Mark Ostrowski is Head of Engineering, US East, Check Point. He has 20 years’ experience in IT security and has helped design and support some of the largest security environments in the country. As regional director of engineering for the east coast at Check Point Software, Mark provides thought leadership for the IT security industry outlining the current threat landscape and helping organizations understand how they can pro-actively mitigate and manage risk.
Many are predicting that 2023 will be the year of artificial intelligence. The question is, who are the ‘many’? As a cyber-security evangelist at Check Point Software, am I part of the many? Or, did generative AI make this prediction of itself? I am only partially kidding as AI has dominated all narratives since ChatGPT was launched on November 30th last year. In reality, AI and Machine Learning (ML) have been a critical part of cyber security for years and have surrounded us in our everyday lives. In this first of three blog post, we'll explore the key ingredients to AI and how it surrounds us and works.
Below are six use cases where AI surrounds us:
- Automatic Speech Recognition (ASR) – Talking to digital assistants or telling your car to turn on the radio or send a message
- Image Recognition – How often have you used google images?
- Natural Language Processing (NLP) – ChatGPT anyone?
- Customer Relationship Management (CRM) – How often have you talked to a bot for customer service?
- Financial Fraud Detection – Getting a voicemail or text of suspicious activity?
- Commercial Activities – Any business application, social media apps as an example
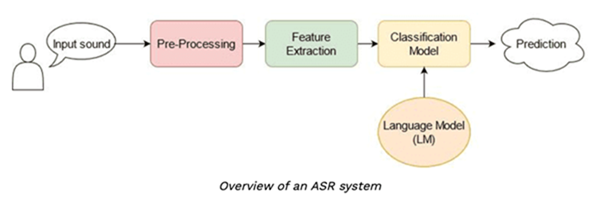
What do you need to build artificial intelligence?
- People – Build it
- Math – Algorithms
- Data – Lots of it
Artificial intelligence is the foundational starting point. AI is simply using computers to emulate humans and perform tasks. Machine learning is a subset of AI where math makes decisions based on what was learned. Deep Learning is a subset of machine learning that creates layers of math or algorithms to create a ‘neural network’. This neural network, which in context looks to mimic the animal brain, improves continuously and looks to solve complex problems.
Let’s jump to cyber-security. To achieve AI/ML representation in cyber intelligence we need to classify data and represent them to the computer. Extracting features (attributes) for each data item are used to train the ML system.
If you are classifying fruit you have color, weight, and shape as features. The math will dictate which ML classifiers are best used. As we build the training data we use labels to define the truth, which the math/algorithm will learn.
In the fruit example, as we collect samples we extract our features and the labels and build the ML algorithm. This output is a function that has the logic from the collection input. This function is called a model.
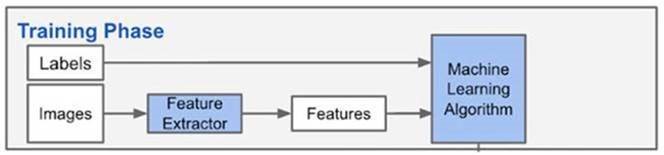
FUNCTION HAS BEEN CREATED
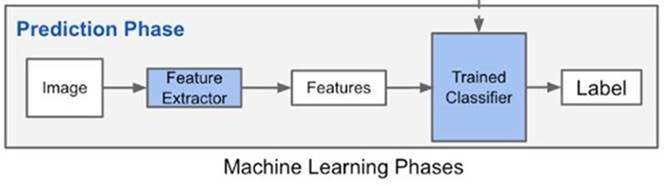
There are two main types of Machine Learning
Supervised – give the ML the data (labels) and desired output. This is to establish truth
Unsupervised – we don’t give labels and in cyber security we look for hidden structures or clusters-- for example in malware families, we look for anomalies
I hope that this post broke down AI to its simplest form while getting a bit technical. In our next post, we’ll explore how Check Point has innovated, employing over 40 AI-based engines to achieve the best cyber-security and providing customers with a qualitative advantage in preventing the most complex and dynamic attacks.





