Mark Ostrowski is Head of Engineering, US East, Check Point. He has 20 years’ experience in IT security and has helped design and support some of the largest security environments in the country. As regional director of engineering for the east coast at Check Point Software, Mark provides thought leadership for the IT security industry outlining the current threat landscape and helping organizations understand how they can pro-actively mitigate and manage risk.
In our first post of the three-part blog, we explored and predicted how in 2023 artificial intelligence will be the most talked about technology development. As I write this post, the headlines in media continue to lead with artificial intelligence implications and in fact, leaders in tech are meeting in the White House in DC.
Let us dive into Check Point ThreatCloud AI, the most preventative cyber security AI use case.
With the speed in which malware is evolving and the sprawl of the number of connected devices (IoT, mobile, 5G etc.) as well as the amount of data to process, all those together combine to make it impossible for human-created models to give comprehensive and real-time protection and prevention. This challenge is overcome by incorporating AI into a multi-layered intelligent system that can prevent these complex and sophisticated attacks.
Check Point’s Threat Cloud AI is a collaborative knowledge base that delivers real-time dynamic security intelligence to all of Check Point’s security solutions. ThreatCloud’s knowledge base is dynamically updated by a vast global network of sensors, attack information, and Check Point research-- just for starters. ThreatCloud is constantly leveraging AI and unique intelligence, which handles billions of requests every day. I talked about DATA being a core component of AI--below is an illustration of how much data is counted daily

There are other key components of any powerful AI system:
PEOPLE Check Point has 30 years of experience in securing the evolving threat landscape; this history has driven our leadership up and down the organization to set the strongest cyber security vision that aligns with challenges. This includes our research team and data scientists that collect and analyze global cyber-attack data stored to train, test, and improve AI models.
MATH ThreatCloud AI and the over 40 AI engines can provide the best prevention. Below are example model types in the knowledge base and examples of the engines themselves.
- Intelligence – Machine-generated signatures, Anonymizer models, reputation, external sources
- Static Analysis – Executables, applications, documents, code, emails, classification
- Dynamic Behavioral Analysis – Dynamic executables, documents, applications
- Correlation and Elimination Models – Machine-based incident correlation, signatures, accuracy
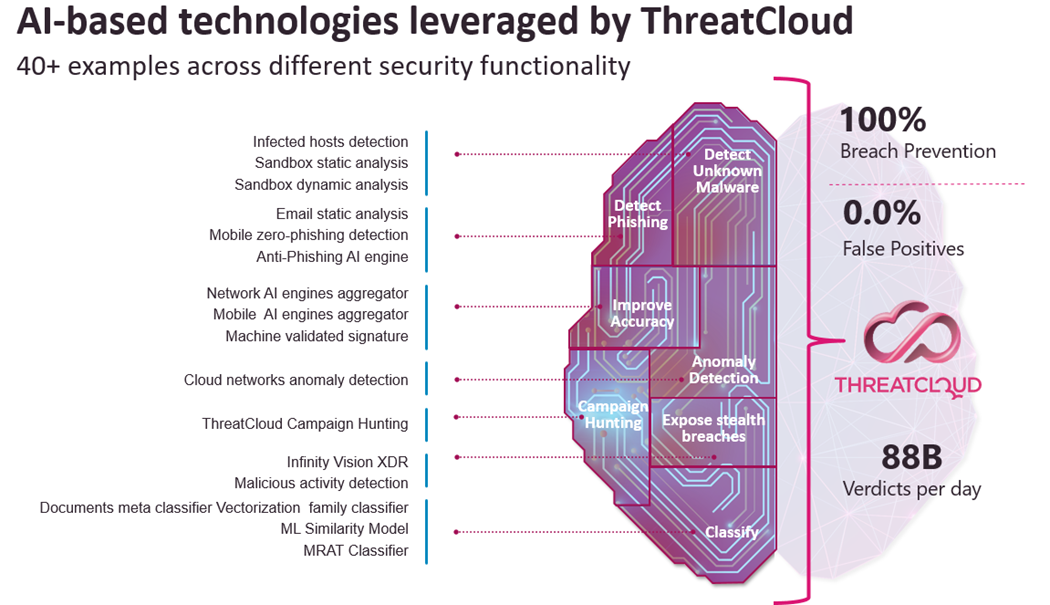
The effectiveness of Check Point’s ThreatCloud AI in preventing attacks is due to the vast amount of real-world data of threat and domain experts who develop, train and validate the models. Check Point has developed a proprietary labeling methodology that establishes a trustworthy ground truth. Additionally, a unique feature set, data enrichment, and integration of the algorithm approach result in the industry’s leading prevention rate.
The Check Point Infinity Architecture which is the industry’s full-consolidated cybersecurity architecture protects business and IT infrastructure again complex cyber-attacks across all networks, endpoint, cloud, email and mobile. The AI engines and completeness of data take a major role in the best security. The final post we will deep dive into is email security specifically, and how AI provides industry-leading email and collaboration security and malware prevention.





