Check Point researchers recently discovered a large-scale phishing campaign in Colombia targeting over 40 prominent companies. The attackers aimed to discreetly install the "Remcos" malware, a sophisticated RAT that gives them complete control over compromised computers. In our report, we explore the attack's complexities and the stealthy techniques used by the malicious actors.
The cybercriminals launched their campaign by sending deceptive emails purportedly from trusted sources, such as well-known financial institutions and established companies operating in Colombia. These malicious emails were meticulously designed to deceive recipients, presenting them with urgent notifications, reports of outstanding debts, and alluring offers.

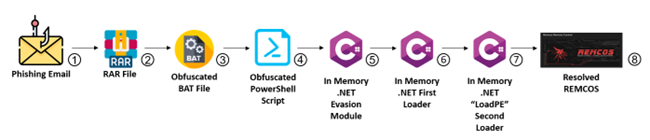
Breaking Down the Attack
- Email Contains an Archive File:
The phishing email includes an attachment disguised as an innocent archive file, such as ZIP, RAR, or TGZ. The attachment is labeled as containing crucial documents, invoices, or other enticing information, enticing recipients to open it.
- Highly Obfuscated BAT File with PowerShell Commands:
Inside the archive file lies a cleverly disguised Batch (BAT) file, concealed with intricate layers of obfuscation. When executed, the BAT file unleashes a series of PowerShell commands, also heavily obfuscated. This complex web of obfuscation poses a significant challenge for security solutions attempting to detect and analyze the malicious payload.
- Loading .NET Modules:
Once the PowerShell commands have been decrypted, they proceed to load two .NET modules directly into the computer's memory. These modules play a vital role in the progression of the attack, enabling the cybercriminals to advance to the next stages seamlessly.
- First .NET Module: Evasion and Unhooking:
The primary objective of the initial .NET module is to elude detection and dismantle any security measures within the targeted system. By circumventing or eliminating security hooks, the attackers significantly enhance the malware's ability to stay hidden and carry out its operations covertly.
- Second .NET Module: Loading “LoadPE” and Remcos:
The second .NET module loads "LoadPE" from file resources. This technique allows the Remcos malware to be loaded directly into computer memory, bypassing traditional antivirus and endpoint security solutions.
- Reflective Loading with “LoadPE”:
The "LoadPE" component allows attackers to directly load the Remcos malware from their resources into memory, enhancing its ability to evade traditional antivirus and security solutions by bypassing file-based detection mechanisms.
- The Final Payload: Remcos – Swiss Army Knife RAT:
Once the Remcos malware has successfully infiltrated the system's memory, the attackers' mission is accomplished. Remcos, a powerful Remote Administration Tool (RAT), bestows the attackers with complete dominance over the compromised system. It functions as a versatile Swiss Army Knife for malicious actors, enabling them to carry out a wide array of nefarious activities such as unauthorized access, data theft, keylogging, remote surveillance, and much more.
Summary
Understanding the attack flow's complexity is crucial for enhancing cybersecurity defenses and devising effective countermeasures against advanced phishing campaigns.
Check Point customers remain protected from the threats described in this research.






