researchers saw that Microsoft rated this attack as harmless spam. When it went to Google after leaving Microsoft, however, it was seen as clean by Google. Neither rated as spam or phishing.
Email Example
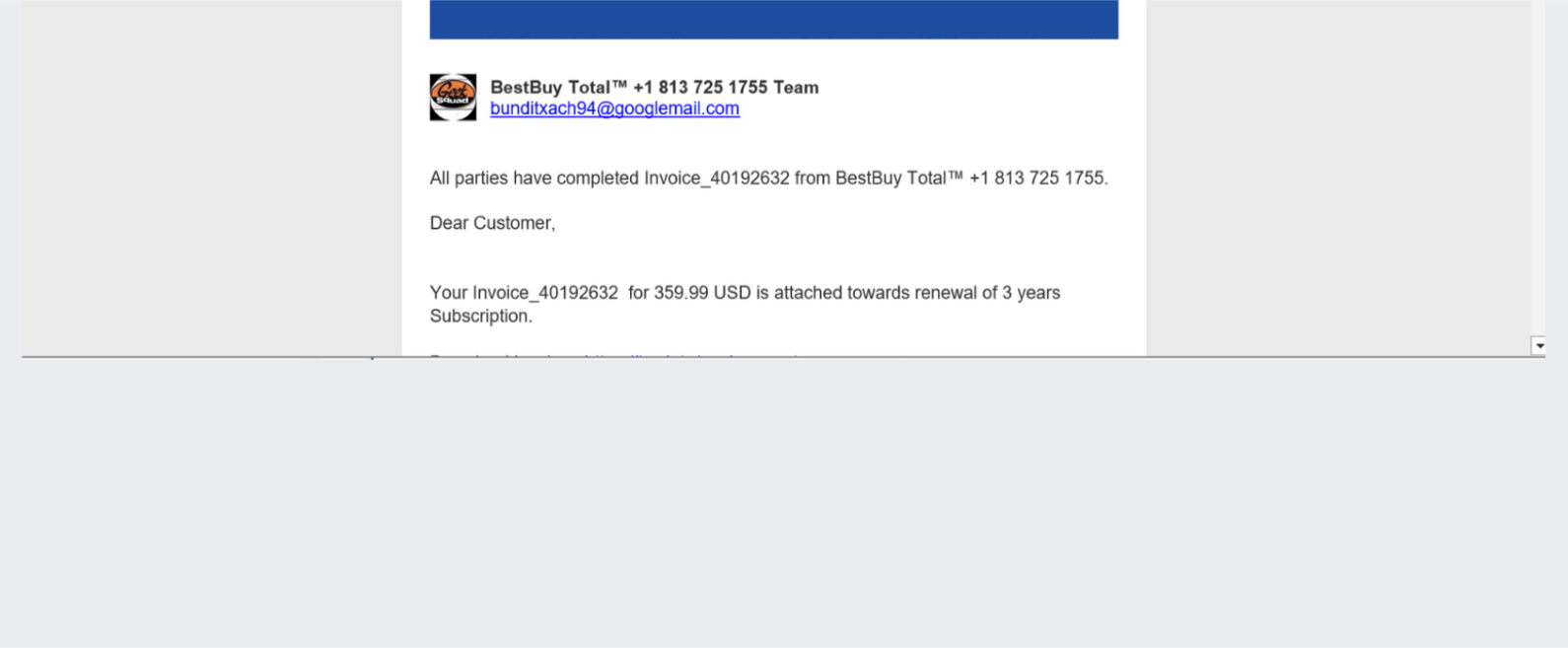
The email starts as a fake invoice. Harmony Email analysts noticed that it was “marked as spam by O365”. Given that this is a Google environment being attacked, it seemed suspicious that HEC saw the markers from a Microsoft environment during the email scans.
Upon further inspection, we noticed that the original recipient of the message is a dummy email ID with a domain ending in an onmicrosoft.com address. After the attack hits that inbox, Microsoft marks it as spam and it’s then sent to our intended victim’s Gmail environment. What the threat actors are doing is routing the email through a bogus M365 tenant that has an auto forward or BCC forward to the organization. Even though Microsoft noted this as spam, it was still auto-forwarded and marked clean by Gmail.
Harmony Email & Collaboration researchers reached out to Microsoft and Google. Google noted that “this is not a Gmail issue, it’s an upstream DKIM-Replay/Address Map attack. We’ve seen this attack before, including instances like this one where upstream authentication issues were capitalized on. Fortunately, our anomaly detection and AI-based protections caught the vast majority of this malicious activity.”
Techniques
The attackers here have specifically targeted Gmail customers. Instead of sending emails directly to the Gmail tenant, they route the message through Microsoft first. This attack does a number of interesting things. The attacker knew that this organization used Gmail—and as we mentioned, can easily find that using MXLookup. They can then target the attack accordingly. In this case, the bad actor’s experience dictated that routing his attacks through a dummy M365 environment would increase the chances of his attack bypassing the security of his targeted environment. He was correct, as this campaign was marked clean over 100 times by Google.
Understanding the transport hops of an email is critical. Going deep into transport data to pick up security results that previous hops reported, regardless of your mail tenant, provides additional insight into detections.
Google noted that “as an additional defense, we are leading the charge for the entire email ecosystem to follow best authentication practices that will help thwart this class of attacks. In this instance, implementing both of these requirements would have prevented this attack:
- Set up SPF and DKIM email authentication for your domain
- For direct mail, the domain in the sender’s From: header must be aligned with either the SPF domain or the DKIM domain. This is required to pass DMARC alignment.”
Best Practices: Guidance and Recommendations
To guard against these attacks, security professionals can do the following:
- Implement security that uses AI to look at multiple indicators of phishing
- Implement security that doesn’t show up via MX Lookup
- Implement security that understands all the transport hops to see the full context of the email
Conclusion: A Call to Arms in the Digital Age
This tale of digital cunning underscores the ongoing battle in cyberspace, where attackers and defenders constantly evolve their strategies. For everyday email users, it's a reminder of the invisible wars waged in the background of our daily communications, highlighting the importance of advanced security measures and vigilance in the digital era.






