In an account takeover (ATO) attack, an attacker gains unauthorized access to the credentials for a user’s online account. This access can then be used for identity theft, fraud, and to enable other cyberattacks, such as access to a user’s corporate credentials to login and plant ransomware within the corporate network.
It’s more than just taking over an account. There are broad concerns.
In one study, Javelin Research found that account takeover increased by a whopping 90% in 2021. These losses totaled $11.4 billion, making up nearly a quarter of all identity fraud losses in 2021.
In this attack brief, Check Point Harmony Email Researchers will discuss how this account takeover attack at a regional hotel in the Northeast happened, and what organizations can do to stop it.
Attack
In this attack, hackers are taking over email accounts and using them to try to re-direct invoice payments into their bank accounts.
- Vector: Email
- Type: Account Takeover
- Techniques: Social Engineering, Invoice Redirection
- Target: Any end-user
Email Example
At a regional hotel in the Northeast, invoices are constantly being fulfilled. But when an account gets taken over, things can go haywire. In this case, the account of someone in the finance department is taken over. Posing as this employee, the hacker reached out to a vendor asking about an invoice:
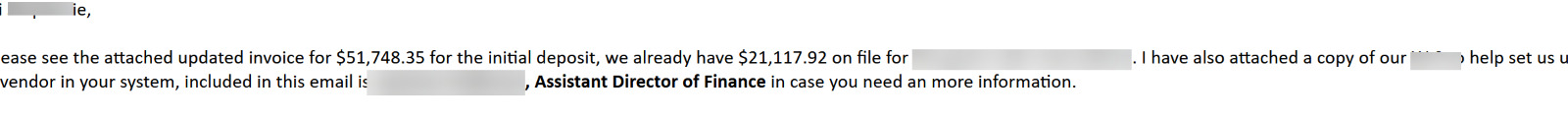
There’s a bunch of back and forth, until the “assistant” director of finance comes in:

Luckily, the account was suspended before the invoice could be paid. Otherwise, that would’ve been $50,000 out the door.

Techniques
The attacker used a few techniques to almost pull off this scam. One, they took over the account. In the world of SaaS, a username and password is all the hackers need to take over all of your accounts. There is no need to put malware on your endpoint or get in through a Firewall. In fact, there is very little practical security after they have your username and password. The hacker could’ve gotten the information they needed in any number of ways.
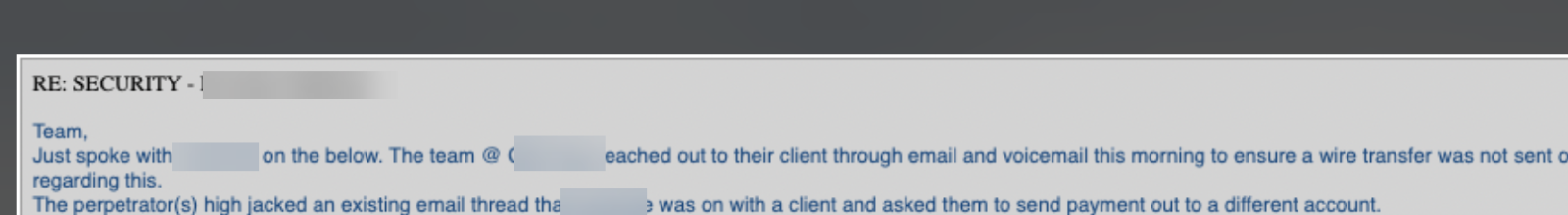
Once they got in, they decided to do what’s called thread hijacking. Essentially, they insert themselves into an already existing thread. That can make it more believable for recipients since it seems like a natural part of the conversation.
Beyond that, the hackers created an inbox rule, whereby all emails sent or received from the account in question were sent to a hidden folder, thereby hiding their tracks. Had they not been alerted about the suspicious rule by their email provider, the $50,000 would’ve gone out the door.
When someone takes over an account via email, they usually do one of the following actions:
- Update bank account info email to payroll
- Hijack existing legitimate conversation related to an invoice and send the attacker’s bank info instead
- Create an inbox rule to hide future emails in a conversation so that the real user is unaware that anything happened
- Create a new payment request from a trusted account to a fake 3rd party service.
Account takeover attacks can cause incredible damage. Not only can they come from anywhere, including email, but they also can lead to massive financial and reputational loss. Whether it's a man-in-the-middle attack when connecting through a shady WiFi, or an end-user that used the same credentials for another account that was then breached, these are incredibly common. Some believe Microsoft and Google already provide some detection of suspicious logins but they generally focus on the web-login itself and not on IMAP/MAPI logins, and hackers have reverse-engineered that security in their lab environment and found ways to avoid its detection. Implementing account takeover in email is key. Another key? Real-time abilities. Finding out that an account was taken over immediately after the malicious login is critical to prevent the hackers from gaining access to what they shouldn't see or using the account as a jump-board to launch additional attacks.
Automation is important because you often don't have time to wait for someone to review every event. It is vital to revoke the hacker's access to the account immediately before any damage is done. In addition to a low false-positive rate, your automated protection should include a method for end-users to manually remediate themselves because if it's not 'self-service' then you are relying on helpdesk calls and have users getting locked out of their accounts. That's where automatic and instantaneous blocking comes into play.
As organizations move their email platform to SaaS-based email like Office 365 and Gmail, account take-over becomes easier for hackers because all it takes is the username and password. It also becomes more valuable because all corporate data resides in the cloud, both in the emails and the other services of the suite such as OneDrive, SharePoint and Google Drive.
Best Practices: Guidance and Recommendations
To guard against these attacks, security professionals can do the following:
- Implement email security that monitors for unusual behavior, such as Superman logins, insecure configurations and more
- Implement security that can automatically block account takeover attacks
- Implement security that uses AI, ML and NLP to understand the intent of a message and when phishing language might be used






