Account takeovers happen when an outside actor gains access to an email account. This can happen through a number of ways, from standard brute force to more complex ways in.
Regardless, once attackers have credentials to an email account, there’s a lot of things they can do.
One thing we see a lot of is what we call BEC 2.0, which refers to when someone compromises an employee or a partner and begins sending out emails from that legitimate email address.
Some examples of this are better than others, but because they come from what appears to be a “trusted” source, recipients are more likely to click on or otherwise engage with the email.
Lately, we’ve seen a rise in student email accounts being taken over and used to send out emails to otherwise unsuspecting recipients.
In this attack brief, Harmony Email researchers will discuss how hackers are taking over student email accounts and using it to send out phishing emails.
Attack
In this attack, hackers are taking over student email accounts and using it to send out phishing emails.
- Vector: Email
- Type: Credential Harvesting, Account Takeover
- Techniques: Social Engineering, BEC 2.0
- Target: Any end-user
Email Example
In this attack, a threat actor has taken over the account of a student at a large university in the Middle East.
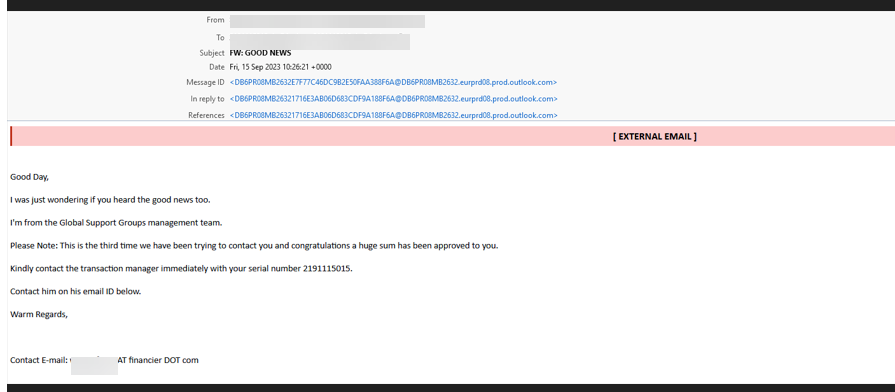
The attacker has taken over the account of a student and has sent an email to a large list. Sending emails to a large mailing list can be one way to evade detection by security services.
You’ll notice the email content itself is pretty typical of phishing emails. There's some urgency here--”this is the third time we have been trying to contact you”--and a big reward promised at the end-- “huge sum has been approved to you.” That should be standard tip-offs.
Another tip-off is the fact that there’s a separate contact email at the bottom, and it goes to a domain called fiancier.com. That's actually an email service that has been used by abusive accounts, though it’s also used for legitimate purposes. But it has nothing to do with the university.
And finally, any time there’s a subject line that’s “FW: GOOD NEWS” you probably want to stay away.
Techniques
Some phishing emails are really bad. Some are really convincing and effective.
This example is a good illustration of a bad phishing attack. There are multiple things that will alert the end-user that something is awry.
But in these Attack Briefs, we tend to focus on the technique. And here, the technique is representative of a popular and effective phishing tactic.
Taking over accounts of anyone—whether a corporate employee or a student—is an easy and effective way to begin sending out phishing emails.
That’s because the sender will always be legitimate. It’s even more effective when the email comes as a reply to an existing thread.
When someone takes over an account via email, they usually do one of the following actions:
- Update bank account info email to payroll
- Hijack existing legitimate conversation related to an invoice and send the attacker’s bank info instead
- Create an inbox rule to hide future emails in a conversation so that the real user is unaware that anything happened
- Create a new payment request from a trusted account to a fake 3rd party service.
In order to prevent these attacks, end-user education is key. But you also need proactive, preventative security, and there’s where our ability to automatically block compromised accounts come into play. We have a workflow that automatically disables users detected as compromised and terminates all active sessions. Admins are, of course, still alerted of this and then are able to reset the password and unblock the user manually—all from the dashboard. This is aided by our new AI engine that looks for compromised users. Instead of looking at single login parameters on their own (such as country, IP address, etc), the AI engine looks at and inspects all the parameters of login events to determine those that are done by malicious actors.
This list is dynamic and constantly growing, but involves things like the IP address, browser, browser version, device, VPN brand and much more. Login events detected by this new engine will flag their corresponding users as compromised (Critical Anomalies).
The amount of damage that can be done when a compromised account is vast. Getting to the root of the problem and stopping it before something happens is critical.
Best Practices: Guidance and Recommendations
To guard against these attacks, security professionals can do the following:
- Implement email security that monitors for unusual behavior, such as Superman logins, insecure configurations and more
- Implement security that can automatically block account takeover attacks
- Implement security that uses AI, ML and NLP to understand the intent of a message and when phishing language might be used






