Last week, news was made when it was revealed by Brian Krebs that there was a breach at the California State Controller's Office, which is an agency responsible for handling over $100 billion in public funds.
The attackers used their 24 hours of access to steal social security numbers and other sensitive information for scores of state workers, while also sending phishing messages to at least 9,000 contacts.
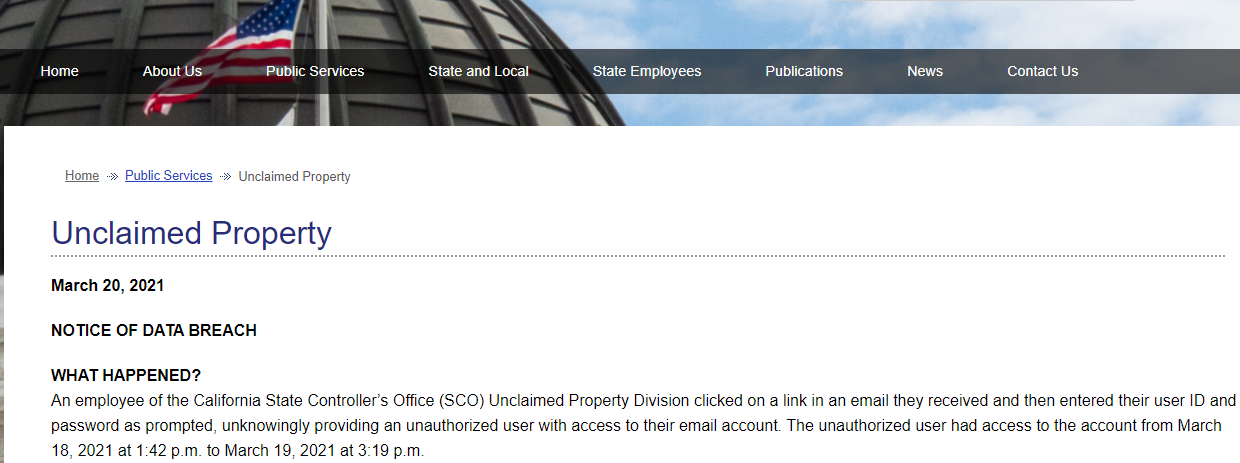
The Controller's Office put out a public message last week describing the incident:
The key line is: "An employee of the California State Controller's Office (SCO) Unclaimed Property Division clicked on a link in an email they received and then entered their user ID and password as prompted, unknowingly providing an unauthorized user with access to their email account."
Phishing links are designed to make harried employees click. It's why some 30% of phishing attacks are opened by end-users.
And it's why Avanan stresses the importance of inline, pre-delivery scanning, which is our patent. Avanan scans emails before they reach the inbox, meaning if it's malicious, it doesn't end up with the end-user.
Other API-based solutions work differently. The malicious email actually reaches the inbox. It's then retracted, in a time span ranging from 30 seconds to up to five minutes.
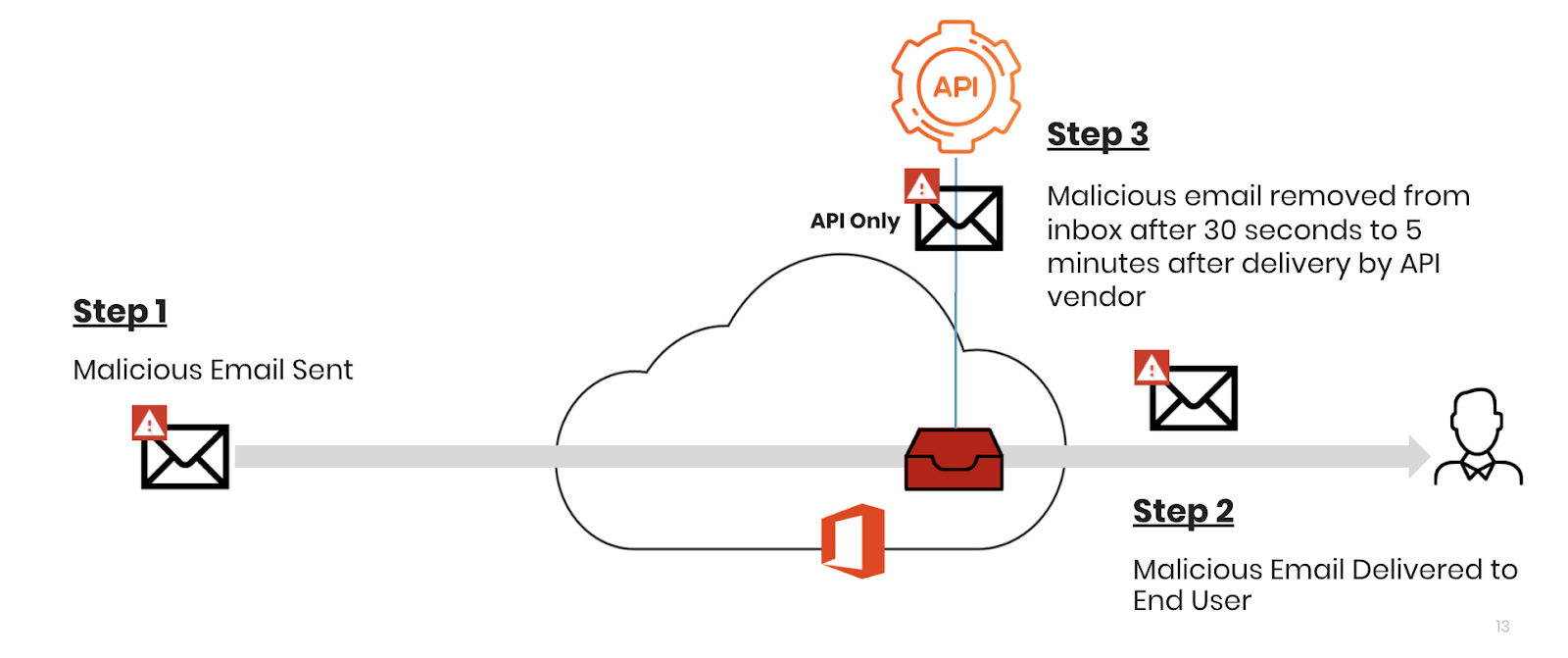
According to the Verizon DBIR, the average time it takes for an end-user to click on a phishing link is one minute and 40 seconds. Plus, in 93% of data breaches, the compromise occurred in a minute or less. That means, with other API solutions, there could be plenty of time for a user to click. See how it looks in this example:
We don't know what security provider the State Controller was using. But consider it a cautionary tale.
When there is phishing, there's a good chance that an employee will click and damage will be done.
Preventing phishing from reaching the inbox is the only way to guard against this.