Earlier this month, Verizon released their 10th annual Data Breach Investigations Report. The 76-page report covers the data breach trends across all industries—from finance and healthcare, to manufacturing and education.
Although each sector had notable differences, mainly in the intent of the malicious actors, there were clear trends that reinforce what we have seen since we created our cloud security platform: while data leak prevention is important, the greatest security risk to an organization is their email and the access it can provide.
Malware
According to the report, over half of data breaches were a result of malware that made its way into the organization.
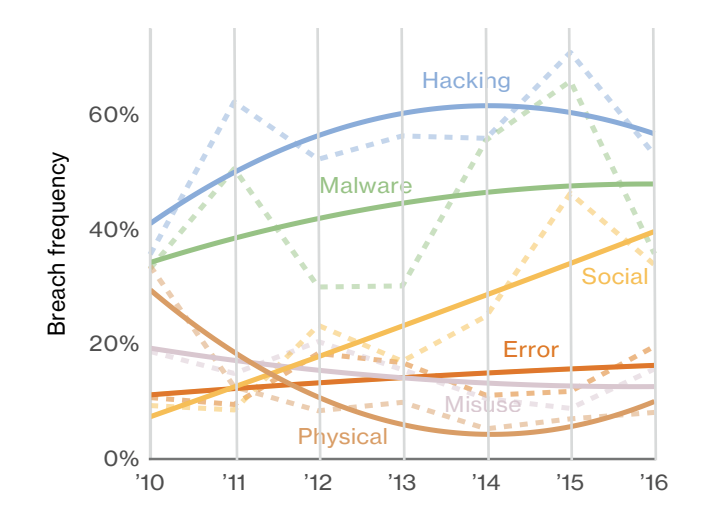
Additionally, malware looks to be on the rise as the primary cause of data breach. Hacking appears to be on the decline. It won’t be too long until malware is the number one cause of data breach.
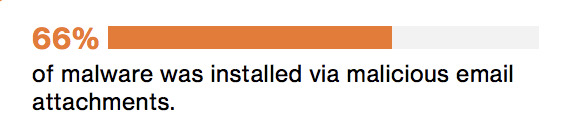
But how did the malware get there? The study took a deeper look at the source of each data breach and found that 2 out of 3 malware related breaches were perpetrated via email attachments.
In fact, when looking at total amount of malware, even malware that did not lead to an incident and where it came from, the number climbed much higher. Over 93% of malware was email based from this count, dwarfing other vectors.
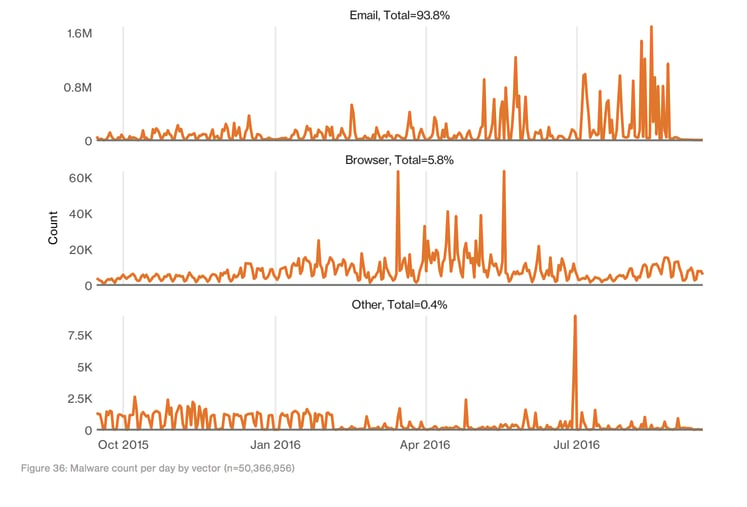
As the popularity of email attacks has grown, email security providers are struggling to keep up. This can be seen with our recent posts about the gaps in Microsoft Advanced Threat Protection and MTA based email security, such as Proofpoint and Mimecast.
The human vulnerability that makes malware attacks popular and successful will never go away. 95% of phishing attacks that led to a breach were followed by some form of software installation.
