Scammers continually utilize and spoof file-sharing services to launch attacks. We've seen this recently with the We Shouldn't Transfer Attack, the Flipping Out Attack and so much more.
That's the case with a new attack that bypassed ATP. Doc Express is an e-Doc service that's used to send documents back and forth.
In this case, attackers utilized Doc Express (as well as SharePoint and Adobe) to launch the attack. They send an email that claims to have documents, but they are in fact malicious. Here's what the email looks like: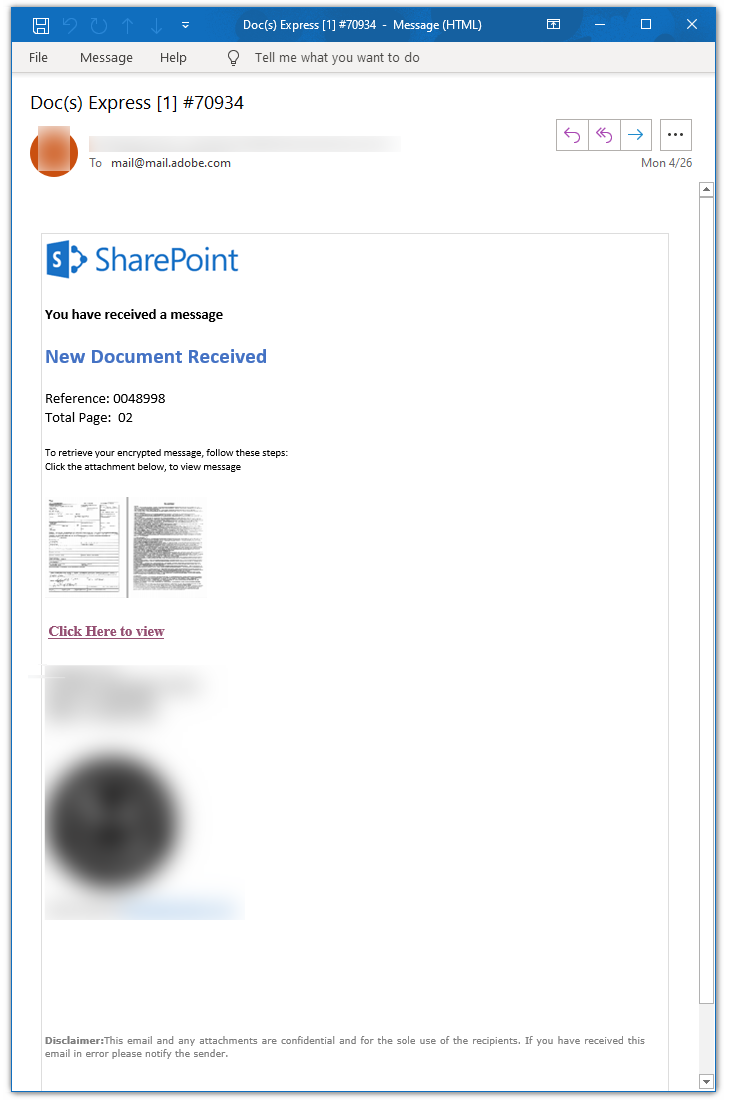
The sender address is an address that the end-user has had previous interactions with. Attackers are either compromising these domains or spoofing the sender information to display the email as what looks like a trusted domain.
Further, these attackers are sending the email to "mail@mail.adobe.com" and sending it to the real recipients as BCC. This is a common trick to try and get past poorly tuned security scanners that just look at the "to" field.
Avanan was able to block this attack with SPF checks.







