UPDATE: May 12, 2020
Microsoft made news earlier this week by announcing that they are rolling out a feature that can block reply-all email storms.
Just a friendly reminder that Avanan has had this feature since 2018.
SEGs like Proofpoint and Mimecast cannot solve this problem. Microsoft can take months, or even years, to fix something that we figured out a long time ago.
It's a good time to learn about what else we can do better than legacy email protection.
Last week, Maria Peterson, a government employee in Utah, sent what she thought was an email inviting her colleagues to the annual holiday potluck. Instead, she accidentally invited every government employee in the entire state. What followed was a reply-all email storm that ensnared the entire state government in a seemingly endless chain of messages.
So this is happening right now. It’s Replyall-gate 2018. Adventures in state government. #ReplyAll Actually don’t reply all. pic.twitter.com/8loT09CM4s
— Joe Dougherty (@PIO_Joe) December 7, 2018
A brief history of reply-all email storms
The first known reply-all email storm struck in 1997, when a Microsoft employee asked to be removed from a list irrelevant to them. The aftermath was 15 million emails. Two decades later, humans simply can’t resist the allure of the spotlight Reply All provides—especially when social media commentary is added into the mix. It’s no wonder that email storms have metastasized into a global phenomenon capable of briefly derailing entities like ESPN, NYU, and the New York TImes.
The existing body of literature on reply-all email storms covers what happened, what the responses were, and how to avoid prolonging the issue. But I’d like to focus solely on the IT side of the equation. The IT teams are the ones responsible for cleaning up the mess that these email storms leave in their wake.
But before that, we need to understand the factors contributing to the recurring instances of these reply-all email storms.
The truth about reply-all email storms
We have little control over our email, even though it might seem like we do.
Reply-all email storms show that you don’t have to be an admin to wield a lot of power in your company’s email. Any employee with the ability to send to a listserv can trigger a torrent of unwanted and eventually redundant messages, empowering every recipient with the same visibility and voice.
At the same time, reply-all email storms reveal that lack of control over your email is perhaps greater. There is virtually nothing you can do to stop the messages from cascading into your inbox, aside from muting or simply ignoring the messages.
Training doesn’t stop the problem.
The New York Times reported that that Maria Peterson wouldn’t face any punishment for initiating the 22,000 person chain, but will undergo additional email training to avoid incidents like this in the future. With or without the training, it’s likely that the embarrassment from the fallout has taught her to be more thoughtful about what she sends to whom.
Like phishing, it seems that no amount of employee training or breaking news about reply-all email storms reduce their frequency. Truthfully, the only thing employees can be trained to do in this situation is mute the thread in Gmail, or hit “ignore” in Outlook.
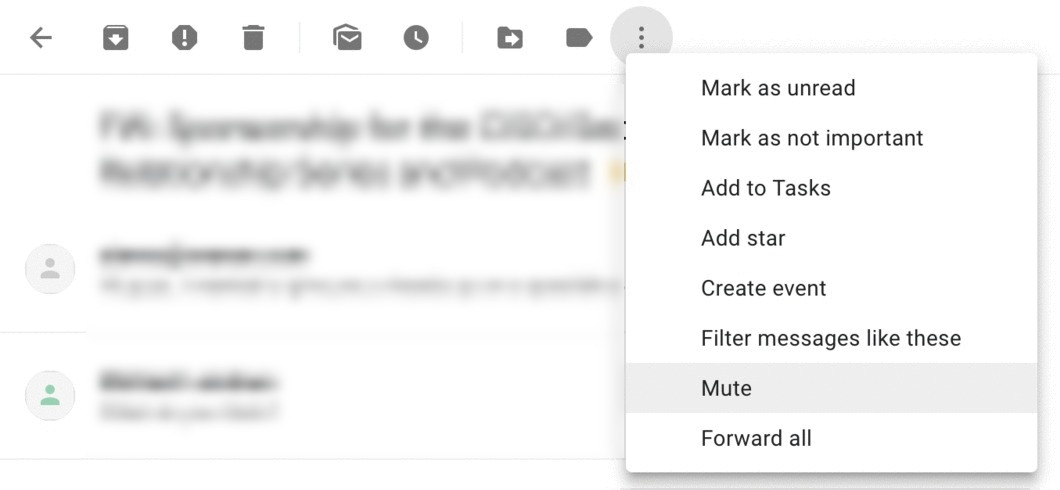
Train employees to mute a reply-all email storm, shown above.
Fortunately, in Maria’s case, the email subject matter was innocuous. No critical information was indiscriminately blasted to all government officials in Utah. But what if Maria had listed the address of the event, the code to enter the building, or even worse, the security code for the company card that would be used to purchase goods for the potluck? This is where the intersection between reply-all email storms, information security, and IT teams becomes a topic worthy of discussion.
Current fixes for reply-all email storms are labor-intensive for the IT team.
Reply-all email storms drain the security team who must scramble to restore order to the company’s email environment.
In the past, when email was in the data center, a reply-all event like potluck-gate would have generated loads of traffic and broken email servers, just like a DDoS attack. To fix this, IT would have to log in, delete the messages from the database, shut down the server, and write a script for new inbound emails.
Now that email is in the cloud, the slightly less labor-intensive solution is to write Powershell scripts that find these messages and quarantine them. Still, this can be a grueling task with a lot of overhead.
More resilient than an on-premises server, the cloud won’t break under the weight of the traffic generated by your average reply-all email storm. And unlike the good ‘ol days of the data center, IT doesn’t own the email server, leaving them without any native tools to fix the problem.
How to stop the reply-all email chain storm once and for all
Last year, we had a front-row seat to this travesty of email etiquette. One of our customers, a major US city with hundreds of thousands of accounts, suffered a reply-all email storm when a politician used a listserv of 5,000 government employees to share his positions on key issues and campaigns. The reply-alls began flooding because of the email's polarizing subject matter, and hostility among employees was brewing. Using Avanan, the admin ended the email storm with just a few clicks.
It is worth noting that every message in a reply-all email storm is considered legitimate by the email provider since it contains no malicious content like malware or viruses. Because of this, the vast majority of email security products cannot bring the madness of a reply-all email storm to an abrupt halt. Except for us, of course.
Avanan's Search and Destroy feature ends reply-all email storms and quarantines threats from compromised accounts.
Avanan’s Search and Destroy feature can annihilate a reply-all email storm in seconds. Search for the initial sender and subject of the email that started the reply-all email storm, and create a policy to move, delete, or edit all emails in the email chain. Voila! Now you know how to stop reply-all email chains. Peace has been restored to every inbox.