Introduction
In the world of SaaS, all a threat actor needs to take over an account is the email and password.
There are countless ways this can occur. People often aren’t as disciplined with their passwords as they might like to believe; lists get leaked. And there are plenty of ways skilled hackers can obtain this information.
Once in, they have the keys to the kingdom.
What we see a lot of is attempts to route money elsewhere. The hacker will insert themselves into an existing email chain, and ask for payment to be sent to a different bank account.
For the hacker, this is pretty easy money. All they have to do is sit back and wait for the funds to hit.
For the recipient, it depends on the company. Are there processes in place to update bank information? People and companies do change banks—does your procurement and purchasing departments account for these?
Hackers are counting on there being no procedures in place. And that the five seconds it takes to update banking information will be enough to route money into their account.
In this attack brief, Harmony Email researchers will discuss how hackers are taking over email accounts and using it to try and pilfer money—in this case, $76,000.
Attack
In this attack, hackers are taking over email accounts and using it to try and redirect $76,000 to their bank account.
- Vector: Email
- Type: Credential Harvesting, Account Takeover
- Techniques: Social Engineering
- Target: Any end-user
Email Example
In this attack, the first step is the hacker taking over an email account.
Once the attacker has taken over the email, you can see the strategy.
The hacker has inserted themselves into a relevant email. It doesn’t make sense to randomly pick an email and ask for banking information to be changed.
Instead, they hijacked a thread asking about a past due invoice.

They inserted new banking information and attached an invoice for $76,000.
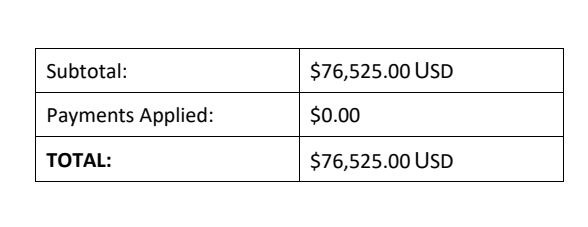
Had this not been caught, this would’ve been paid out, and there would be a number of unhappy people—the actual company waiting for the invoice, and the recipient’s company who paid out an invoice to the wrong person.
Techniques
When looking for compromised accounts, there are a number of potential tip-offs. Here’s some of the things our AI looks for:
- Superman" logins (Same user, across SaaS from remote GEOs in a short time)
- First seen in a new country
- First seen with this device
- Unusual number of used devices
- Suspicious Configurations like Forward-all-to-outside-email (Office 365 + Gmail)
- Suspicious emails like an unusual number of BCC in an email (compared to other emails in the user's history)
- Login outside a defined geography
- Multiple failed login
- Same machine with login by multiple people
- Same machine sending an email and trying to login (Some hackers use hacking tools on their PC to send out phishing emails and then login to O365 from the same IP)
- Session characteristics such as length, time-of-day, behavior (For example, sending emails without reading emails, to spread an attack)
- Existence of suspcious configuration changes (For example, a Gmail rule that deletes all incoming email to hide tracks of a hacker)
- Disabling MFA
- Unusual number of 'reset password' emails received by a user
- Email rules that hide incoming emails
- Email rules that leak data to outsiders
- Phishing emails originating from an internal user
- Suspicious activity that follows the reading of a suspicious email
- Tokens with access given to low-reputation applications
- And others... (Total of over 100 indicators)
When one or more of these things occur, it’s a good sign that someone has accessed the account fraudulently.
If your email security system can automatically block these accounts when this happens—like we can—you'll be in good shape.
There’s a few other things that might be beneficial. This is where DLP comes into play.
Consider the story of the City of San Francisco. We worked together to create a “break-the-glass" workflow for education and enforcement surrounding DLP. When users are properly encrypting and protecting data, the system rewards the end-user for following proper security practices. If, however, a busy employee attempts to send sensitive data outside the City—or, say, update banking information without following typical policy—then they are stopped and given notice, and asked, “Did you mean to do this?”
That’s why one of the most powerful tools in the fight against BEC and account takeover is DLP.
As Gartner has noted, “leading email security vendors are consolidating their service portfolio to include data loss prevention (DLP), user awareness training and BEC as attacks become more targeted and complex.”
Utilizing DLP to understand when sensitive data is being shared and ensuring that users know they are about to send out said sensitive information is a huge tool in the fight against BEC and account takeover.
Our DLP is super customizable, with categories around personal information, financial inforamtion, even intellectual property. This applies to both inbound and outbound email, and across SaaS apps.
Giving end-users and companies all the tools they need to be successful in the fight against BEC is key. That includes auto-blocking of compromised accounts and robust DLP tools.
Best Practices: Guidance and Recommendations
To guard against these attacks, security professionals can do the following:
- Implement email security that monitors for unusual behavior, such as Superman logins, insecure configurations and more
- Implement security that can automatically block account takeover attacks
- Implement security that uses AI, ML and NLP to understand the intent of a message and when phishing language might be used
- Implement security that utilizes DLP to prevent sensitive information from being shared mistakenly






