When someone takes over an account via email, they usually do one of the following actions:
- Update bank account info email to payroll
- Hijack existing legitimate conversation related to an invoice and send the attacker’s bank info instead
- Create an inbox rule to hide future emails in a conversation so that the real user is unaware that anything happened
- Create a new payment request from a trusted account to a fake 3rd party service.
These are simple, yet potentially very damaging attacks.
Another one we see often is the bank signature change. This happens when a “new employee” tries to become the signatory on the bank account.
That would give them control to do just about anything.
In this attack brief, Harmony Email researchers will discuss how hackers are taking over email accounts and using it to try to become an authorized signer.
Attack
In this attack, hackers are taking over accounts and asking for signatory power on bank accounts.
- Vector: Email
- Type: Credential Harvesting, Account Takeover
- Techniques: Social Engineering
- Target: Any end-user
Email Example
The first step in this attack is taking over the account. As we’ve discussed, account takeovers can happen in a number of ways, from brute password access to much more complex methods.
Once taken over, the attacker can do a lot of things.
In this email, the attacker has taken over the account of someone in finance. They are notifying someone, likely in purchasing, that there’s a new finance manager on board.
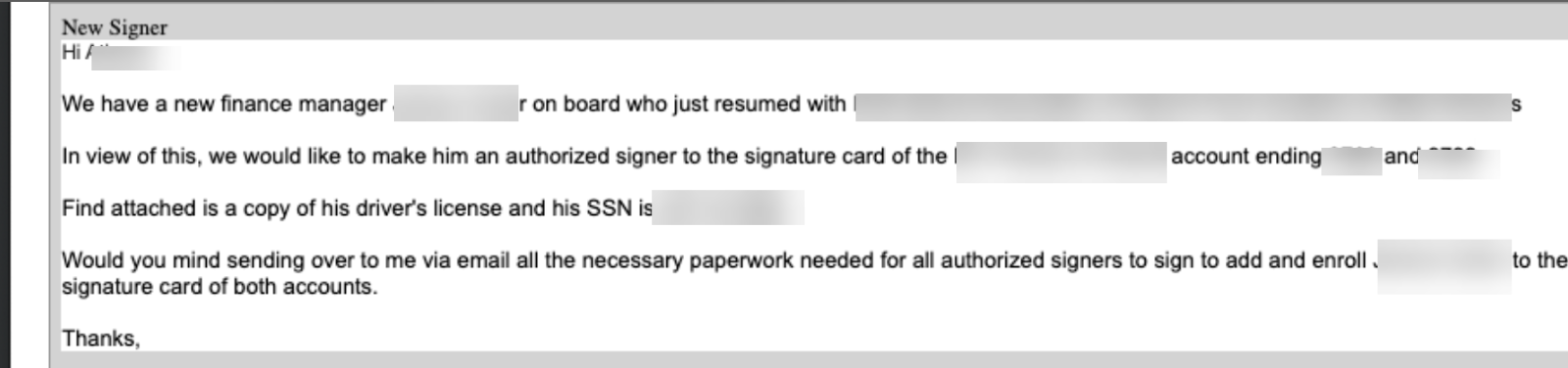
What they want to do is have this new “finance manager” become an authorized signer on a particular account. They are even giving over driver’s licenses and social security information to obtain this signatory power.
The level of detail and preparedness by the threat actor shows that this wasn’t just a spray-and-praypray attack. It was thought-out and coordinated.
Had this not been caught, the threat actor would have untold power and the ability to transfer funds almost indiscriminately to their personal account.
Techniques
Taking over accounts is a great way to launch BEC-style attacks.
Some are cleverer than others. This attack is pretty clever, because of the preparedness involved.
Wwhether the hacker makes it incredibly obvious or not, systems and processes need to be in place.
Gartner has noted the increasing intertwining between DLP and BEC. Adding what we call SmartBanners can help as well. These are customizable, but for example, might have a “suspected phishing” banner on it, and educates users that the email contains elements that may indicate phishing, such as tricking them into disclosing private or financial information.
Plus, our DLP tools can be set up to note that social security numbers or driver’s licenses have been included in an email and that this is a violation of policy.
Utilizing DLP to understand when sensitive data is being shared and ensuring that users know they are about to send out said sensitive information is a huge tool in the fight against BEC and account takeover.
Another key is processes. For example, if there was ever a legitimate need to change the signatory on a bank card, a process that could be in place would be something along the lines of going through official channels, not via email. When something then comes over email, it will immediately be suspicious.
Giving end-users and companies all the tools they need to be successful in the fight against BEC is key. That includes auto-blocking of compromised accounts and robust DLP tools, as well as defined processes and procedures that everyone knows.
Best Practices: Guidance and Recommendations
To guard against these attacks, security professionals can do the following:
- Implement email security that monitors for unusual behavior, such as Superman logins, insecure configurations and more
- Implement security that can automatically block account takeover attacks
- Implement security that uses AI, ML and NLP to understand the intent of a message and when phishing language might be used
- Implement security that utilizes DLP to prevent sensitive information from being shared mistakenly