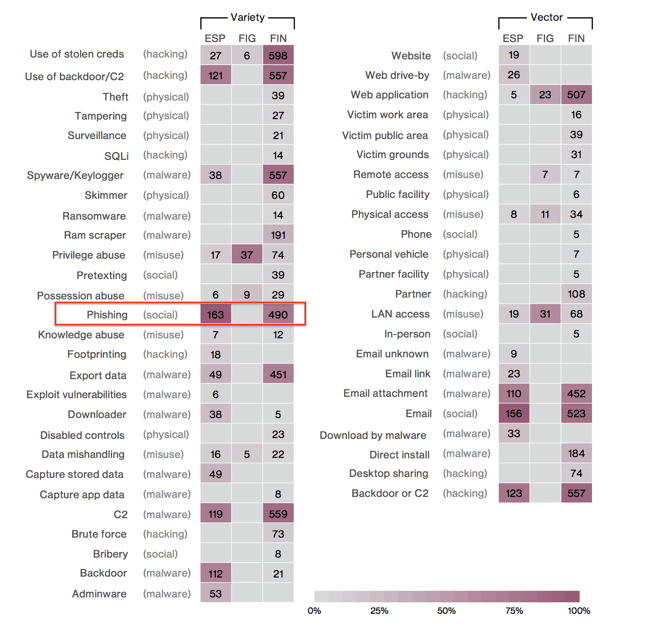
Phishing
The report looks at phishing from an angle that we do not often consider. We know phishing attacks are prevalent, but what are the phishing attacks after? What is actually at risk?
As can be seen on the chart below, the majority of phishing attacks fall in the “financial (FIN)” category, meaning the attackers hope for some monetary gain. Another sizable portion, though only about ⅓ the size of the financial group, are motivated by “espionage or state-affiliated (ESP)” reasons. Phishing understandably appears to not be used by the “fun, ideology or grudge (FIG)” motivated grouping, which are colloquially known as hacktivists.
FIG = Fun, Ideology, Grudge motives OR activist group threat actors
ESP = Espionage motive OR state-affiliated OR nation-state actors
FIN = Financial motivation OR organized criminal group actors
Attack Vectors by Industry and Variety (click to enlarge)
Now that we see that money is the prime motivator for most phishing attacks, we can look at why phishing is such a popular method.
The chart below, shows how likely an employee is to click on a phishing link or attachment. The range is not massive, but it is alarming to see that in half of the industries surveyed, more than 1 in every 10 phishing campaigns garnered a click.
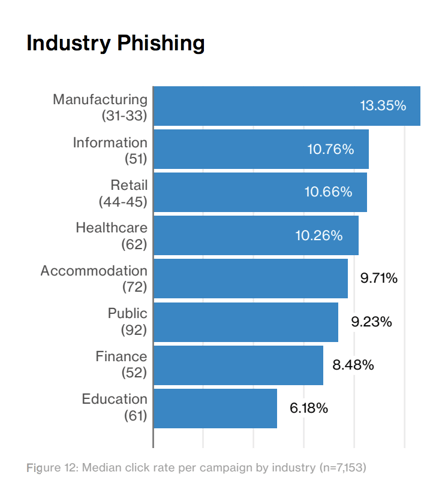
Who is clicking on phishing links? Click rate by industry.
The immediate response to these numbers may be to blame the victim and consider it an unavoidable cost of human error. We don’t believe that.
It is up to security providers, not humans, to prevent phishing attacks. As it does every year, the report concludes that organizations ought to invest more in human education. While this is a good idea, we can see that in the finance industry—where security awareness is considered an important part of employee training—the odds an employee will click on a malicious email are still greater than 1 in 20.
According to the report,
“7.3% of users across multiple data contributors were successfully phished—whether via a link or an opened attachment … 15% of all unique users who fell victim once, also took the bait a second time. 3% of all unique users clicked more than twice…”
The risks are too high to be left to “better training.” As one CISO described it, “Employee training is like a signature that gets updated once a year.”
Over the last few years email security providers have worked hard to identify and block phishing attacks, but we have seen that the latest methods now include evasion techniques designed to fool automated algorithms. In fact, many of them are specifically designed to evade the built-in anti-spam and anti-phishing tools offered by Office 365 and Google.
We’ve covered some of these in a number of recent posts including the recent Excel Phishing Attack that Bypasses Office 365 and the Office 365 Security Hack Using Google Redirect Vulnerability. There are many, many more.
Conclusion
Email is much more than just the primary method of business communication: it is the hackers’ main entry-point into your organization. It won’t matter how robust your network or datacenter security is if your employees can be compromised via email. Your email provider’s default security and end user training can only get you so far in protecting your assets.